Содержание
- 2. Cyber Preparedness
- 3. Cyber Preparedness
- 4. Technology? Security team? Processes? Where Does Cyber Preparedness Begin?
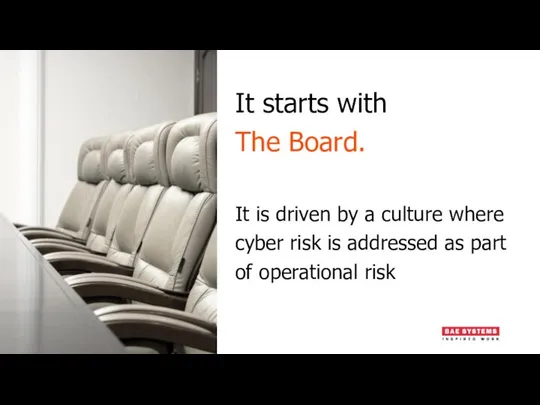
- 5. It starts with The Board. It is driven by a culture where cyber risk is addressed
- 6. Why Should They Care?
- 7. The Obvious
- 8. Reducing Risk. Enables Growth.
- 9. Cyber Preparedness
- 10. Fire started in a NJ home last year A driver saw the fire and banged on
- 11. Effective Smoke Detection Consider where you replace them Ensure the batteries work Monitor and maintain
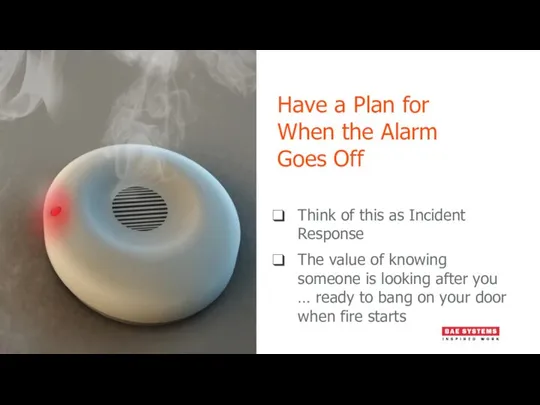
- 12. Have a Plan for When the Alarm Goes Off Think of this as Incident Response The
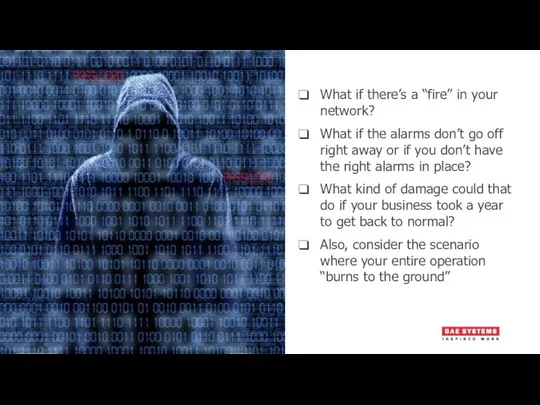
- 13. What if there’s a “fire” in your network? What if the alarms don’t go off right
- 14. Hierarchy of Security Needs To be fully prepared and avoid disasters: Detect new, hidden threats Effectively
- 15. Prevention: Still Important
- 16. Balancing Spend Allocations Prevention Detection Response
- 17. detect the incident. The ability to respond to an incident is only as good as an
- 18. Detection Too many bad guys/attacks Bad guys don’t want to be found Attacks take new forms
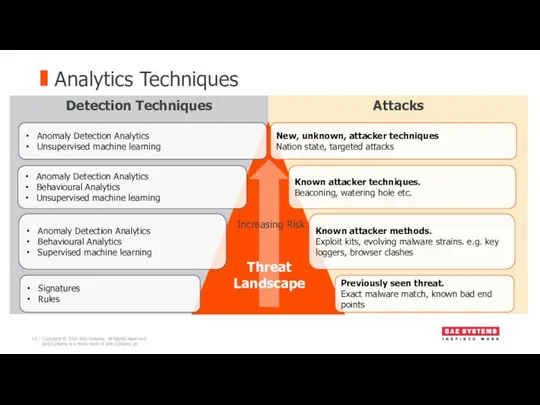
- 19. Analytics Techniques Attacks Detection Techniques Anomaly Detection Analytics Unsupervised machine learning Anomaly Detection Analytics Behavioural Analytics
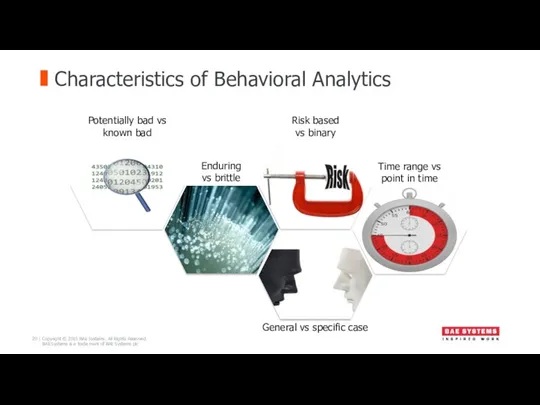
- 20. Characteristics of Behavioral Analytics
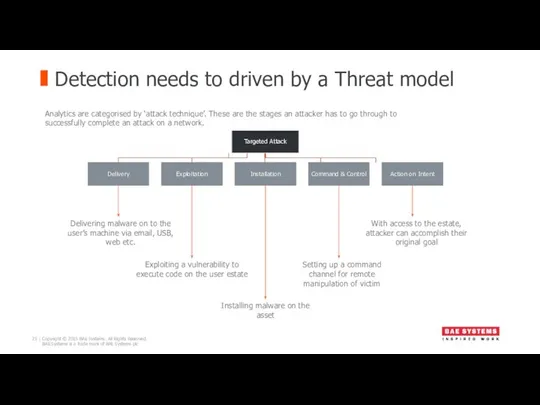
- 21. Detection needs to driven by a Threat model Delivering malware on to the user’s machine via
- 22. Cyber Preparedness
- 23. Response
- 24. Having proper analysis capabilities requires both trained personnel and the proper tools to perform the analysis.
