Содержание
- 3. Biometrics
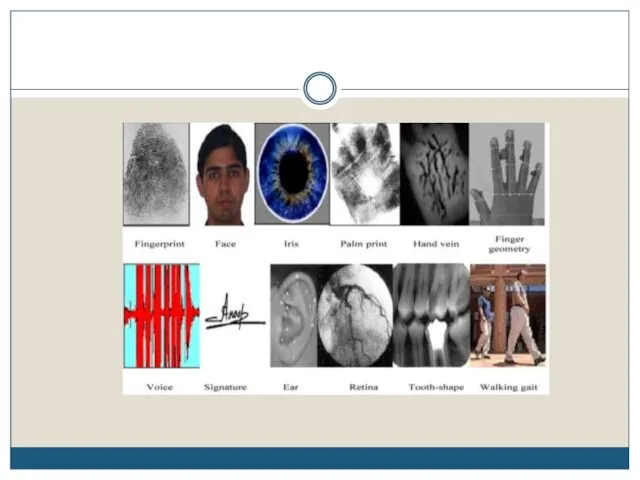
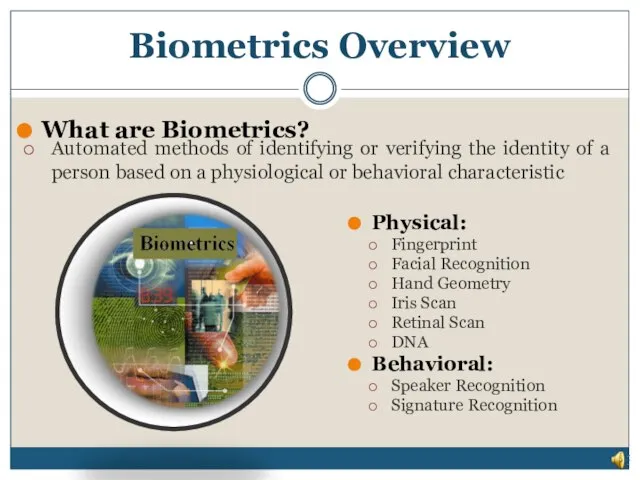
- 4. Biometrics Overview Automated methods of identifying or verifying the identity of a person based on a
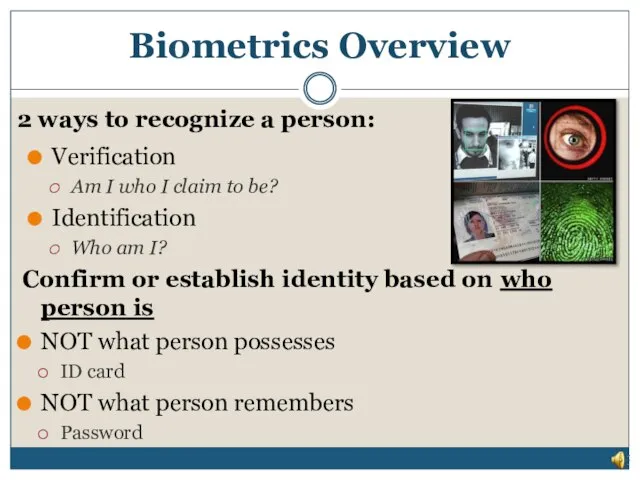
- 5. Biometrics Overview Verification Am I who I claim to be? Identification Who am I? Confirm or
- 6. Fingerprint Fingerprint Pattern Analysis Typical System: fingerprint scanner maps the series of whorls, ridges, furrows and
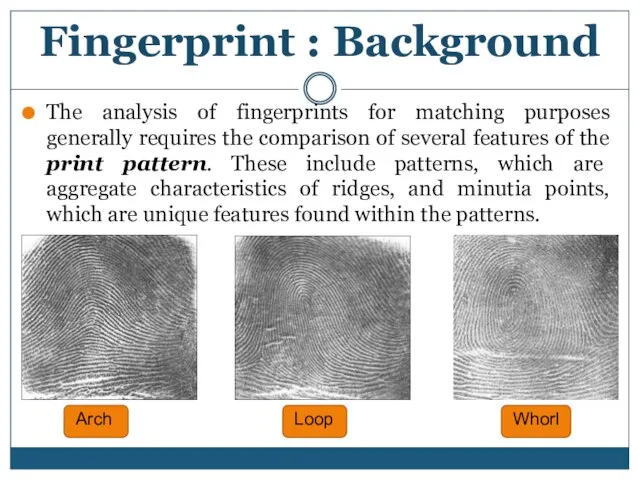
- 7. The analysis of fingerprints for matching purposes generally requires the comparison of several features of the
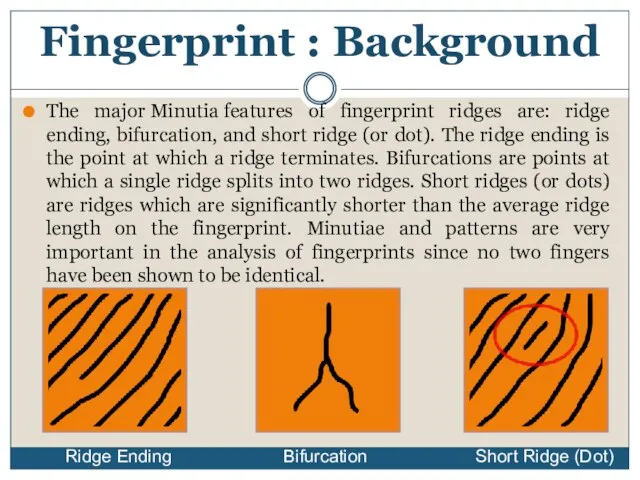
- 8. The major Minutia features of fingerprint ridges are: ridge ending, bifurcation, and short ridge (or dot).
- 9. Facial Recognition Face characteristics analysis Typical system: digital video camera input of a person’s face images
- 10. Facial Recognition : Techniques Traditional Some facial recognition algorithms identify facial features by extracting landmarks, or
- 11. Hand Geometry Hand shape analysis and measurement Typical system: scanners with guidance pegs that position the
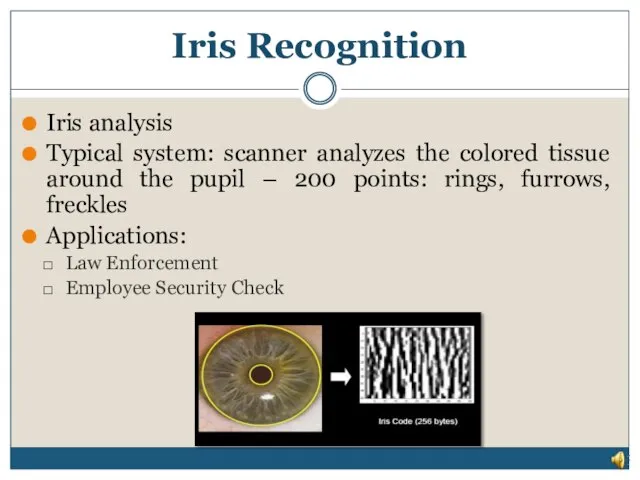
- 12. Iris Recognition Iris analysis Typical system: scanner analyzes the colored tissue around the pupil – 200
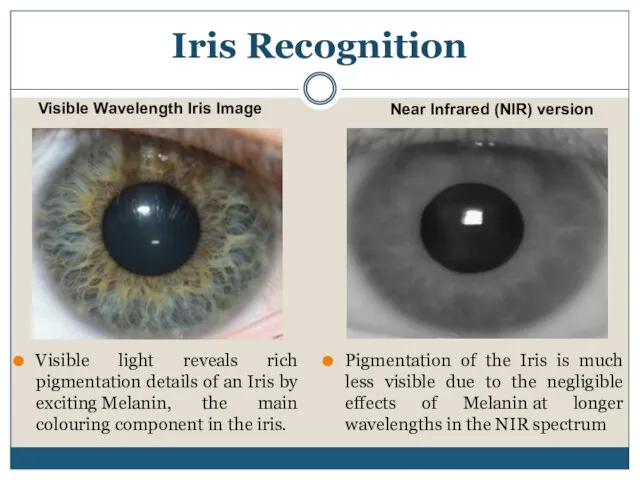
