Содержание
- 2. Content 1 2 Map of Risks 4 3 5 Map of Responsibility Basics Principles of Security
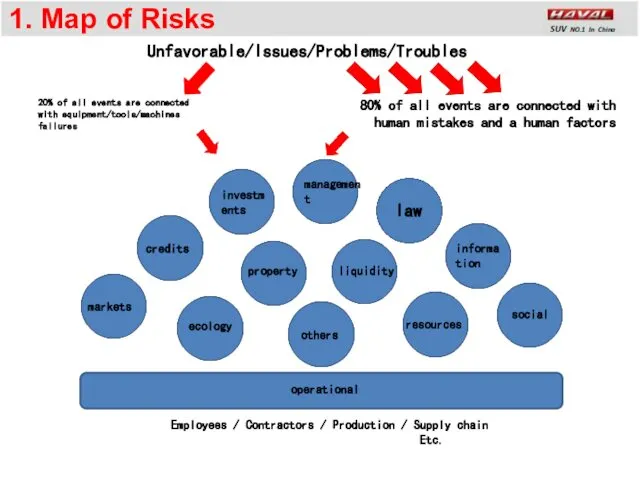
- 3. 1. Map of Risks law ecology social resources informa tion liquidity property Employees / Contractors /
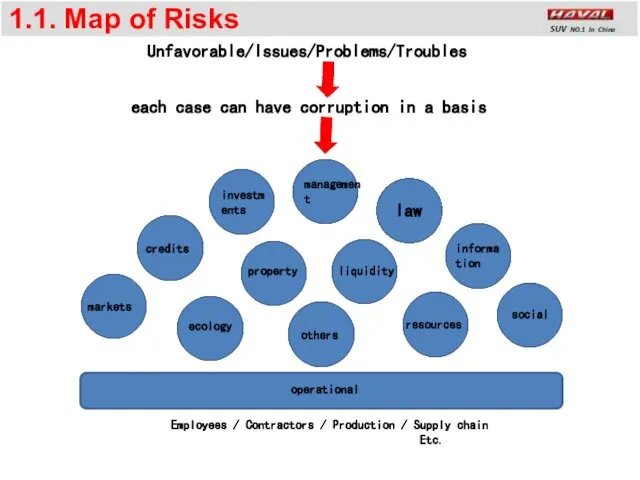
- 4. 1.1. Map of Risks law ecology social resources informa tion liquidity property Employees / Contractors /
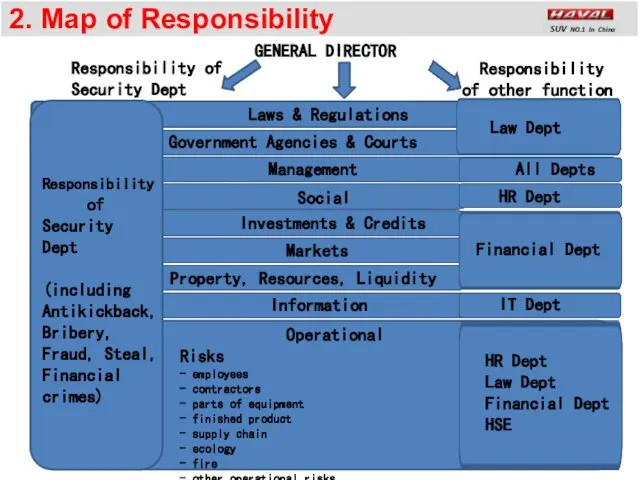
- 5. 2. Map of Responsibility Responsibility of Security Dept Government Agencies & Courts Laws & Regulations Management
- 6. 3. Basic principles of Security Activity If necessary receive and exchange of information with Great Wall
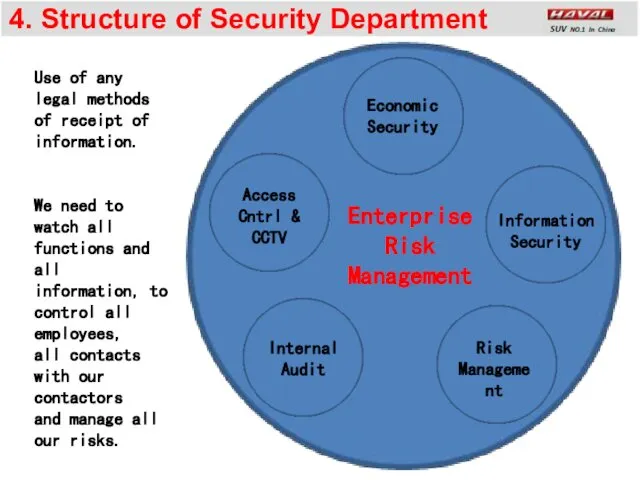
