Содержание
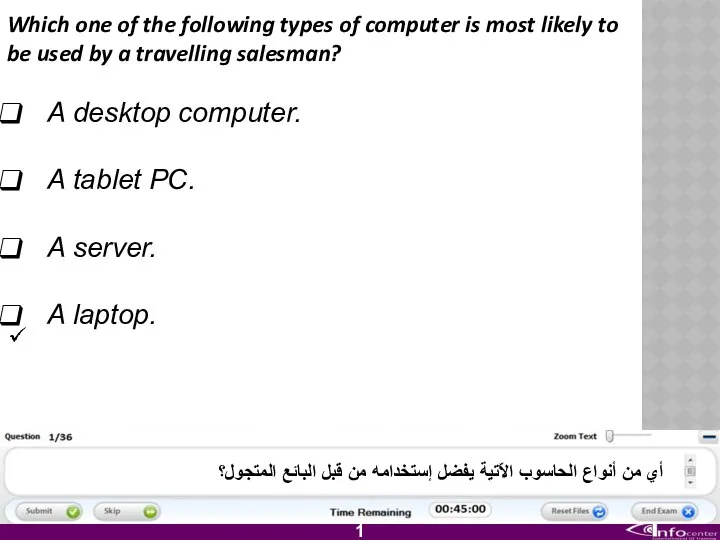
- 2. Which one of the following types of computer is most likely to be used by a
- 3. Which one of the following is a term for systems used to store, retrieve, process and
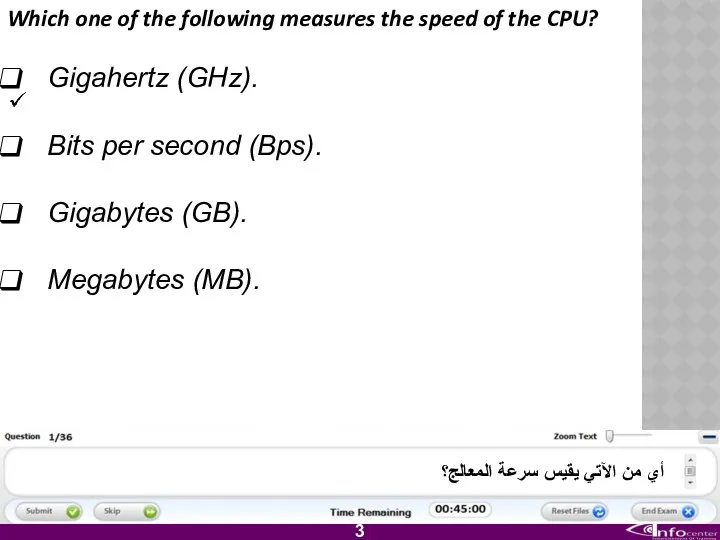
- 4. Which one of the following measures the speed of the CPU? Gigahertz (GHz). Bits per second
- 5. Which one of the following is a term for an audio or video recording posted on
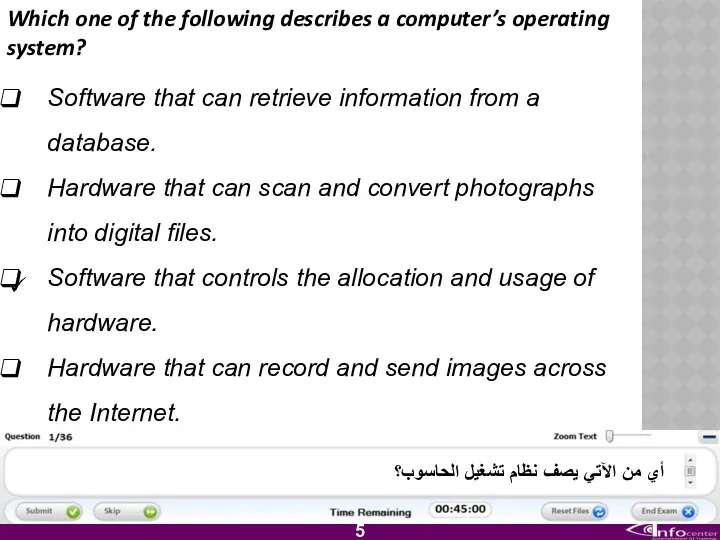
- 6. Which one of the following describes a computer’s operating system? Software that can retrieve information from
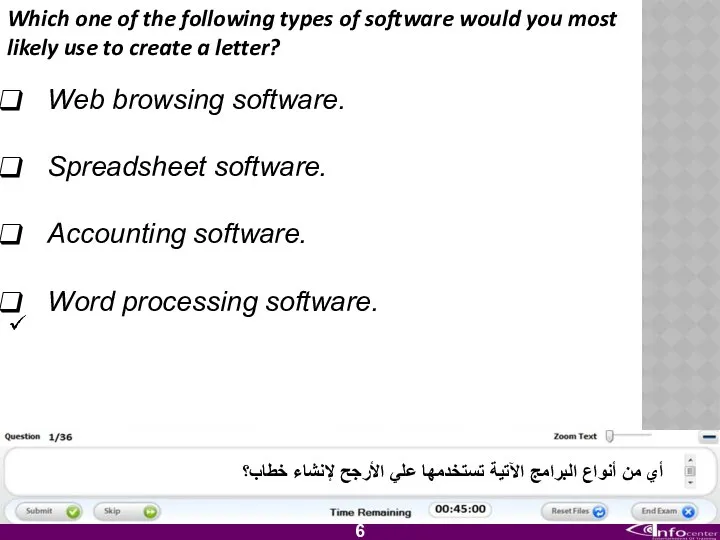
- 7. Which one of the following types of software would you most likely use to create a
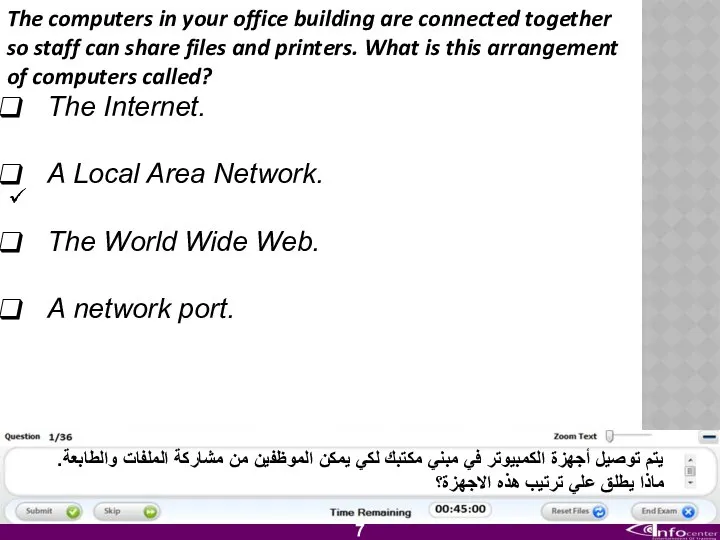
- 8. The computers in your office building are connected together so staff can share files and printers.
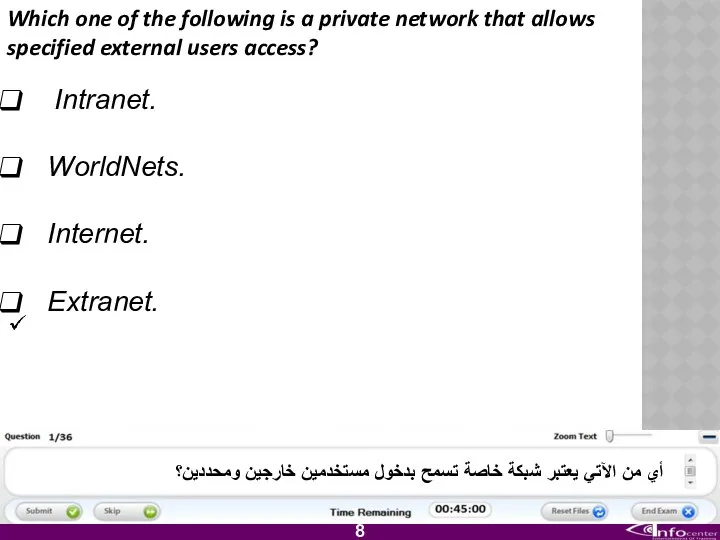
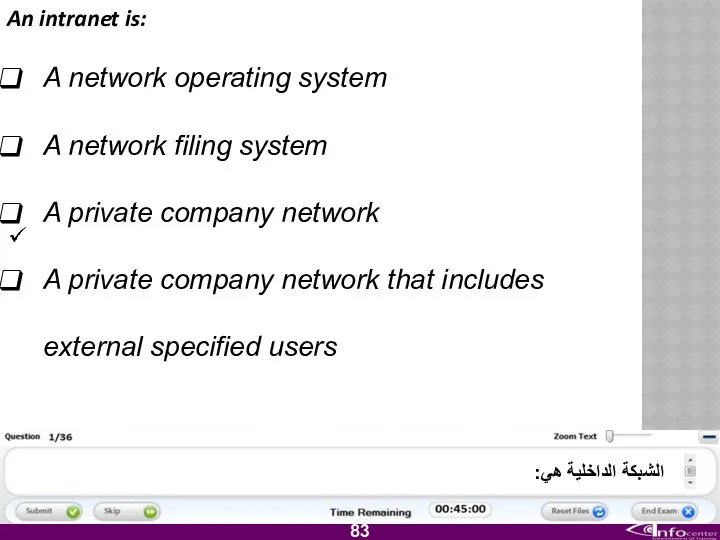
- 9. Which one of the following is a private network that allows specified external users access? Intranet.