- 13. Visible light reveals rich pigmentation details of an Iris by exciting Melanin, the main colouring component
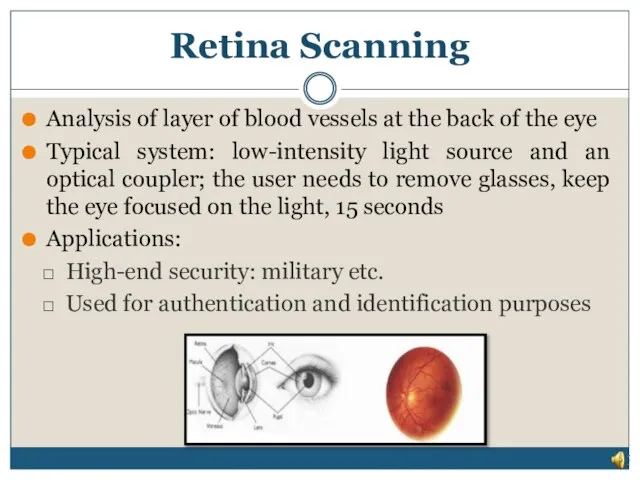
- 14. Retina Scanning Analysis of layer of blood vessels at the back of the eye Typical system:
- 15. The human retina is a thin tissue composed of neural cells that is located in the
- 16. DNA (Deoxyribonucleic acid) A DNA sample is used to produce either a DNA fingerprint or a
- 17. Speaker Recognition Voice print analysis Typical system: uses the pitch, pattern, tone, rhythm of speech for
- 18. Verification versus Identification There are two major applications of speaker recognition technologies and methodologies. If the
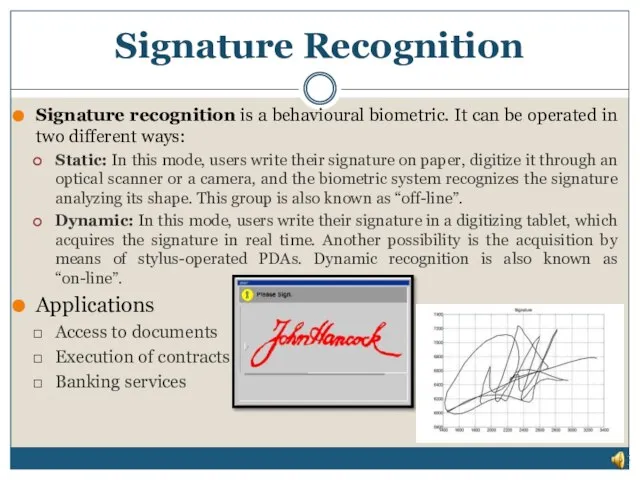
- 19. Signature Recognition Signature recognition is a behavioural biometric. It can be operated in two different ways:
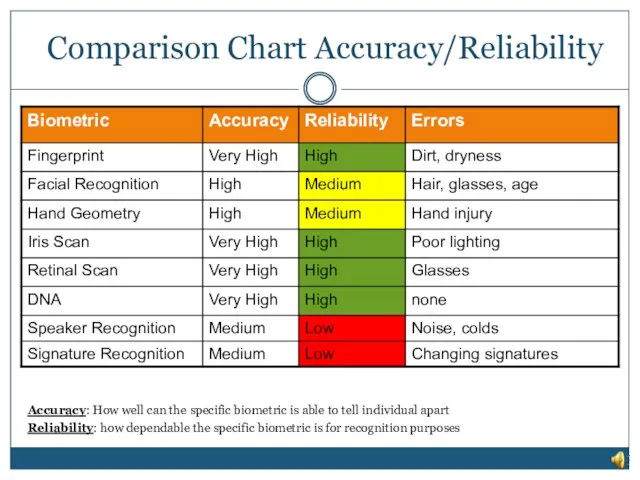
- 20. Comparison Chart Accuracy/Reliability Accuracy: How well can the specific biometric is able to tell individual apart
- 21. What Biometrics are Replacing Passwords PIN numbers Tokens Photo ID cards Smart cards Magnetic strip cards
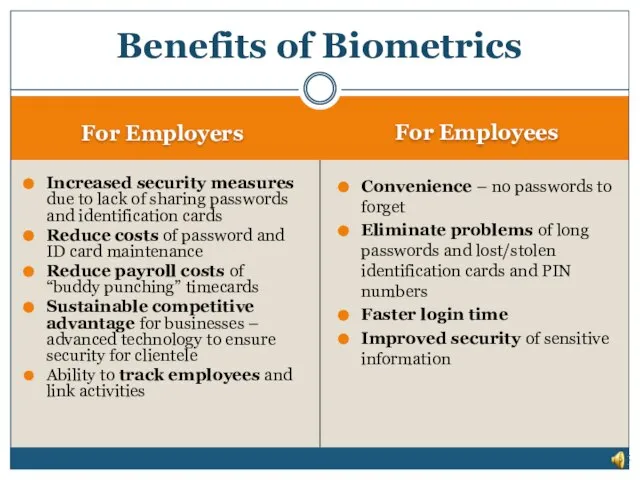
- 22. Benefits of Biometrics - Increased security - Convenience - Opportunity to build a sustainable competitive advantage
- 23. For Employers For Employees Increased security measures due to lack of sharing passwords and identification cards
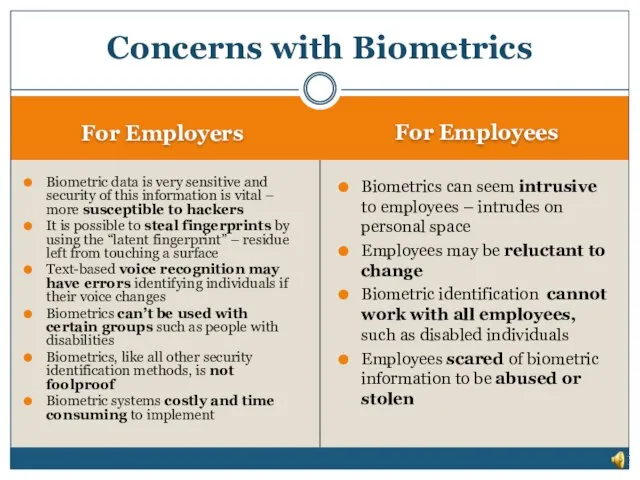
