Содержание
- 2. CRC Encoding - Recab Multiply i(x) by n-k; (puts n-k zeros in (n-k) low order positions)
- 3. An Example – Step-by-Step
- 4. An Example – Step 1
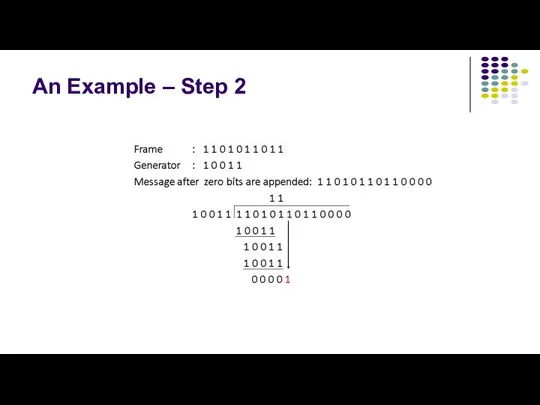
- 5. An Example – Step 2
- 6. An Example – Step 3
- 7. An Example – Step 4
- 8. An Example – Step 5
- 9. An Example – Step 6
- 10. An Example – Step 7
- 11. An Example – Step 8
- 12. An Example – Step 9
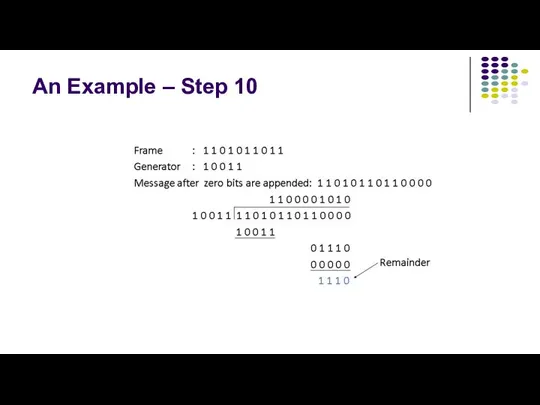
- 13. An Example – Step 10
- 14. Overall
- 15. CRC Capability Analysis What kind of errors will be detected? Imagine that a transmission error e(x)
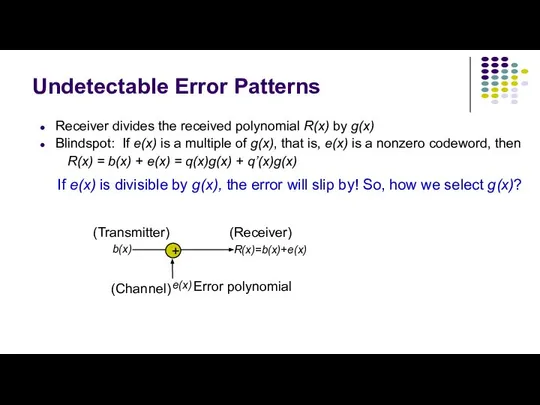
- 16. Undetectable Error Patterns Receiver divides the received polynomial R(x) by g(x) Blindspot: If e(x) is a
- 17. Designing Good Polynomial Codes Select generator polynomial so that likely error patterns are not multiples of
- 18. Designing Good Polynomial codes Detecting Odd Numbers of Errors Suppose all codeword polynomials have an even
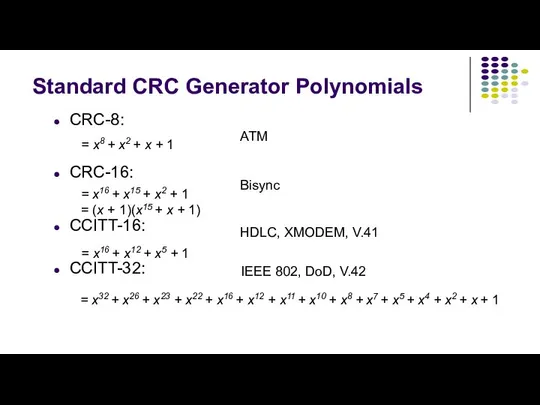
- 19. Standard CRC Generator Polynomials CRC-8: CRC-16: CCITT-16: CCITT-32: HDLC, XMODEM, V.41 IEEE 802, DoD, V.42 Bisync
- 20. Internet Checksum Internet Protocols (IP, TCP, UDP) use check bits to detect errors, instead of using
- 21. Let IP header consists of L, 16-bit words, b0, b1, b2, ..., bL-1 The algorithm appends
- 22. Internet Checksum Example Assume 4-bit words Use mod 24-1 arithmetic b0=1100 = 12 b1=1010 = 10
- 23. Internet Checksum Example Use Modulo Arithmetic Assume 4-bit words Use mod 24-1 arithmetic b0=1100 = 12
- 25. Скачать презентацию

















 Презентация по математике "Галерея великих" - скачать
Презентация по математике "Галерея великих" - скачать  Финансовая математика: банки, вклады, кредиты
Финансовая математика: банки, вклады, кредиты Презентация на тему Выполните задание дроби
Презентация на тему Выполните задание дроби История теории вероятностей. Элементы комбинаторики. Лекция №1
История теории вероятностей. Элементы комбинаторики. Лекция №1 Внеклассное мероприятие по математике: Своя игра
Внеклассное мероприятие по математике: Своя игра Длина ломаной (Урок 25)
Длина ломаной (Урок 25) Геометрический смысл производной
Геометрический смысл производной Применение производной к исследованию функций
Применение производной к исследованию функций Игра по математике для 6 класса «Счастливый случай»
