Содержание
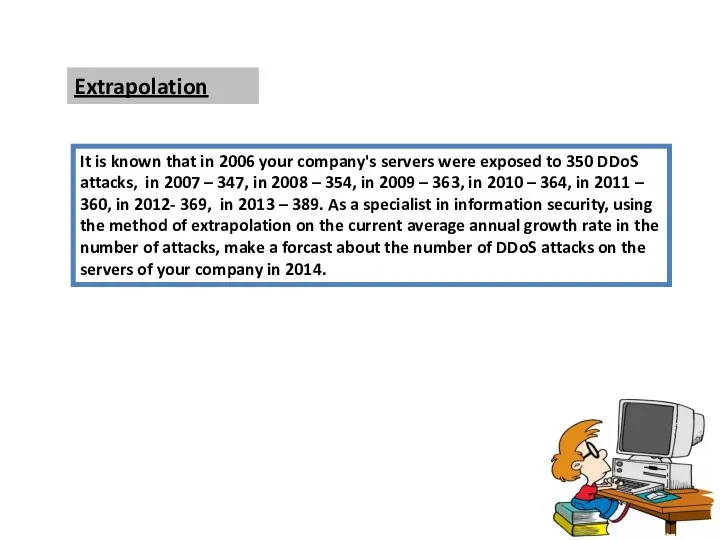
- 2. Extrapolation It is known that in 2006 your company's servers were exposed to 350 DDoS attacks,
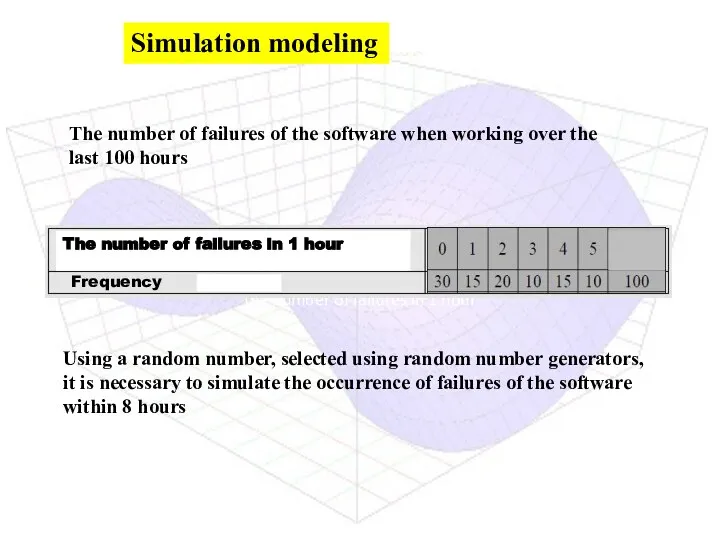
- 3. the number of failures in 1 hour The number of failures of the software when working
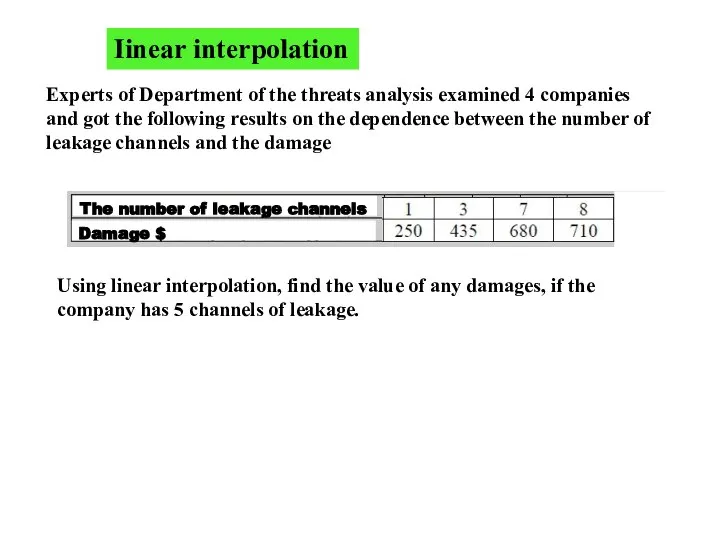
- 4. Iinear interpolation Experts of Department of the threats analysis examined 4 companies and got the following
- 5. EXPONENTIAL SMOOTHING The number of confidential information leakage from the public authorities of the region for
- 6. EVALUATION OF THE FORECAST RELIABILITY You must provide the CEO report on the reliability of forecasts
- 7. Calculate the average and marginal product of the company, using the following data: When the decreasing
- 9. Скачать презентацию



 Методы экономического анализа
Методы экономического анализа Халқаралық экономикалық қатынастар. Сыртқы экономикалық қызметті реттеу
Халқаралық экономикалық қатынастар. Сыртқы экономикалық қызметті реттеу Функции денег
Функции денег Сущность жилищно-коммунального хозяйства, структура управления. (Тема 1)
Сущность жилищно-коммунального хозяйства, структура управления. (Тема 1) Презентация Повышение конкурентоспособности предприятия
Презентация Повышение конкурентоспособности предприятия «Транспортные риски во ВЭД: классификация, оценка и методы минимизации»
«Транспортные риски во ВЭД: классификация, оценка и методы минимизации» Внеоборотный капитал предприятия
Внеоборотный капитал предприятия Эластичность спроса и предложения
Эластичность спроса и предложения Экономический рост и развитие
Экономический рост и развитие Типы экономических систем
Типы экономических систем Медународные налоговые отношения. (Лекция 5)
Медународные налоговые отношения. (Лекция 5) Облік у зарубіжних кранах
Облік у зарубіжних кранах Историография ЭИЗС и подходы к периодизации истории глобальной экономики. (Лекция 3)
Историография ЭИЗС и подходы к периодизации истории глобальной экономики. (Лекция 3) Индустриальный инжиниринг в Германии
Индустриальный инжиниринг в Германии Применение имитационного моделирования в экономике
Применение имитационного моделирования в экономике Учет инфляции и оценка инвестиционных рисков и ликвидности инвестиций
Учет инфляции и оценка инвестиционных рисков и ликвидности инвестиций Хозяйство страны (экономика)
Хозяйство страны (экономика) Рынки факторов производства
Рынки факторов производства Статистический анализ отдельных стран в мировом импорте
Статистический анализ отдельных стран в мировом импорте Моделирование социально-экономических процессов
Моделирование социально-экономических процессов Экономическая сущность предпринимательской деятельности. (Тема 1)
Экономическая сущность предпринимательской деятельности. (Тема 1) Митна політика україни. Сучасність і перспективи розвитку
Митна політика україни. Сучасність і перспективи розвитку Россия в процессах международной миграции рабочей силы
Россия в процессах международной миграции рабочей силы Оценка результатов финансово-хозяйственной деятельности ОАО «Атмис-Сахар»
Оценка результатов финансово-хозяйственной деятельности ОАО «Атмис-Сахар» Мероприятия по организации функционирования земли как комплексного объекта жизнедеятельности общества (2)
Мероприятия по организации функционирования земли как комплексного объекта жизнедеятельности общества (2) Финансово-экономическая оценка инвестиционного промышленного проекта
Финансово-экономическая оценка инвестиционного промышленного проекта Экономика, ее роль в жизни общества
Экономика, ее роль в жизни общества Понятие и классификация рядов динамики. (Занятие 9)
Понятие и классификация рядов динамики. (Занятие 9)