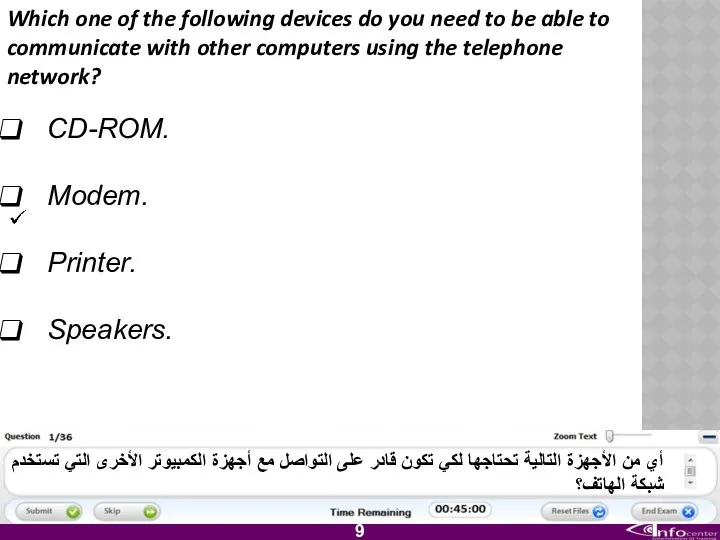
- 10. Which one of the following devices do you need to be able to communicate with other
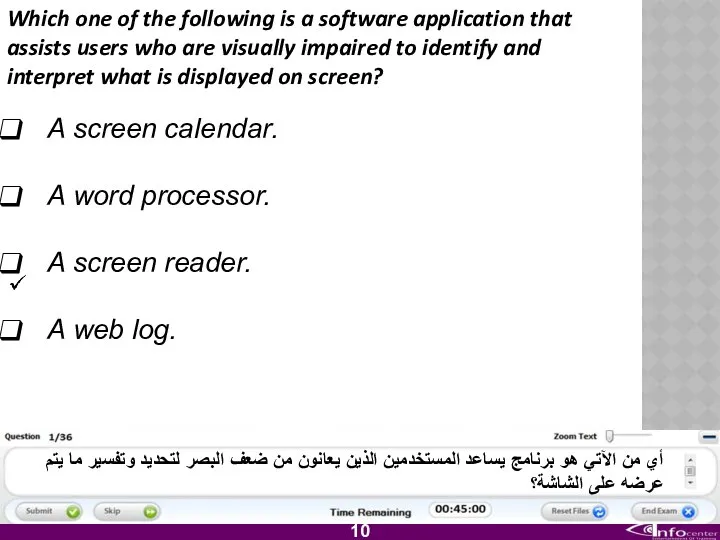
- 11. Which one of the following is a software application that assists users who are visually impaired
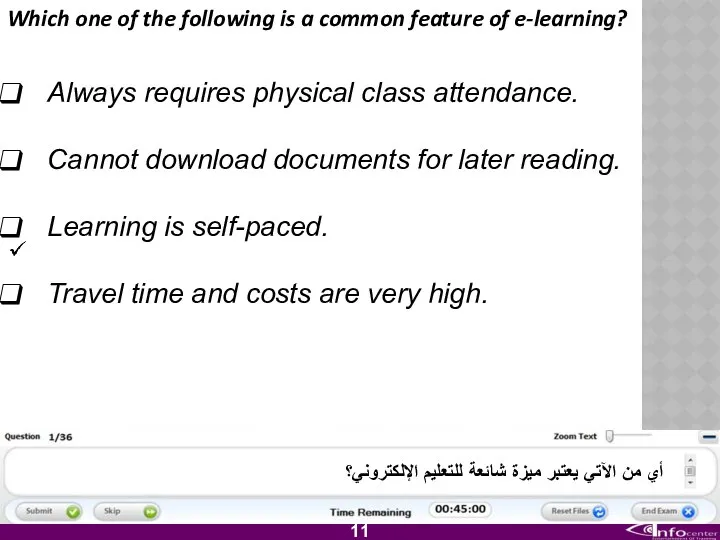
- 12. Which one of the following is a common feature of e-learning? Always requires physical class attendance.
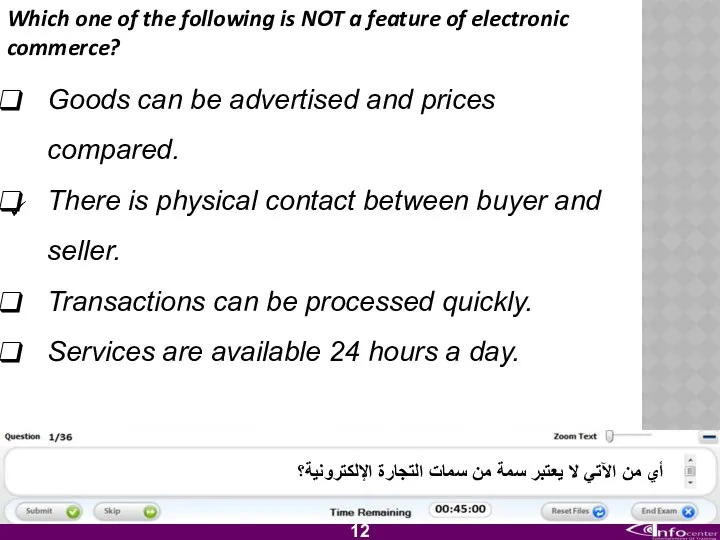
- 13. Which one of the following is NOT a feature of electronic commerce? Goods can be advertised
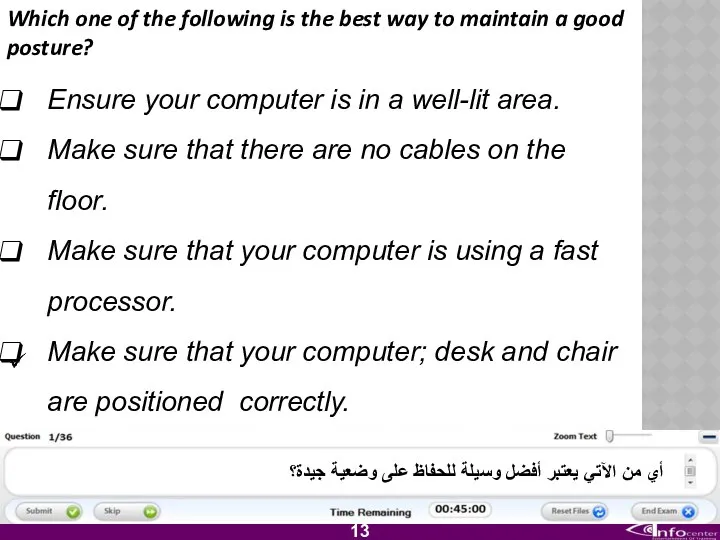
- 14. Which one of the following is the best way to maintain a good posture? Ensure your
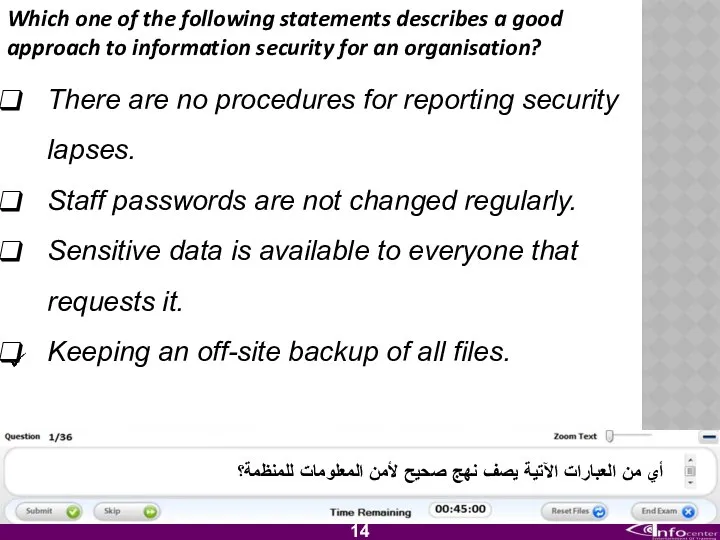
- 15. Which one of the following statements describes a good approach to information security for an organisation?