Игра по математике для 6 класса «Счастливый случай» GEOMETRIYa_povtorenie
GEOMETRIYa_povtorenie ОГЭ 2016. Геометрия 9. Решение задач с развернутым ответом
ОГЭ 2016. Геометрия 9. Решение задач с развернутым ответом Подготовка к ГИА. Нахождение знаков коэффициентов квадратичной функции по графику
Подготовка к ГИА. Нахождение знаков коэффициентов квадратичной функции по графику Изображение пространственных фигур Мячина Екатерина Колдаева Есения 11 Г класс
Изображение пространственных фигур Мячина Екатерина Колдаева Есения 11 Г класс  Математическое кафе
Математическое кафе Система подготовки обучающихся к ГИА и ЕГЭ с начальной школы.
Система подготовки обучающихся к ГИА и ЕГЭ с начальной школы.  Интерактивный плакат "Треугольник"
Интерактивный плакат "Треугольник" Начальные геометрические сведения. Диктант 7 класс
Начальные геометрические сведения. Диктант 7 класс Основное свойство дроби. Сокращение дробей
Основное свойство дроби. Сокращение дробей Бесконечный мир чисел Выполнили: Ибрагимова Марина, ученица 9 класса МОУ СОШ №34 г. Волжского Волгоградской области. Чалышева Ксен
Бесконечный мир чисел Выполнили: Ибрагимова Марина, ученица 9 класса МОУ СОШ №34 г. Волжского Волгоградской области. Чалышева Ксен Решение заданий №6 (прямоугольник) по материалам открытого банка задач ЕГЭ по математике 2016 года
Решение заданий №6 (прямоугольник) по материалам открытого банка задач ЕГЭ по математике 2016 года Погрешность и точность приближения. Абсолютная и относительная погрешности
Погрешность и точность приближения. Абсолютная и относительная погрешности Практическое задание №2
Практическое задание №2 Арифметика Магницкого
Арифметика Магницкого Аттестационная работа. Организация познавательной деятельности школьников через систему внеклассной работы по математике
Аттестационная работа. Организация познавательной деятельности школьников через систему внеклассной работы по математике Путешествие в страну Арифметика. Выполнила Учитель математики МОУ «ООШ»с.Трубетчино Данилушкина З.А.
Путешествие в страну Арифметика. Выполнила Учитель математики МОУ «ООШ»с.Трубетчино Данилушкина З.А. Её величество Степень
Её величество Степень Презентация по математике "Проценты" - скачать бесплатно_
Презентация по математике "Проценты" - скачать бесплатно_ Графи. Основні поняття і визначення
Графи. Основні поняття і визначення