Содержание
- 2. Chapter 6 Other Security Building Blocks Motivation for Secret Splitting A professor, Carol, encrypts her
- 3. Chapter 6 Other Security Building Blocks Secret Splitting Secret splitting makes it possible to divide
- 4. Chapter 6 Other Security Building Blocks Secret Splitting Using One-Time Pads M = “THEKEYISTHREE” Create
- 5. Chapter 6 Other Security Building Blocks Secret Split. with One-Time Pads Encrypt C1 with P2:
- 6. Chapter 6 Other Security Building Blocks Secret Sharing Secret sharing (also called a threshold scheme)
- 7. Chapter 6 Other Security Building Blocks Motivation for Blind Sig’s Dave owns a bank Carol
- 8. Chapter 6 Other Security Building Blocks Blind Signatures Blind signatures enable a user to digitally
- 9. Chapter 6 Other Security Building Blocks Blind Signatures (cont) Carol blinds the message: B =
- 10. Chapter 6 Other Security Building Blocks Blind Signatures (cont) Dave signs the blinded message as
- 11. Chapter 6 Other Security Building Blocks Blind Signatures (cont) Carol unblinds the signed blinded message
- 12. Chapter 6 Other Security Building Blocks Properties of Blind Signatures Validity – as with normal
- 13. Chapter 6 Other Security Building Blocks Unlinkability of Blind Signatures Suppose: Carol gives Dave two
- 14. Chapter 6 Other Security Building Blocks Example of Unlinkability Carol gives Dave two blinded documents
- 15. Chapter 6 Other Security Building Blocks Example of Unlinkability (cont) To link an unblinded document
- 16. Chapter 6 Other Security Building Blocks Motivation for Blind Signatures (cont) Why would Dave sign
- 17. Chapter 6 Other Security Building Blocks Digital Money Without Blind Sig’s Carol creates a message
- 18. Chapter 6 Other Security Building Blocks Digital Money With Blind Signatures Carol creates a message
- 19. Chapter 6 Other Security Building Blocks Digital Money With Blind Signatures (cont) Problem #1: double
- 20. Chapter 6 Other Security Building Blocks Digital Money With Blind Signatures (cont) Problem #2: fraud
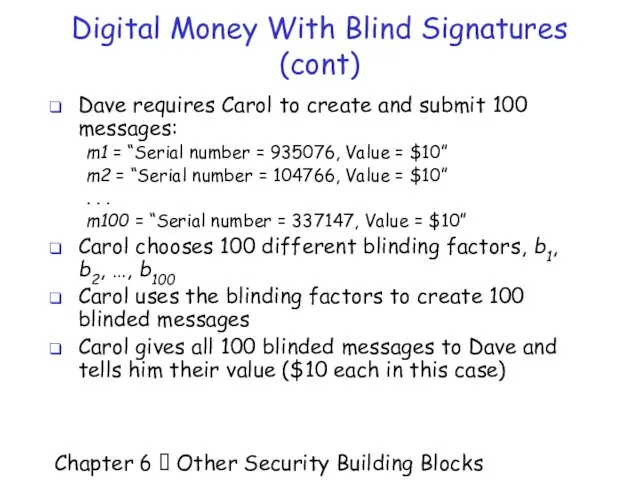
- 21. Chapter 6 Other Security Building Blocks Digital Money With Blind Signatures (cont) Dave requires Carol
- 22. Chapter 6 Other Security Building Blocks Digital Money With Blind Signatures (cont) Dave chooses 99
- 23. Chapter 6 Other Security Building Blocks Digital Money With Blind Signatures (cont) For Carol to
- 24. Chapter 6 Other Security Building Blocks Motivation for Bit Commitment Might want to commit to
- 25. Chapter 6 Other Security Building Blocks Motivation for Bit Commitment (cont) Chuck and Bill’s virtual
- 26. Chapter 6 Other Security Building Blocks Bit Commitment Bit commitment allows someone to commit to
- 27. Chapter 6 Other Security Building Blocks Bit Commitment Using a Symmetric-Key Cryptosystem Commitment phase: Chuck
- 28. Chapter 6 Other Security Building Blocks Bit Commitment Using a Symmetric-Key Cryptosystem Commitment phase: Bill