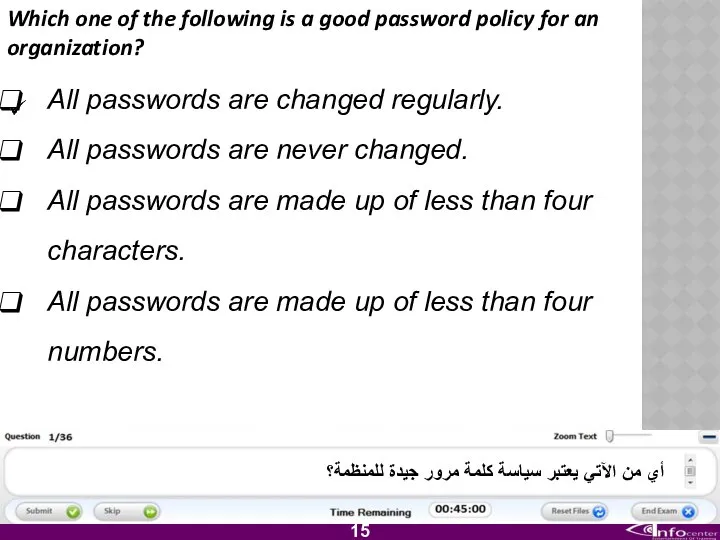
- 16. Which one of the following is a good password policy for an organization? All passwords are
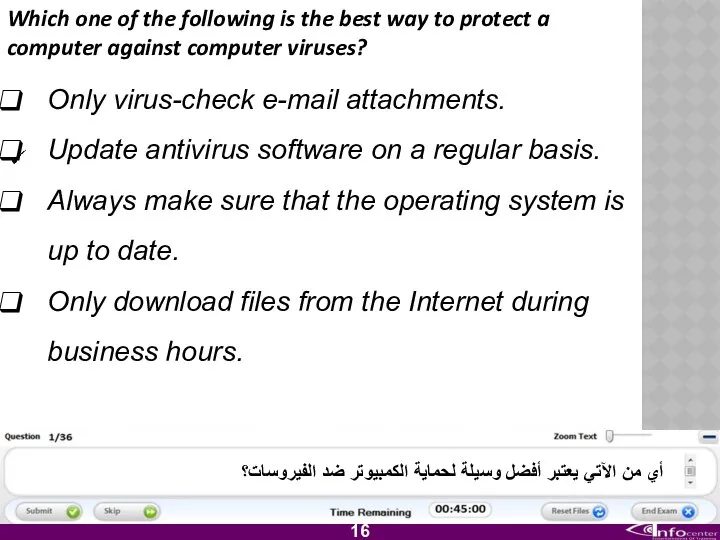
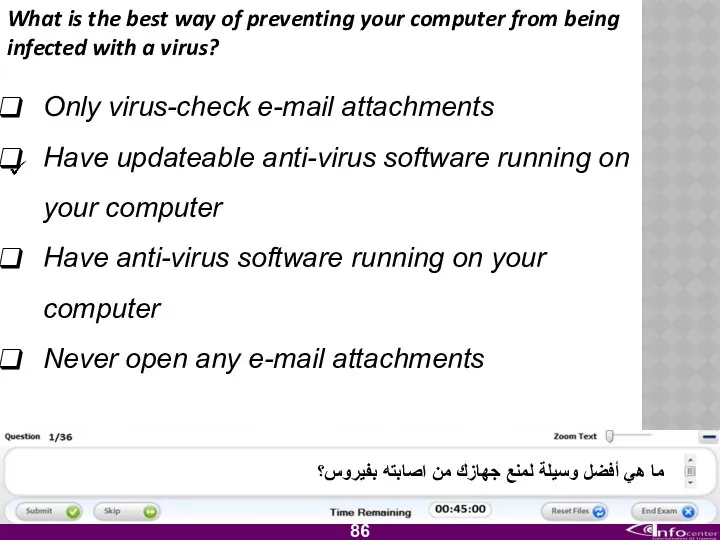
- 17. Which one of the following is the best way to protect a computer against computer viruses?
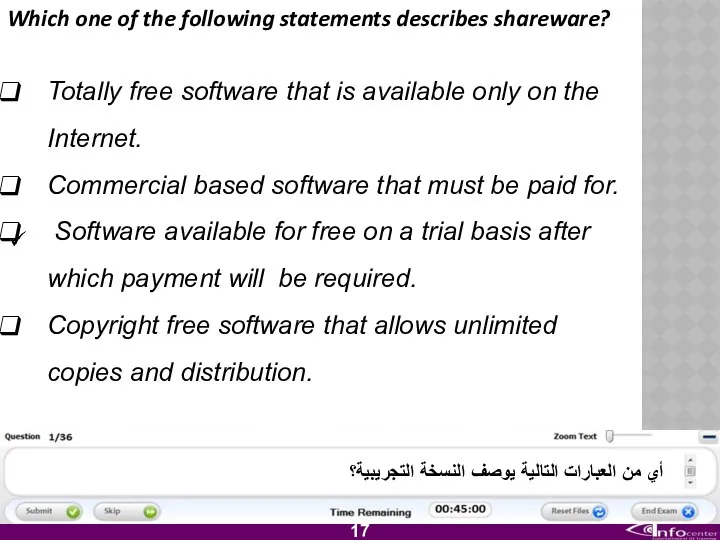
- 18. Which one of the following statements describes shareware? Totally free software that is available only on
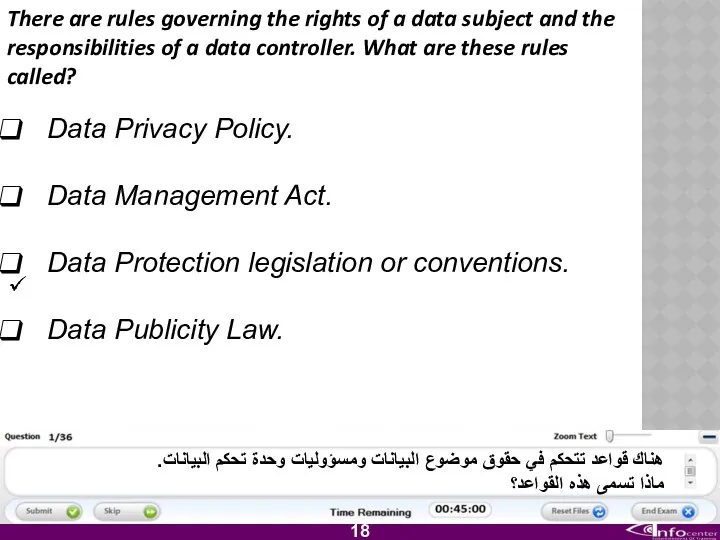
- 19. There are rules governing the rights of a data subject and the responsibilities of a data
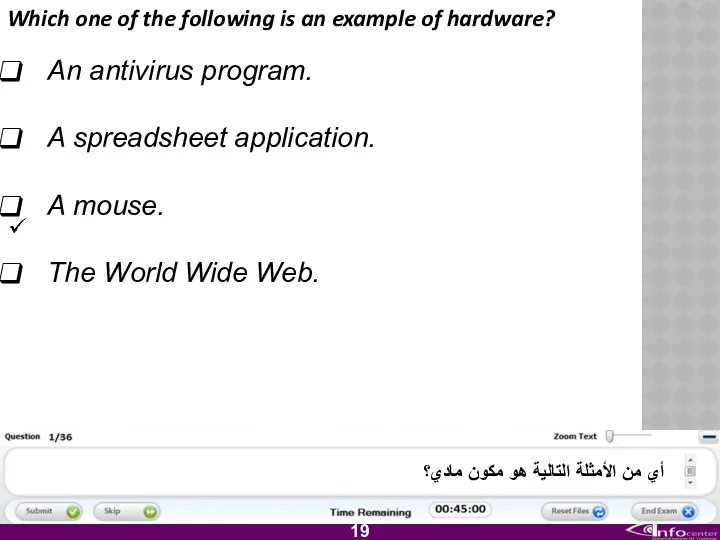
- 20. Which one of the following is an example of hardware? An antivirus program. A spreadsheet application.
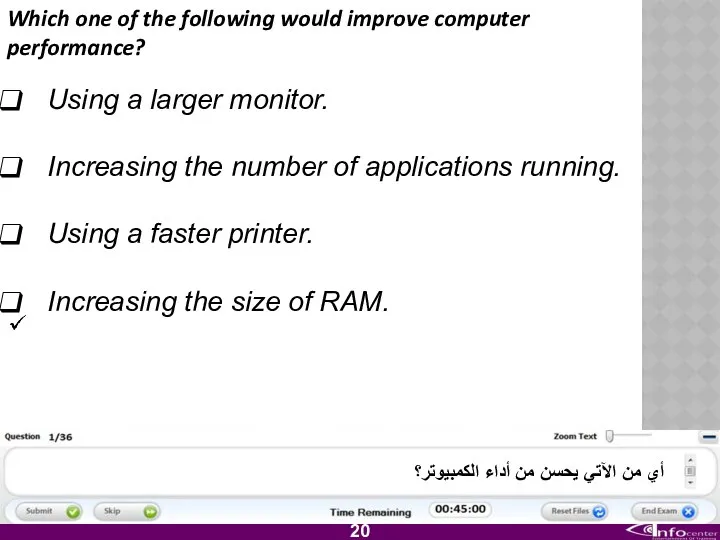
- 21. Which one of the following would improve computer performance? Using a larger monitor. Increasing the number
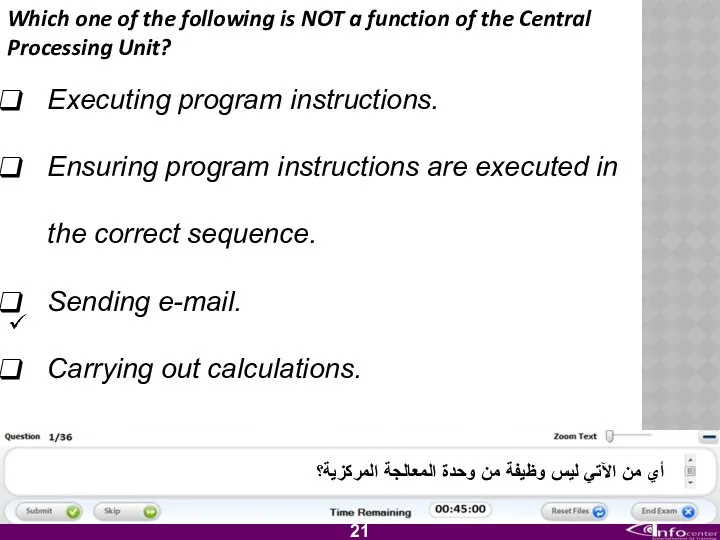
- 22. Which one of the following is NOT a function of the Central Processing Unit? Executing program
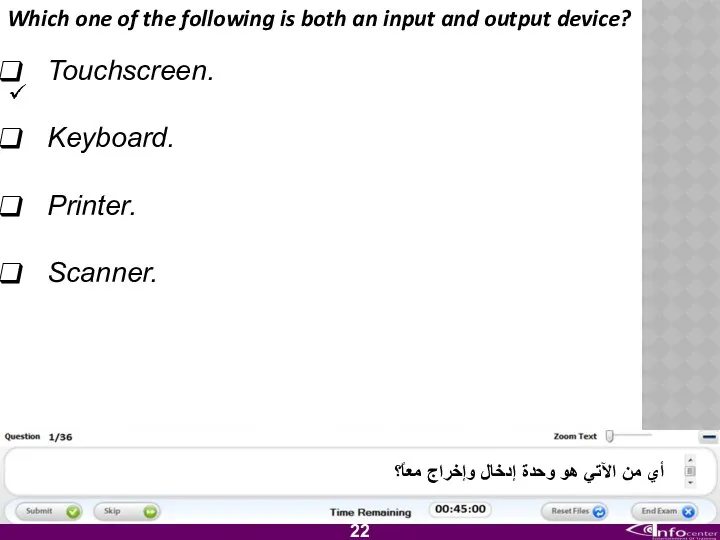
- 23. Which one of the following is both an input and output device? Touchscreen. Keyboard. Printer. Scanner.