- 7. 4. Structure of Security Department Economic Security Access Cntrl & CCTV Information Security Internal Audit Risk
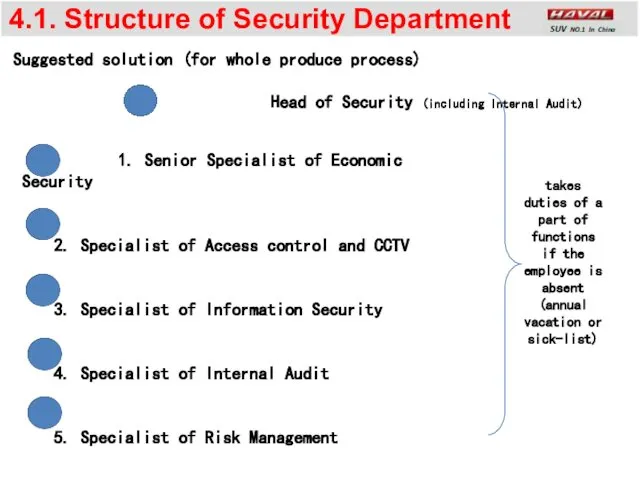
- 8. 4.1. Structure of Security Department Suggested solution (for whole produce process) Head of Security (including Internal
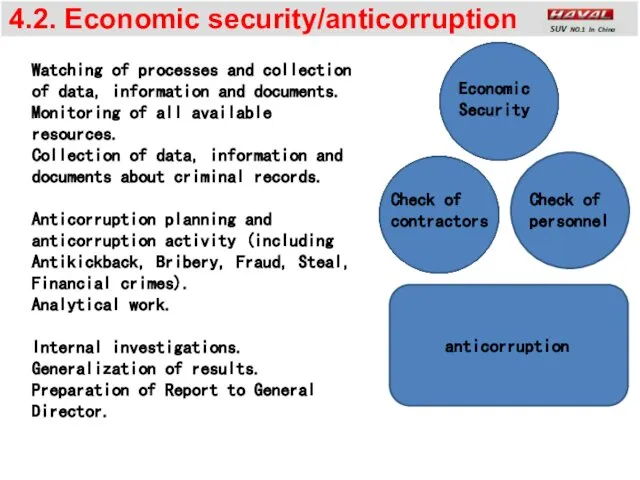
- 9. 4.2. Economic security/anticorruption Check of personnel Check of contractors Watching of processes and collection of data,
- 10. 4.2.1. Economic security/anticorruption Check of personnel Personnel Check of the hired personnel. Collection of data, information
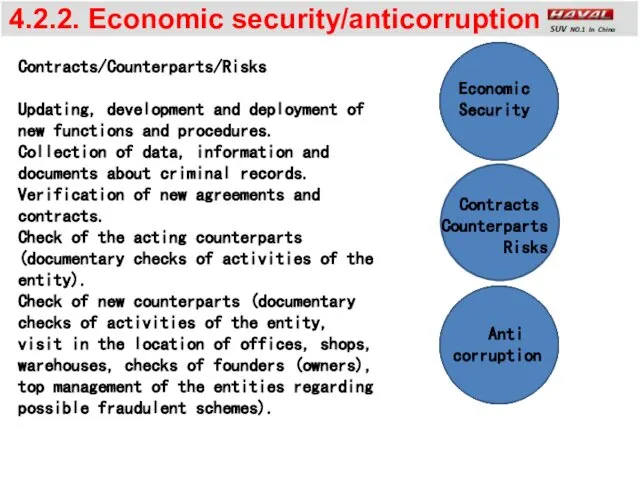
- 11. 4.2.2. Economic security/anticorruption Contracts Counterparts Risks Contracts/Counterparts/Risks Updating, development and deployment of new functions and procedures.