- 24. Concerns with Biometrics - Sensitive biometric information susceptible to hackers - Lack of privacy for employees
- 25. For Employers For Employees Biometric data is very sensitive and security of this information is vital
- 26. As with many emerging technologies, there are concerns with the abuse of biometric technology and identification.
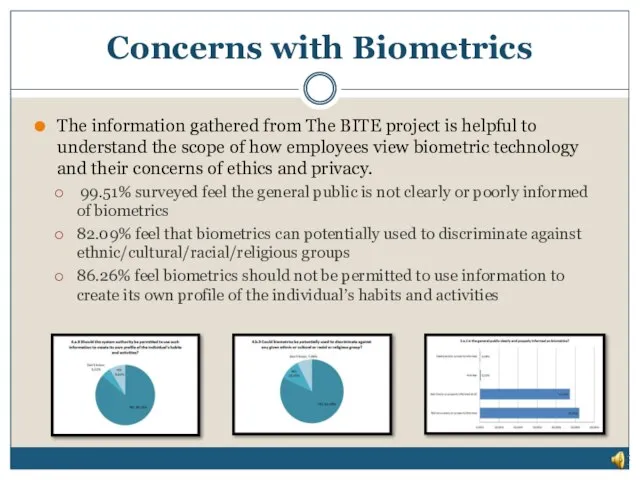
- 27. The information gathered from The BITE project is helpful to understand the scope of how employees
- 28. Biometrics in Business Current Biometric Applications: Computer logins ATMs Grocery stores Airport kiosks Driver’s licenses Internet
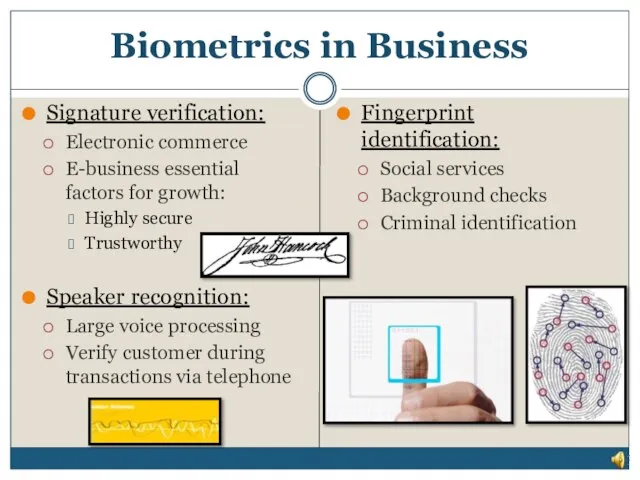
- 29. Signature verification: Electronic commerce E-business essential factors for growth: Highly secure Trustworthy Speaker recognition: Large voice
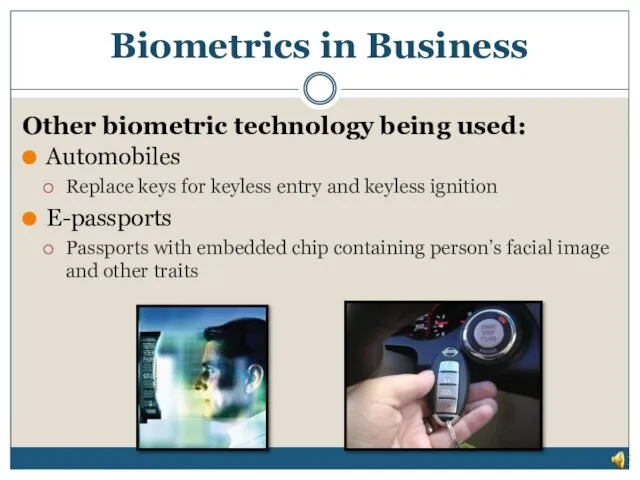
- 30. Automobiles Replace keys for keyless entry and keyless ignition E-passports Passports with embedded chip containing person’s
- 31. Travel and Transport Biometrics is growing in the travel and transportation industry due to heightened security
- 33. Скачать презентацию




 Условия признания субъектов малого или среднего предпринимательства (МСП) социальным предприятием
Условия признания субъектов малого или среднего предпринимательства (МСП) социальным предприятием Юридическая ответственность