- 24. Which one of the following is a method of publishing frequently updated content such as news
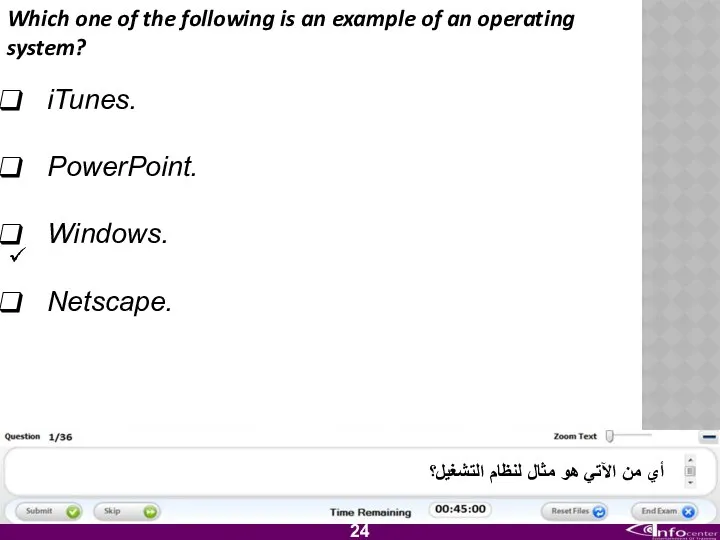
- 25. Which one of the following is an example of an operating system? iTunes. PowerPoint. Windows. Netscape.
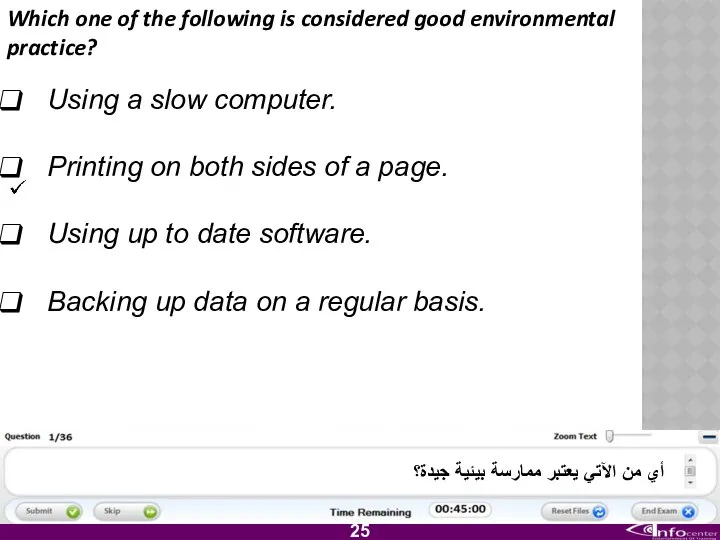
- 26. Which one of the following is considered good environmental practice? Using a slow computer. Printing on
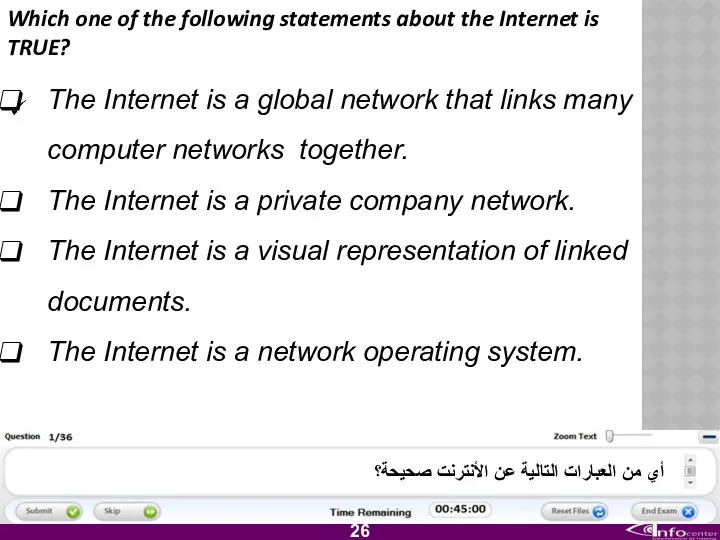
- 27. Which one of the following statements about the Internet is TRUE? The Internet is a global
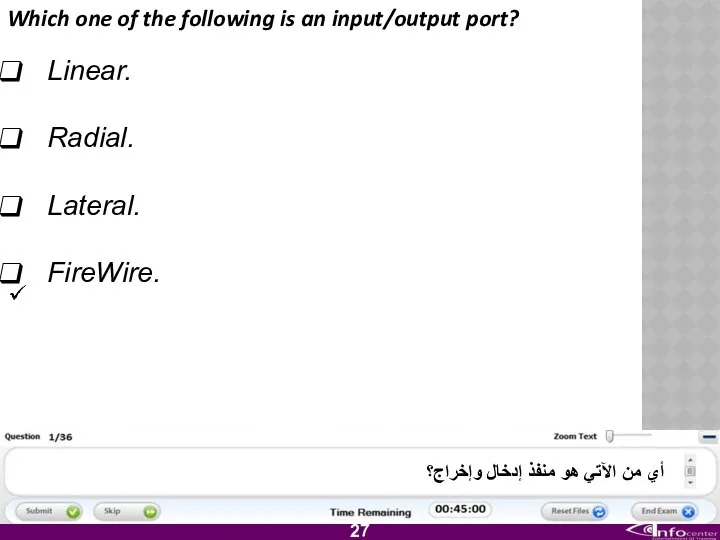
- 28. Which one of the following is an input/output port? Linear. Radial. Lateral. FireWire. أي من الآتي
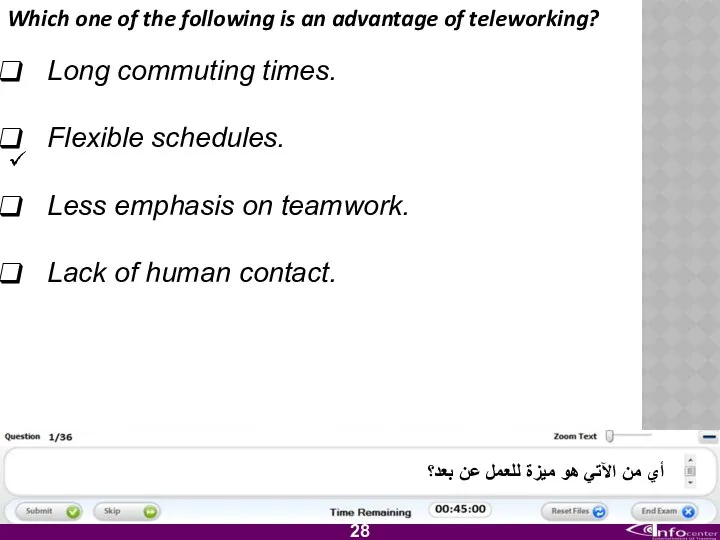
- 29. Which one of the following is an advantage of teleworking? Long commuting times. Flexible schedules. Less
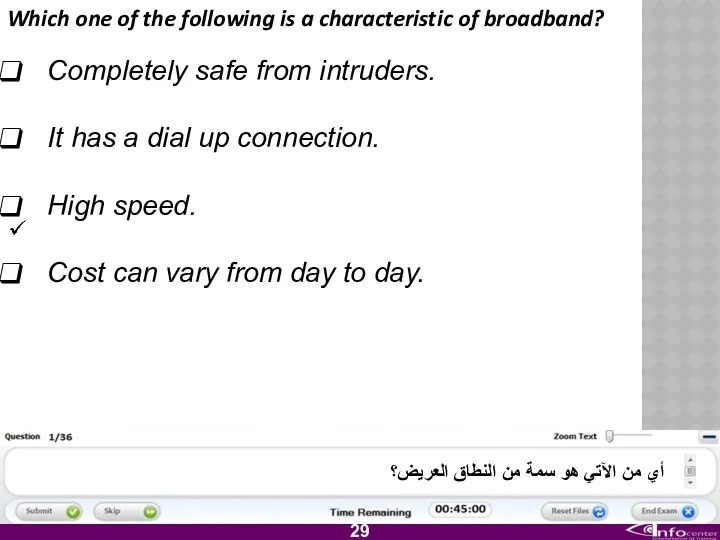
- 30. Which one of the following is a characteristic of broadband? Completely safe from intruders. It has
- 31. Which one of the following is a text-based communication between two or more people over the
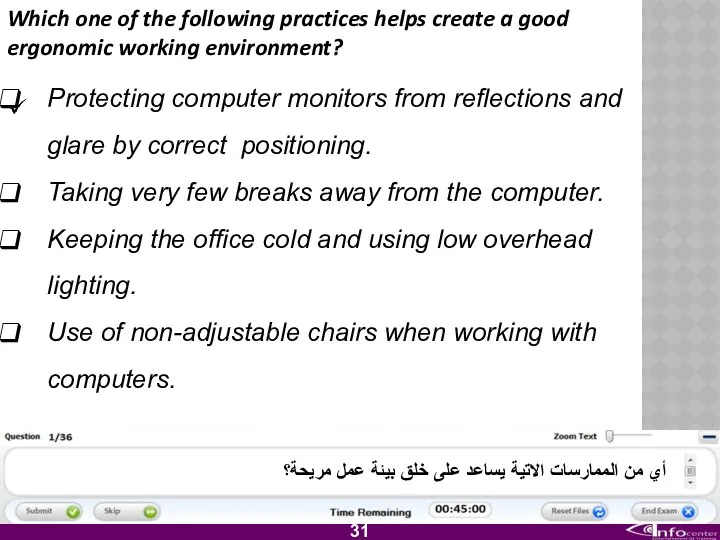