- 25. A PLAN vs A FRAMEWORK "No plan of operations extends with certainty beyond the first encounter
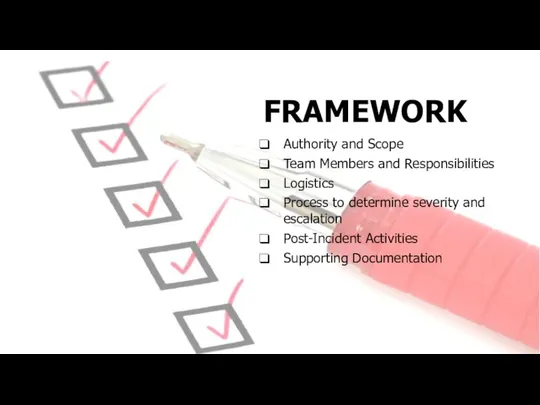
- 26. FRAMEWORK Authority and Scope Team Members and Responsibilities Logistics Process to determine severity and escalation Post-Incident
- 27. The most critical component in any Incident Response Practice … Authority and backing from executive management.
- 28. IR Team Primary team Extended team Third parties
- 29. Primary Security Team IR Lead Operations Team Service Desk Team
- 30. Extended Executives Legal Communications Human Resources Compliance Physical Security
- 31. 3rd Parties Outsourced IT (help desk, server support) Forensic Firms ISPs Legal Counsel Law Enforcement Public
- 32. LOGISTICS E-Mail Distro / Call bridge for communication War Room Computing equipment Evidence Locker Often overlooked
- 33. Testing Incident Response High Level Audit Objective Based Assessment Table top Exercise War Game
- 34. Cyber Preparedness – Key Takeaways
- 35. Thank You
- 36. Q&A
- 37. BAE Systems Surrey Research Park Guildford Surrey GU2 7YP United Kingdom T: +44 (0)1483 816000 F:
- 39. Скачать презентацию




















 Литосферные опасности
Литосферные опасности ЧС природного характера
ЧС природного характера Государственное управление в чрезвычайных ситуациях
Государственное управление в чрезвычайных ситуациях Основные инфекционные заболевания, их классификация и профилактика
Основные инфекционные заболевания, их классификация и профилактика Назначение костра. Виды костров
Назначение костра. Виды костров Допуск транспортных средств к эксплуатации !
Допуск транспортных средств к эксплуатации ! Нашақорлық – қоғамдық дерт
Нашақорлық – қоғамдық дерт Выход и выезд на лёд водных объектов вне ледовых переправ и переходов опасен
Выход и выезд на лёд водных объектов вне ледовых переправ и переходов опасен Влияние табакокурения на сердечнососудистую систему. Влияние никотина на организм
Влияние табакокурения на сердечнососудистую систему. Влияние никотина на организм Здоровый образ жизни
Здоровый образ жизни Коридор безопасности
Коридор безопасности Выбор овощей и фруктов. Их польза и вред
Выбор овощей и фруктов. Их польза и вред Функции и предупреждающие знаки дорожного движения
Функции и предупреждающие знаки дорожного движения Запомнить твердо нужно нам: пожар не возникает сам!
Запомнить твердо нужно нам: пожар не возникает сам! Аварийно - спасательные и другие неотложные работы
Аварийно - спасательные и другие неотложные работы Дорожные знаки. Информационные знаки. (Тема 3.6)
Дорожные знаки. Информационные знаки. (Тема 3.6) Наркомания и токсикомания. Профилактика вредных привычек
Наркомания и токсикомания. Профилактика вредных привычек Сигналы светофора
Сигналы светофора Режим дня – залог здоровья
Режим дня – залог здоровья Улучшение экологической чистоты производства
Улучшение экологической чистоты производства Безопасное проведение массовых взрывов на земной поверхности
Безопасное проведение массовых взрывов на земной поверхности Организация ЭПП в зоне ЧС
Организация ЭПП в зоне ЧС Основы радиосвязи и её организации при проведении поисково-спасательных работ
Основы радиосвязи и её организации при проведении поисково-спасательных работ «Секреты правильного питания» для учащихся 1-4 классов
«Секреты правильного питания» для учащихся 1-4 классов Ғылыми жоба сағыз
Ғылыми жоба сағыз Введение для штатных сотрудников и подрядчиков
Введение для штатных сотрудников и подрядчиков Балалар мекемелеріндегі санитарлықтехникалық жабдықтарға қойылатын гигиеналық талаптар
Балалар мекемелеріндегі санитарлықтехникалық жабдықтарға қойылатын гигиеналық талаптар Принципы безопасности жизнедеятельности
Принципы безопасности жизнедеятельности