- 12. 4.2.3. Economic security/anticorruption Contracts Counterparts Risks Contracts/Counterparts/Risks Check of new counterparts (documentary checks of activities of
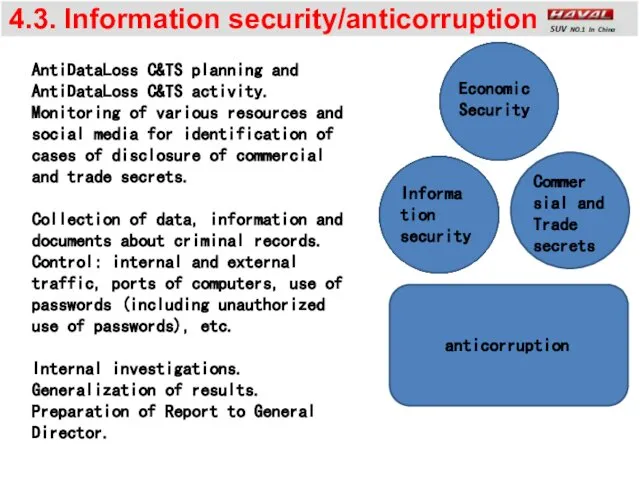
- 13. 4.3. Information security/anticorruption Commer sial and Trade secrets Informa tion security AntiDataLoss C&TS planning and AntiDataLoss
- 14. 4.4. Access control/CCTV CCTV Access control Updating, development and deployment of new functions and procedures Access
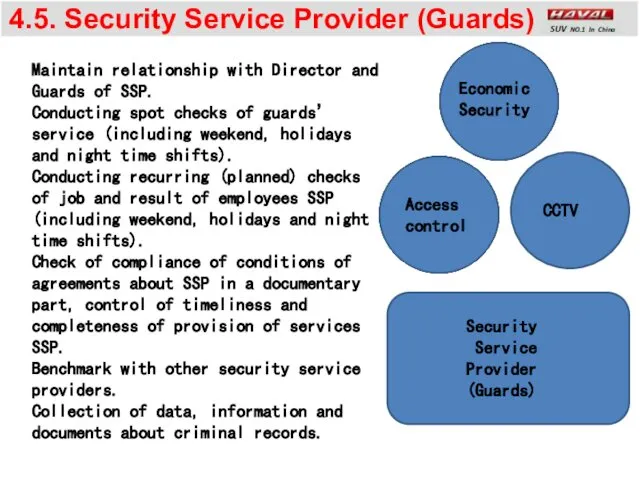
- 15. 4.5. Security Service Provider (Guards) CCTV Access control Maintain relationship with Director and Guards of SSP.
- 16. 4.6.1. Control the incoming and outgoing of goods Staff Devices Procedures Safety and Security of property
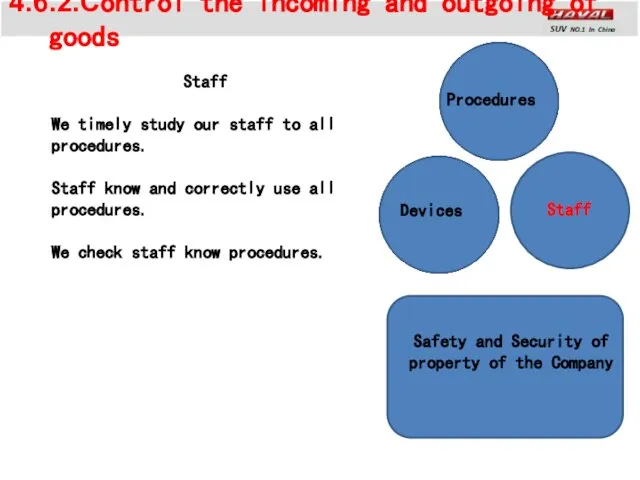
- 17. 4.6.2.Control the incoming and outgoing of goods Staff Devices Procedures Safety and Security of property of
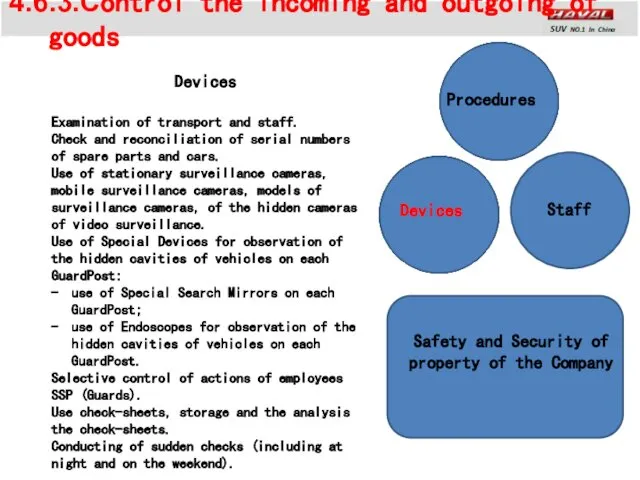
- 18. 4.6.3.Control the incoming and outgoing of goods Staff Devices Procedures Safety and Security of property of
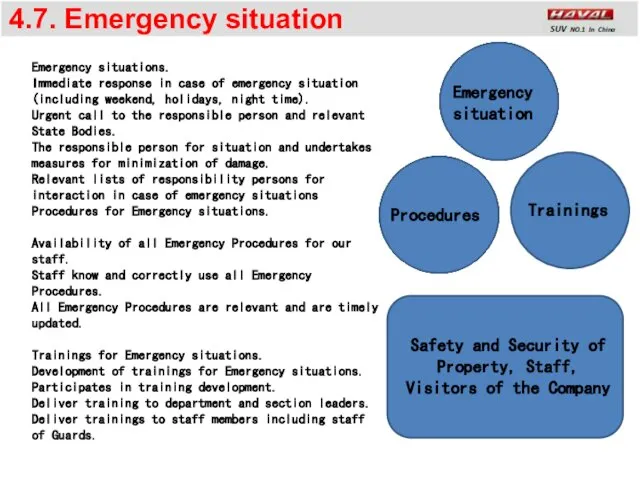
- 19. 4.7. Emergency situation Procedures Trainings Emergency situations. Immediate response in case of emergency situation (including weekend,
- 20. 4.8. Other Security Services Trainings Personal security. Escort of the guests (Top Management of GWM, Government).