- 32. Which one of the following practices helps create a good ergonomic working environment? Protecting computer monitors
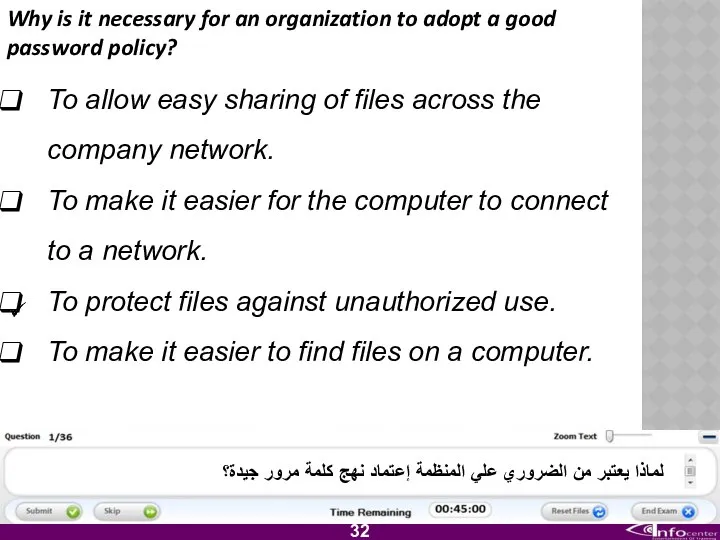
- 33. Why is it necessary for an organization to adopt a good password policy? To allow easy
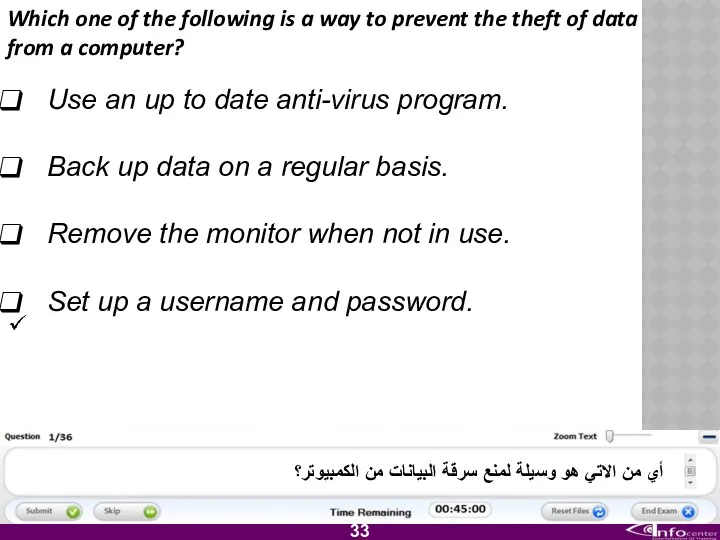
- 34. Which one of the following is a way to prevent the theft of data from a
- 35. Which one of the following should be carried out to safeguard files from loss in case
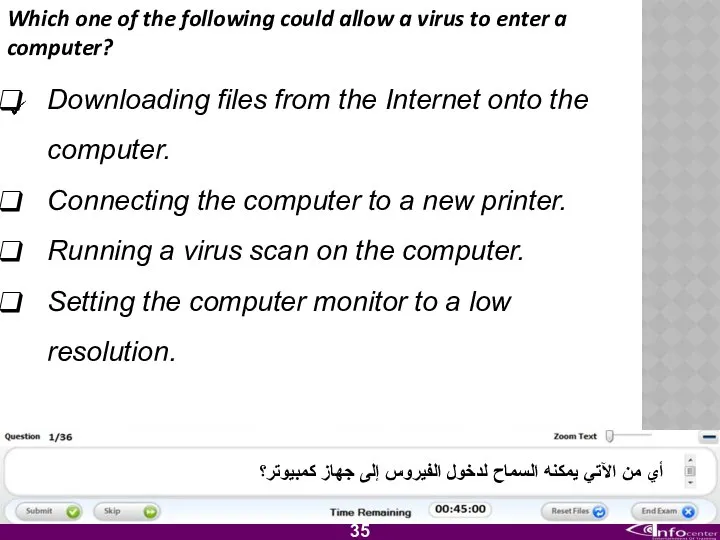
- 36. Which one of the following could allow a virus to enter a computer? Downloading files from
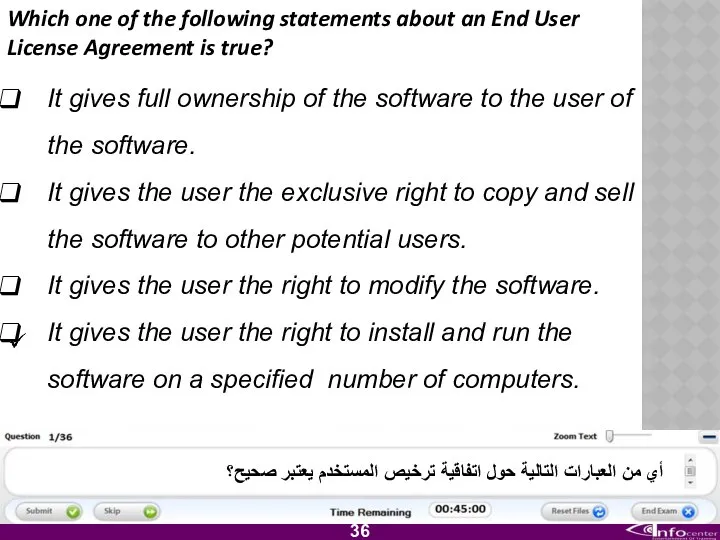
- 37. Which one of the following statements about an End User License Agreement is true? It gives
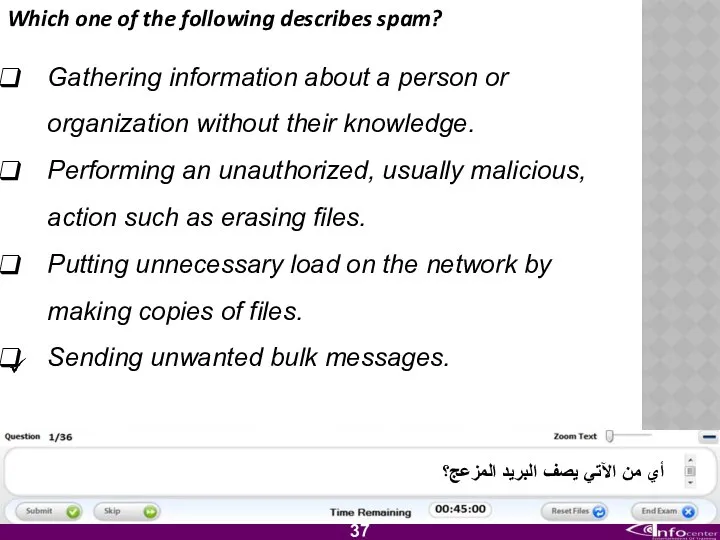
- 38. Which one of the following describes spam? Gathering information about a person or organization without their
- 39. Which one of the following can protect a computer from the risk of unwanted emails? Anti-spam
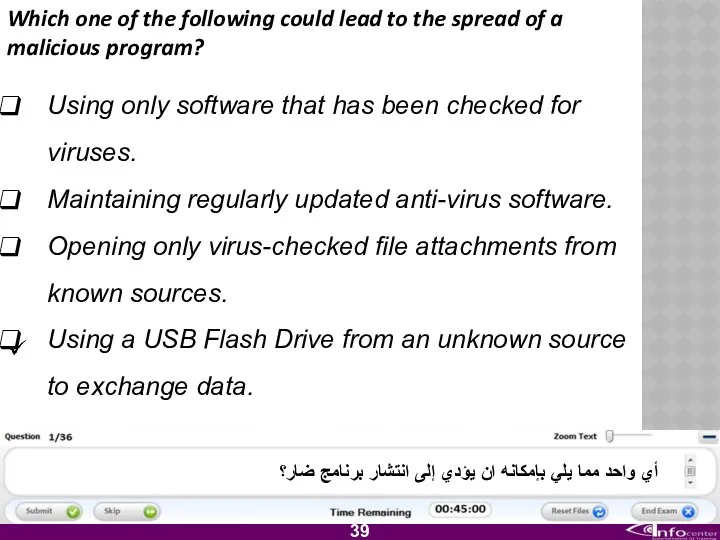
- 40. Which one of the following could lead to the spread of a malicious program? Using only
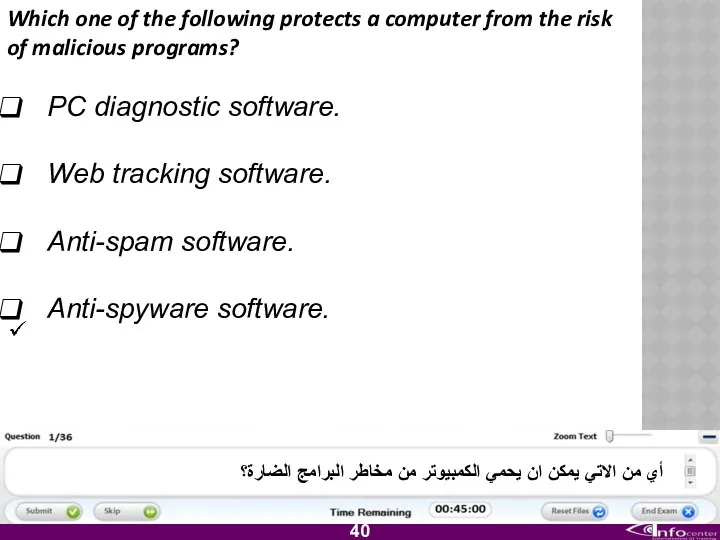