- 29. Chapter 6 Other Security Building Blocks Bit Commitment Using a Symmetric-Key Cryptosystem Neither can cheat:
- 30. Chapter 6 Other Security Building Blocks Bit Commitment Using a One-Way Hash Function Commitment phase:
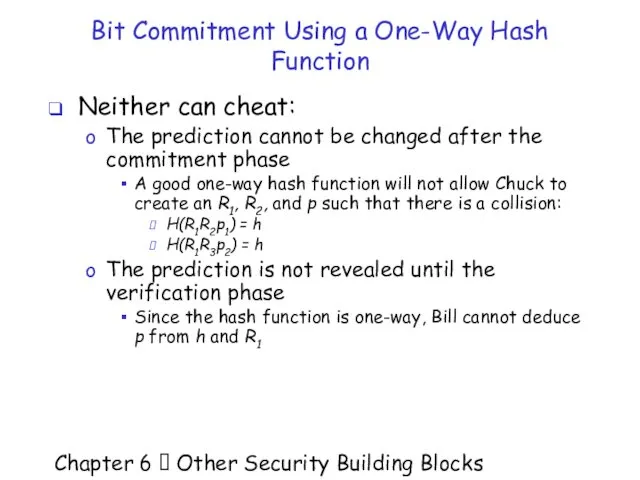
- 31. Chapter 6 Other Security Building Blocks Bit Commitment Using a One-Way Hash Function Neither can
- 32. Chapter 6 Other Security Building Blocks Cryptographic Protocols A protocol is an agreed-upon sequence of
- 33. Chapter 6 Other Security Building Blocks Key Exchange with Symmetric Cryptography Assume Alice and Bob
- 34. Chapter 6 Other Security Building Blocks Key Exchange with Symmetric Cryptography (cont) Agreeing on a
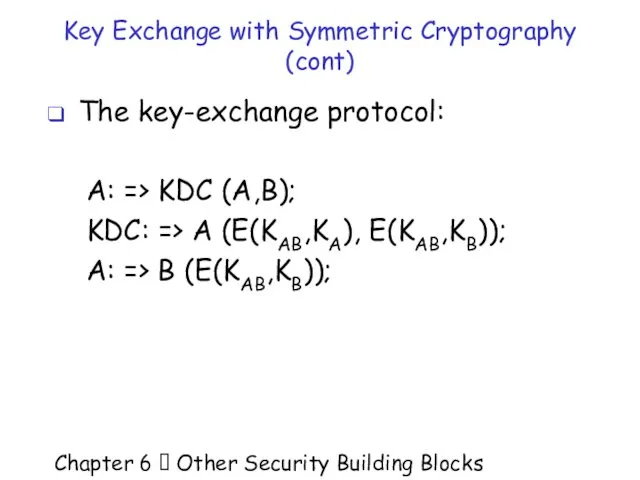
- 35. Chapter 6 Other Security Building Blocks Key Exchange with Symmetric Cryptography (cont) The key-exchange protocol:
- 36. Chapter 6 Other Security Building Blocks Key Exchange with Symmetric Cryptography (cont) Issues: Security depends
- 37. Chapter 6 Other Security Building Blocks Attacking the Protocol Alice and Bob set up a
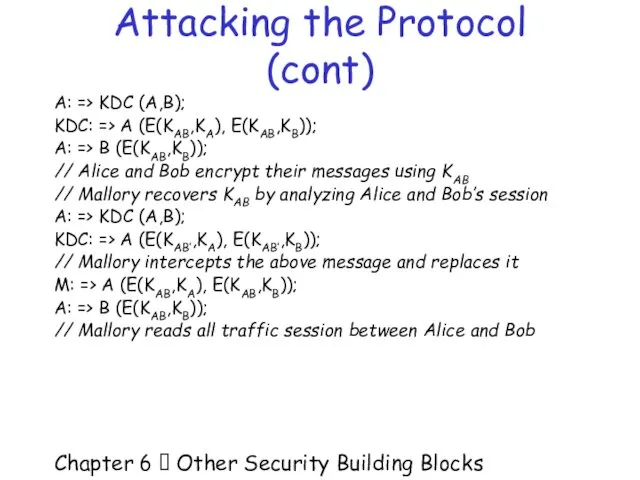
- 38. Chapter 6 Other Security Building Blocks Attacking the Protocol (cont) A: => KDC (A,B); KDC:
- 39. Chapter 6 Other Security Building Blocks What Went Wrong? Alice and Bob need to be
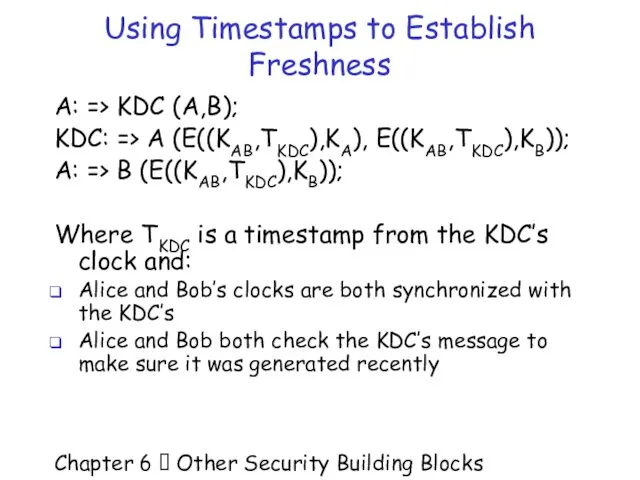
- 40. Chapter 6 Other Security Building Blocks Using Timestamps to Establish Freshness A: => KDC (A,B);
- 41. Chapter 6 Other Security Building Blocks Using Nonces to Establish Freshness A nonce is a
- 42. Chapter 6 Other Security Building Blocks Key-Exchange with Public-Key Cryptography Alice learns Bob’s public key
- 43. Chapter 6 Other Security Building Blocks Attacking the Protocol Recall the man-in-the-middle attack If Mallory
- 44. Chapter 6 Other Security Building Blocks The Interlock Protocol Combating the man-in-the-middle attack: Alice and
- 45. Chapter 6 Other Security Building Blocks The Interlock Prot. (cont) Foiling the man-in-the-middle: Assume Mallory
- 46. Chapter 6 Other Security Building Blocks Authentication Authentication is the process of proving your identity
- 47. Chapter 6 Other Security Building Blocks One-way Authentication Using Symmetric-Key Cryptography Assume that Alice and
- 48. Chapter 6 Other Security Building Blocks One-way Authentication Using Symmetric-Key Cryptography Problem: an adversary, Mallory,
- 49. Chapter 6 Other Security Building Blocks One-way Authentication Using Public-Key Cryptography Alice sends a nonce
- 50. Chapter 6 Other Security Building Blocks One-way Authentication Using Public-Key Cryptography Another challenge-and-response authentication protocol:
- 51. Chapter 6 Other Security Building Blocks Authentication and Key-Exchange Protocols Combine authentication and key-exchange Assume
- 52. Chapter 6 Other Security Building Blocks Authentication and Key-Exchange Protocols Wide-Mouth Frog C: => S(C,Encrypt((D,KCD,TC),KCS));