Юридическая ответственность Изменения в трудовом законодательстве
Изменения в трудовом законодательстве Конституційне право Французької Республіки
Конституційне право Французької Республіки Право водопользования и его виды
Право водопользования и его виды Рецидивная преступность
Рецидивная преступность Благовестие и закон
Благовестие и закон Государство и право Великобритании в XIX – XX вв. Лекция 8
Государство и право Великобритании в XIX – XX вв. Лекция 8 Приемы юридической техники
Приемы юридической техники Уголовная ответственность и ее основания
Уголовная ответственность и ее основания Муниципальный округ: новый тип муниципального образования
Муниципальный округ: новый тип муниципального образования Осуществление строительного контроля и технического надзора строящегося объекта. Лекция 1
Осуществление строительного контроля и технического надзора строящегося объекта. Лекция 1 Наследственное право (лекция 7)
Наследственное право (лекция 7) Суды и судьи
Суды и судьи Деятельность Министерства иностранных Дел Российской федерации
Деятельность Министерства иностранных Дел Российской федерации Органы государственной власти РФ
Органы государственной власти РФ Судебная практика. Дорожно–транспортное происшествие. Возмещение вреда
Судебная практика. Дорожно–транспортное происшествие. Возмещение вреда Законодательство о защите прав потребителей
Законодательство о защите прав потребителей Особенности становления и развития мусульманского права
Особенности становления и развития мусульманского права Гражданское право является одной из сложнейших отраслей российской системы права
Гражданское право является одной из сложнейших отраслей российской системы права Предоставление разрешения на отклонение от предельных параметров строительства, реконструкции объектов строительства
Предоставление разрешения на отклонение от предельных параметров строительства, реконструкции объектов строительства Понятие избирательной системы и избирательного права. Виды избирательных систем
Понятие избирательной системы и избирательного права. Виды избирательных систем Российский флаг – наша гордость
Российский флаг – наша гордость Преступление, его признаки и классификация. Множественность преступлений
Преступление, его признаки и классификация. Множественность преступлений Процессуальный кодекс Древнерусского государства
Процессуальный кодекс Древнерусского государства Конституционное право как ведущая отрасль права, наука и учебная дисциплина
Конституционное право как ведущая отрасль права, наука и учебная дисциплина Етапи прийняття інветором виконаних робіт та готових об'єктів
Етапи прийняття інветором виконаних робіт та готових об'єктів Понятие, значение и особенности организационно-правовых документов в деятельности организации
Понятие, значение и особенности организационно-правовых документов в деятельности организации