- 41. Which one of the following protects a computer from the risk of malicious programs? PC diagnostic
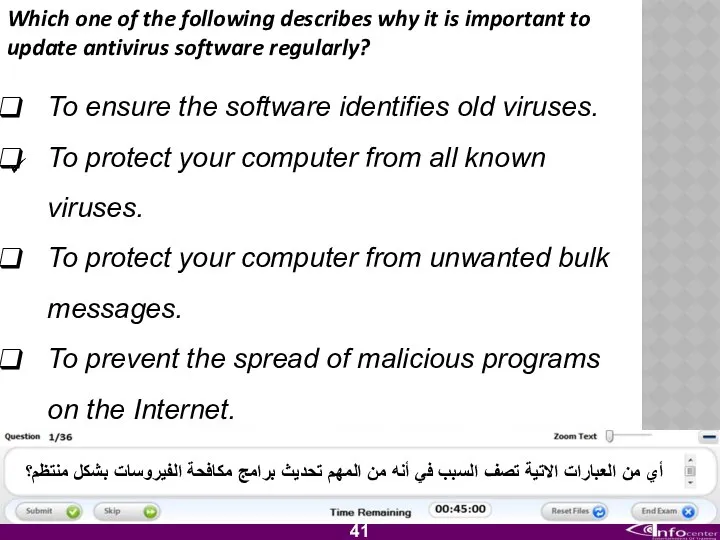
- 42. Which one of the following describes why it is important to update antivirus software regularly? To
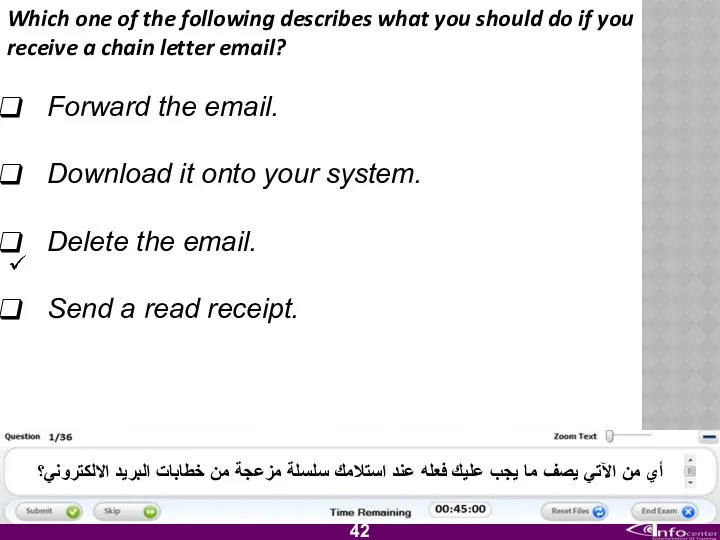
- 43. Which one of the following describes what you should do if you receive a chain letter
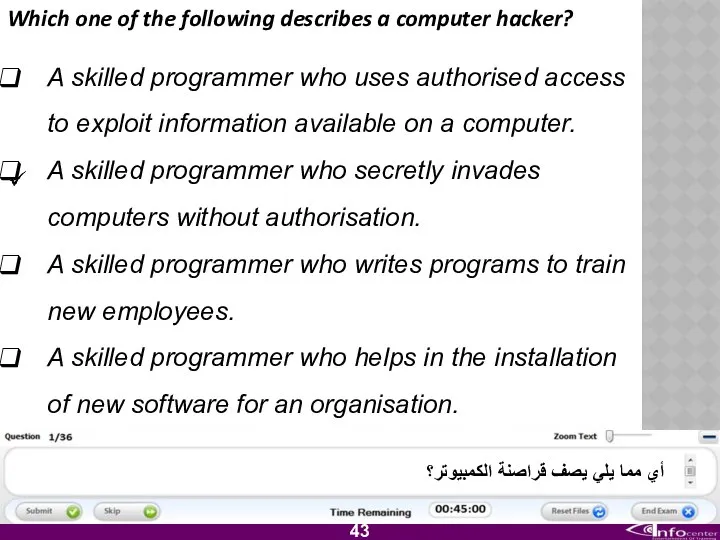
- 44. Which one of the following describes a computer hacker? A skilled programmer who uses authorised access
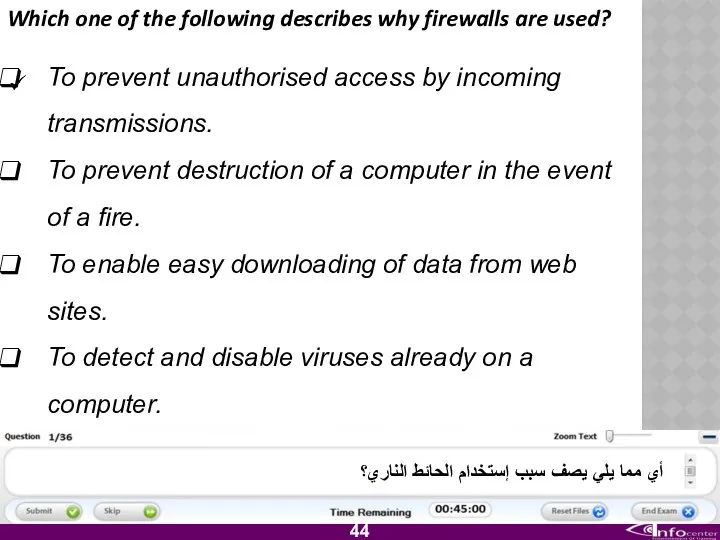
- 45. Which one of the following describes why firewalls are used? To prevent unauthorised access by incoming
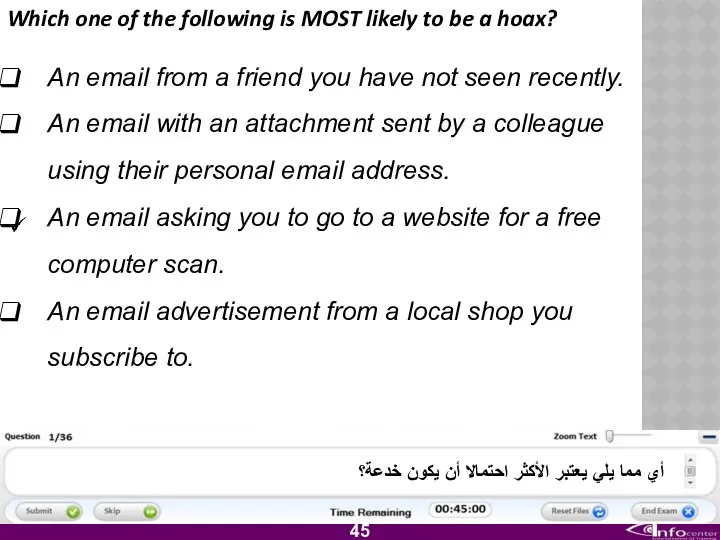
- 46. Which one of the following is MOST likely to be a hoax? An email from a
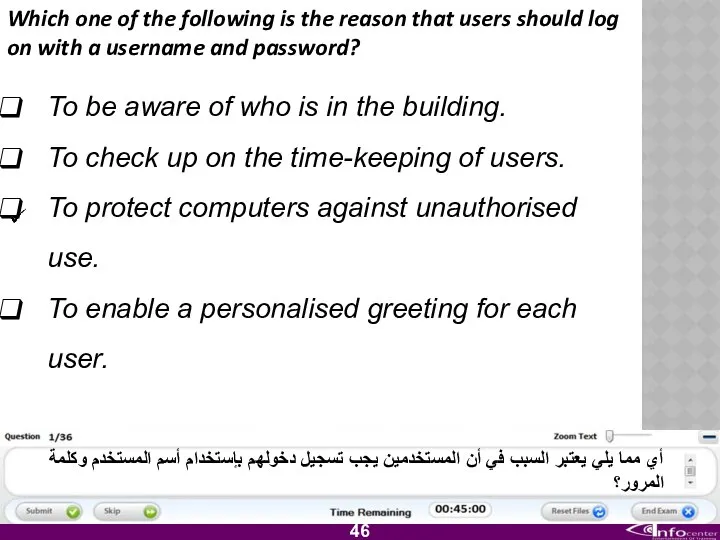
- 47. Which one of the following is the reason that users should log on with a username
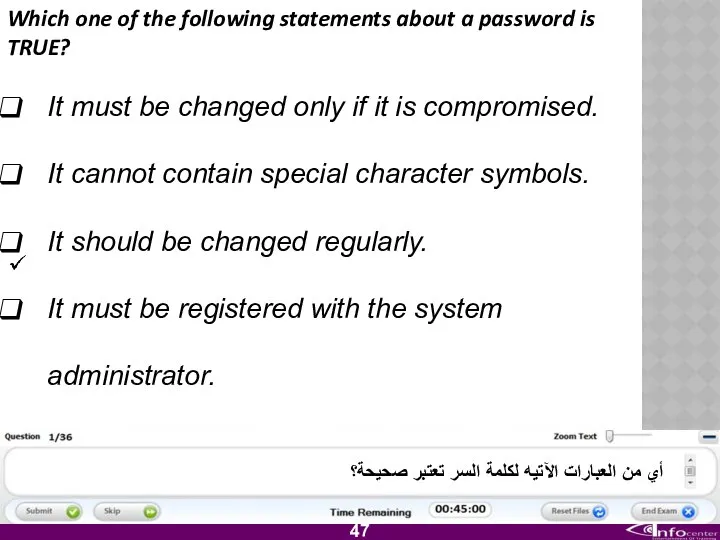
- 48. Which one of the following statements about a password is TRUE? It must be changed only
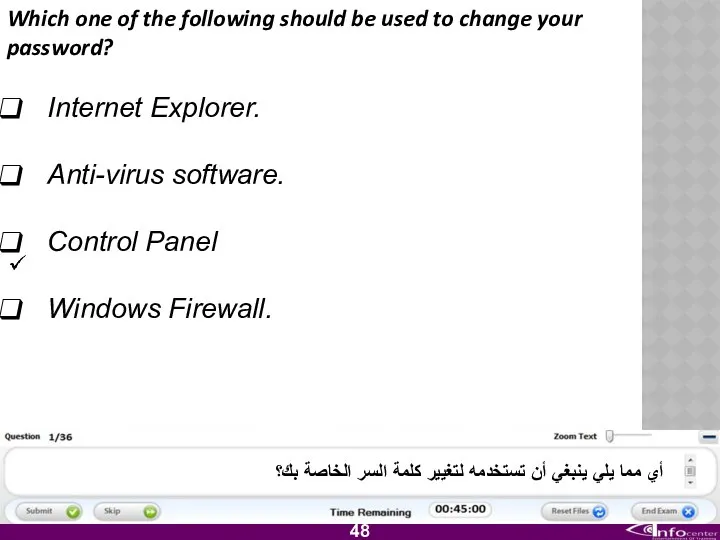
- 49. Which one of the following should be used to change your password? Internet Explorer. Anti-virus software.