- 53. Chapter 6 Other Security Building Blocks Authentication and Key-Exchange Protocols Yahalom C => D (C,NC);
- 54. Chapter 6 Other Security Building Blocks Authentication and Key-Exchange Protocols Denning and Sacco (public-key) Carla
- 55. Chapter 6 Other Security Building Blocks Authentication and Key-Exchange Protocols A weakness of the Denning
- 56. Chapter 6 Other Security Building Blocks Authentication and Key-Exchange Protocols Fixing the Denning and Sacco
- 57. Chapter 6 Other Security Building Blocks Motivation for Zero Knowledge Proofs Many challenge and response
- 58. Chapter 6 Other Security Building Blocks Zero-Knowledge Proofs Alice can perform a zero-knowledge proof so
- 59. Chapter 6 Other Security Building Blocks Zero-Knowledge Proofs (cont) Bob asks Alice up to n
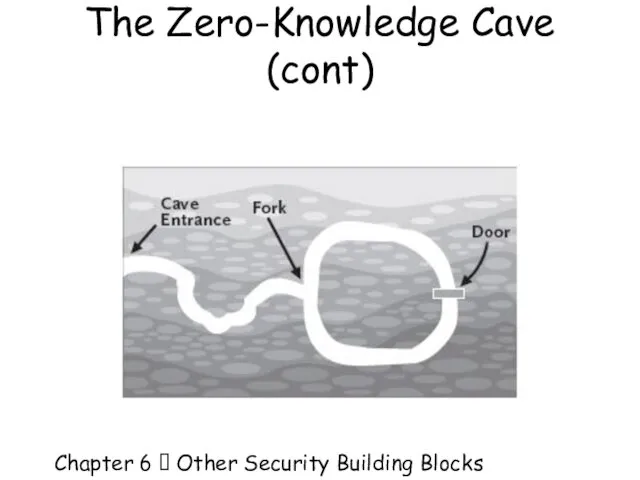
- 60. Chapter 6 Other Security Building Blocks The Zero-Knowledge Cave A cave with a single entrance
- 61. Chapter 6 Other Security Building Blocks The Zero-Knowledge Cave (cont)
- 62. Chapter 6 Other Security Building Blocks The Zero-Knowledge Cave (cont) Alice can prove to Bob
- 63. Chapter 6 Other Security Building Blocks The Zero-Knowledge Cave There are four possiblities: (1) Alice
- 64. Chapter 6 Other Security Building Blocks The Zero-Knowledge Cave (cont) No matter how many times
- 65. Chapter 6 Other Security Building Blocks Mathematical Background - Graph Isomorphism A graph is a
- 66. Chapter 6 Other Security Building Blocks Graph Isomorphism Graphs (I) and (II) are isomorphic: (I)
- 67. Chapter 6 Other Security Building Blocks Graph Isomorphism (cont) Graphs (II) and (III) are isomorphic:
- 68. Chapter 6 Other Security Building Blocks Graph Isomorphism (cont) Graphs (I) and (III) must be
- 69. Chapter 6 Other Security Building Blocks Graph Isomorphism is a Hard Problem In general, determining
- 70. Chapter 6 Other Security Building Blocks A Zero-Knowledge Proof Using Graph Isomorphism Alice creates two
- 71. Chapter 6 Other Security Building Blocks Zero-Knowledge Proof Using Graph Isomorphism Alice randomly permutes G1
- 72. Chapter 6 Other Security Building Blocks Zero-Knowledge Proof Using Graph Isomorphism Alice and Bob repeat
- 73. Chapter 6 Other Security Building Blocks Zero-Knowledge Proof Using Graph Isomorphism Without knowing the isomorphism
- 74. Chapter 6 Other Security Building Blocks Zero-Knowledge Proof Using Graph Isomorphism Alice only sends one
- 75. Chapter 6 Other Security Building Blocks Zero-Knowledge Proof Using Graph Isomorphism If Alice is able
- 76. Chapter 6 Other Security Building Blocks Problem With Zero-Knowledge Proofs Remember the man-in-the-middle attack? Carol
- 78. Скачать презентацию




































































 Структура программы. Запуск программ из командной строки