- 21. 5. Decision of General Director Approve Don`t approve
- 22. Notice: Laws and Regulations Basic Laws and Regulations (international and local) ISO 26000 Guidance on Social
- 24. Скачать презентацию







 pravila_web-saita
pravila_web-saita Планирование и развертывание серверов с использованием диспетчера виртуальных машин (VMM)
Планирование и развертывание серверов с использованием диспетчера виртуальных машин (VMM) Создание приложений на OC Android
Создание приложений на OC Android Настройка удаленного доступа
Настройка удаленного доступа Издательство Альпина Паблишер
Издательство Альпина Паблишер Базовые основы системной инженерии
Базовые основы системной инженерии Разработка программной системы повышения быстродействия мультикомпьютерных систем
Разработка программной системы повышения быстродействия мультикомпьютерных систем Компьютер как универсальное устройство для работы с информацией
Компьютер как универсальное устройство для работы с информацией Протоколы UDP и TCP
Протоколы UDP и TCP Математическое моделирование
Математическое моделирование Тренинг. Бизнес с Китаем в сети интернет. (Занятие 2)
Тренинг. Бизнес с Китаем в сети интернет. (Занятие 2) Артық кетуді басқару
Артық кетуді басқару Проектирование реляционных баз данных
Проектирование реляционных баз данных Анимация в презентации
Анимация в презентации Электронные библиотеки
Электронные библиотеки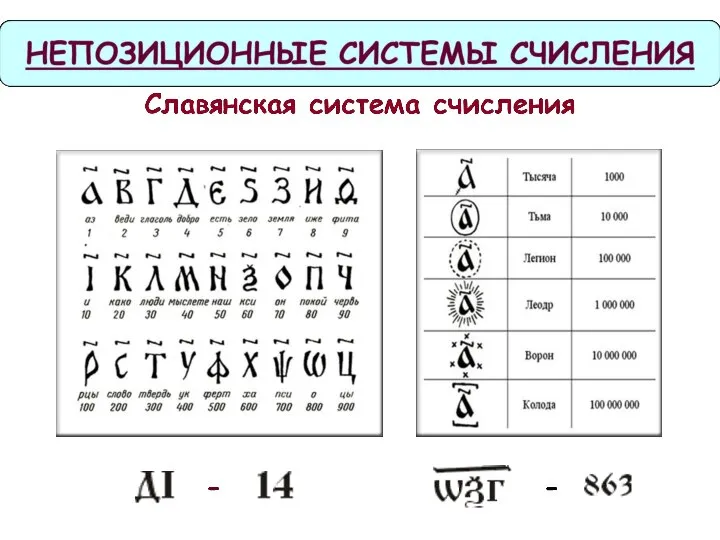 Непозиционные системы счисления
Непозиционные системы счисления Автоматизация чистки
Автоматизация чистки Организация запросов в SQL. Запрос на выборку данных из одной таблицы
Организация запросов в SQL. Запрос на выборку данных из одной таблицы Страна Дождя. Игра
Страна Дождя. Игра Аттестационная работа. Компьютерные игры для младших школьников: вред или польза
Аттестационная работа. Компьютерные игры для младших школьников: вред или польза Социальная инженерия. Тема 7
Социальная инженерия. Тема 7 Возможности программы iTunes
Возможности программы iTunes Тест по информатике
Тест по информатике Кодирование и обработка звуковой информации
Кодирование и обработка звуковой информации Технические средства информационных технологий!
Технические средства информационных технологий! Циклические алгоритмы на Паскале
Циклические алгоритмы на Паскале Свойства систем
Свойства систем Лекция 5. Язык программирования - ассемблер. Логические основы компьютера
Лекция 5. Язык программирования - ассемблер. Логические основы компьютера