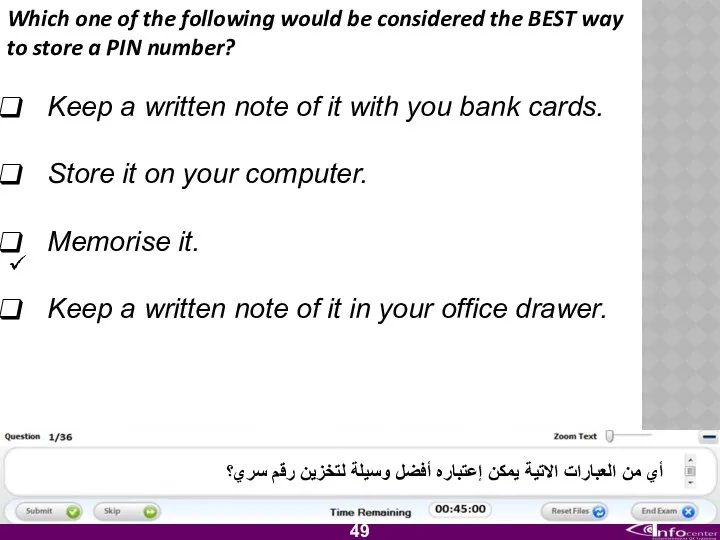
- 50. Which one of the following would be considered the BEST way to store a PIN number?
- 51. Which one of the following shows respect for confidentiality of information? Discussing confidential information over the
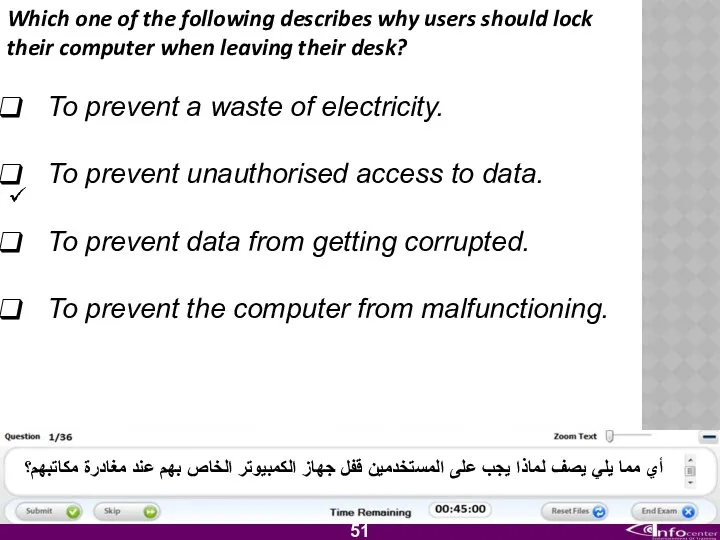
- 52. Which one of the following describes why users should lock their computer when leaving their desk?
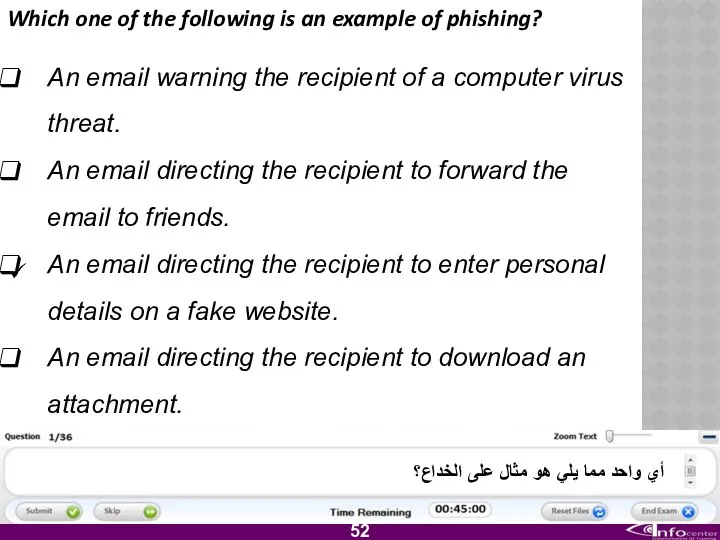
- 53. Which one of the following is an example of phishing? An email warning the recipient of
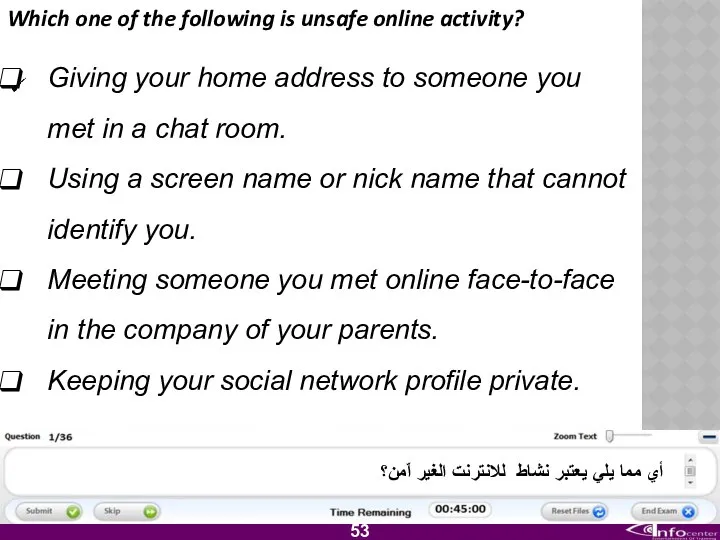
- 54. Which one of the following is unsafe online activity? Giving your home address to someone you
- 55. Which one of the following describes a public network? A network where devices outside the network
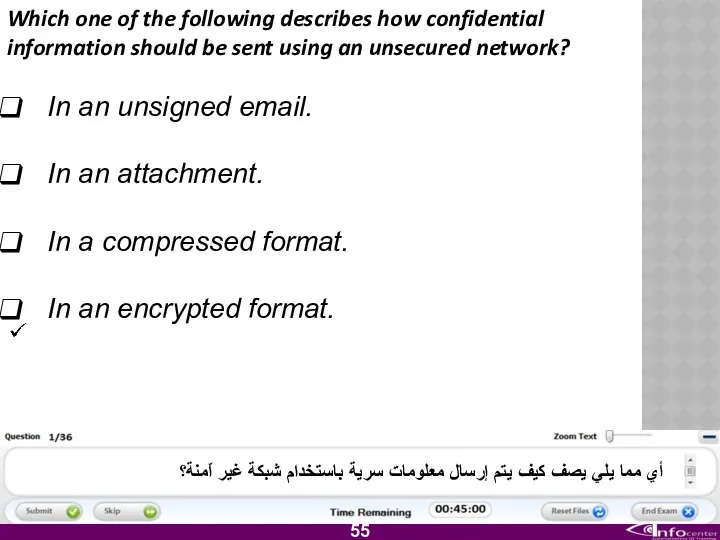
- 56. Which one of the following describes how confidential information should be sent using an unsecured network?