Структура программы. Запуск программ из командной строки Исследовательская работа по цветовым системам
Исследовательская работа по цветовым системам Методика навчання інформатики. (Лекция 2)
Методика навчання інформатики. (Лекция 2) Метод группировки данных. Закон нормального распределения
Метод группировки данных. Закон нормального распределения Типы модулей в Delphi
Типы модулей в Delphi Software development methodologies
Software development methodologies Typografické zásady
Typografické zásady Эффективность новой экономики
Эффективность новой экономики Компьютерные сети. Адресация
Компьютерные сети. Адресация Задание участникам в рамках запроса предложений на разработку, наполнение и производство корпоративного журнала МТС Запросто
Задание участникам в рамках запроса предложений на разработку, наполнение и производство корпоративного журнала МТС Запросто Структура программы Презентация к уроку информатики в 8 классе общеобразовательной школы Учитель Черногорец Л.В. МОУ СОШ № 14 Кра
Структура программы Презентация к уроку информатики в 8 классе общеобразовательной школы Учитель Черногорец Л.В. МОУ СОШ № 14 Кра Требования к разработке приложения на платформе 1С: Предприятие 8.3
Требования к разработке приложения на платформе 1С: Предприятие 8.3 Хранение, поиск и сортировка информации Базы данных и системы управления базами данных(СУБД)
Хранение, поиск и сортировка информации Базы данных и системы управления базами данных(СУБД) Триггеры в презентации. Создание слайдов с триггерами
Триггеры в презентации. Создание слайдов с триггерами Все меры поддержки в твоем мобильном телефоне. Памятка ЕДВ от 3 до 7
Все меры поддержки в твоем мобильном телефоне. Памятка ЕДВ от 3 до 7 Информационные ресурсы 08/09/15
Информационные ресурсы 08/09/15  Разработка системы сбора и единого центра хранения информации, раскрываемой эмитентами в сети интернет
Разработка системы сбора и единого центра хранения информации, раскрываемой эмитентами в сети интернет База данных как модель предметной области. Моделирование и формализация
База данных как модель предметной области. Моделирование и формализация Программирование алгоритмов на языке Python
Программирование алгоритмов на языке Python Основные виды и приемы хакерских атак
Основные виды и приемы хакерских атак Узнай ИНН через интернет
Узнай ИНН через интернет урок 27_6кл_лин_алгПР11_лин_през
урок 27_6кл_лин_алгПР11_лин_през Интерактивные методы для online-занятий (Рулиене Л.Н. ruliene@bsu.ru, www.ruliene.bsu.ru)
Интерактивные методы для online-занятий (Рулиене Л.Н. ruliene@bsu.ru, www.ruliene.bsu.ru) Результаты контент-анализа транслирования образа Беларуси в российском СМИ
Результаты контент-анализа транслирования образа Беларуси в российском СМИ Индивидуальная работа
Индивидуальная работа Логическое проектирование БД. Лекция 4
Логическое проектирование БД. Лекция 4 Сервисы сети Интернет
Сервисы сети Интернет Компьютерные сети. 11 класс
Компьютерные сети. 11 класс