- 57. Which one of the following statements about wireless networks is TRUE? They cannot be intercepted by
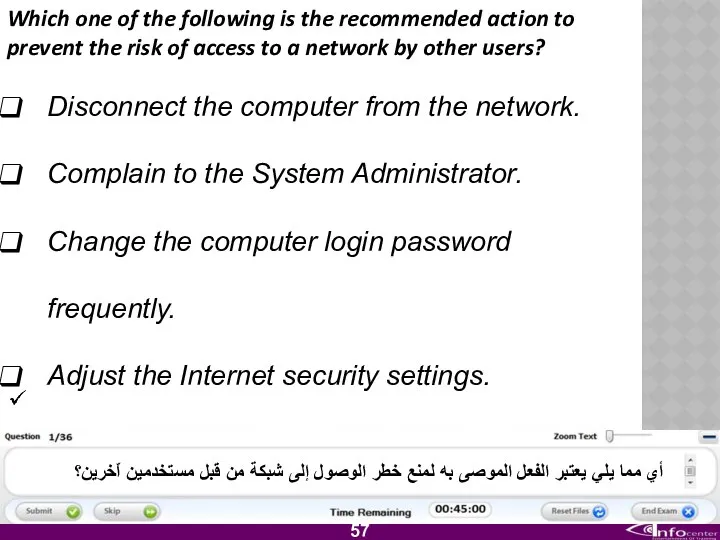
- 58. Which one of the following is the recommended action to prevent the risk of access to
- 59. Which one of the following describes Bluetooth? Short-range wired protocol for exchanging data. Short-range wireless protocol
- 60. Which one of the following describes why Bluetooth device settings should be adjusted? To increase the
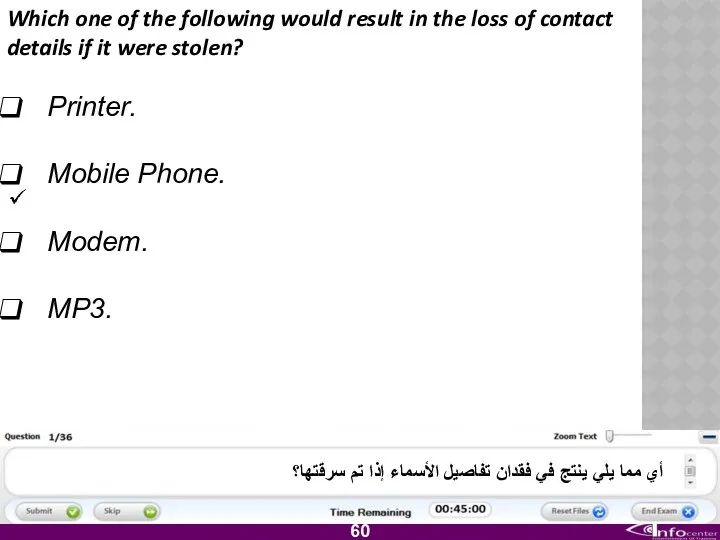
- 61. Which one of the following would result in the loss of contact details if it were
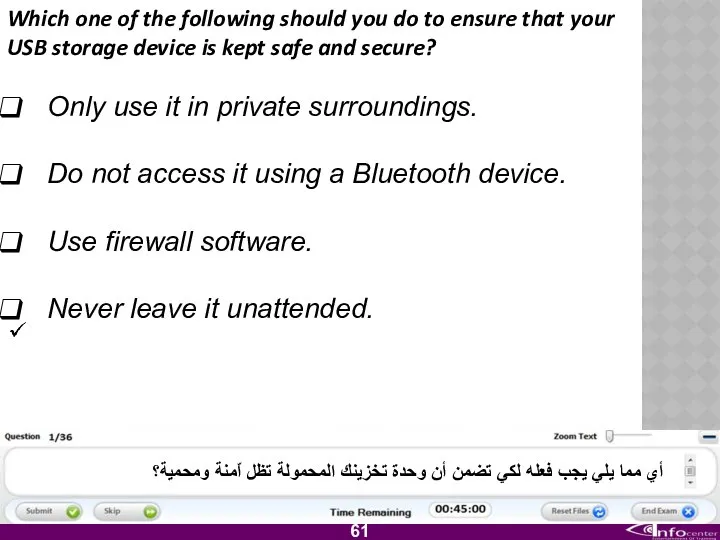
- 62. Which one of the following should you do to ensure that your USB storage device is
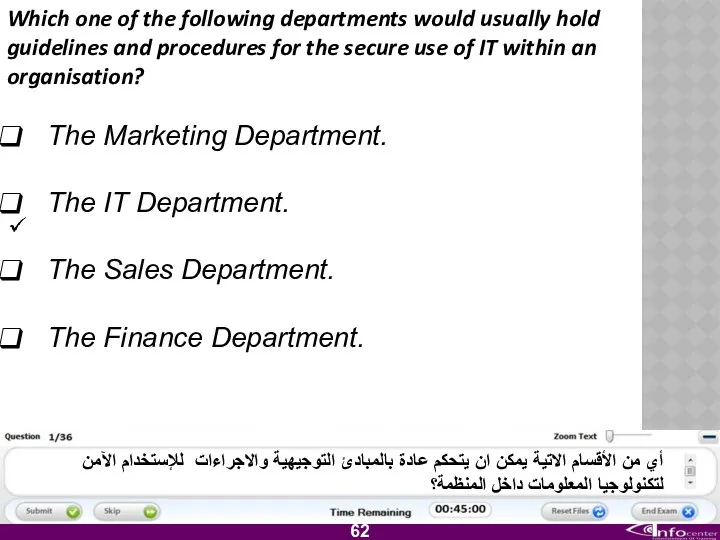
- 63. Which one of the following departments would usually hold guidelines and procedures for the secure use
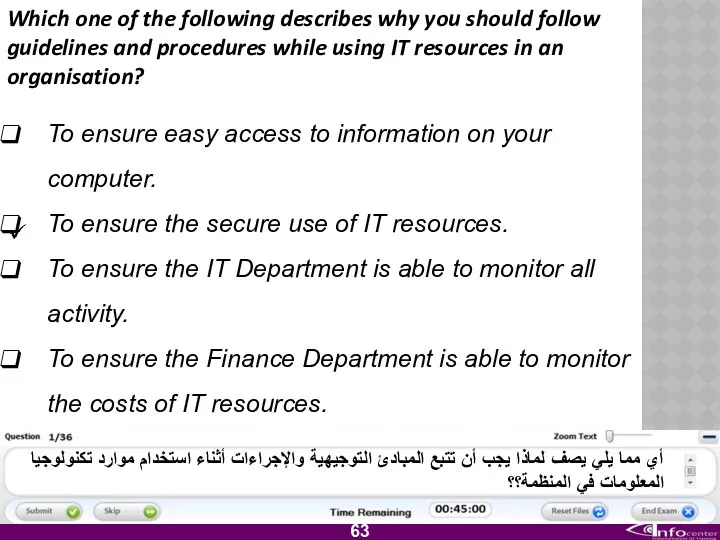
- 64. Which one of the following describes why you should follow guidelines and procedures while using IT
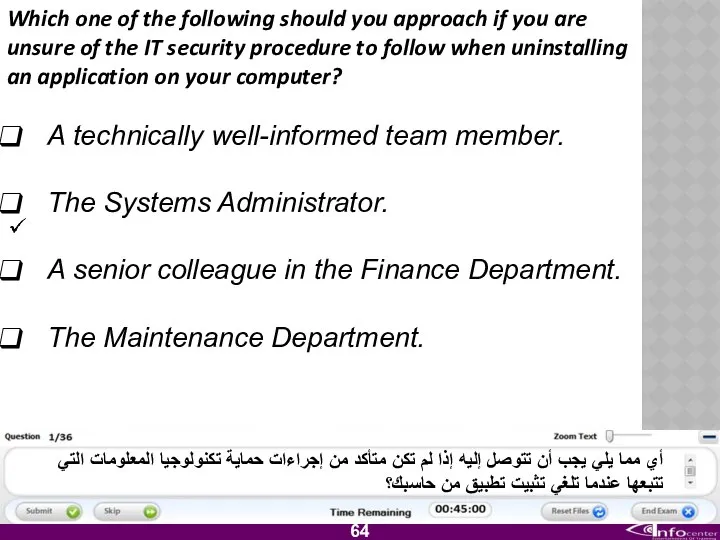
- 65. Which one of the following should you approach if you are unsure of the IT security
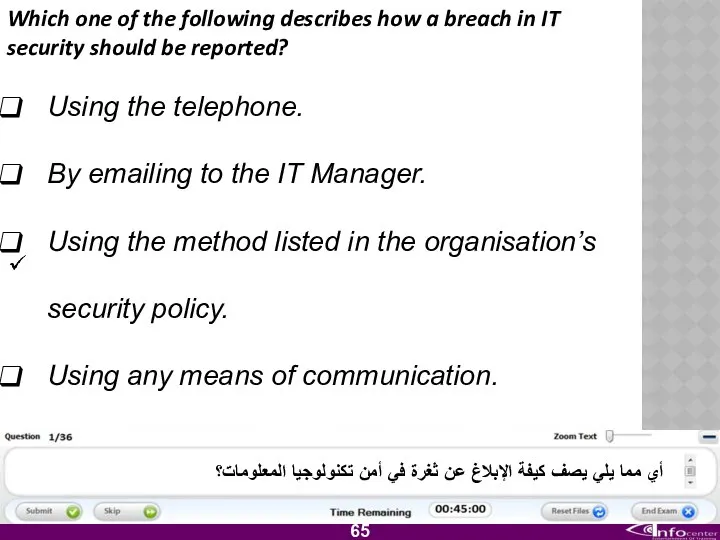
- 66. Which one of the following describes how a breach in IT security should be reported? Using
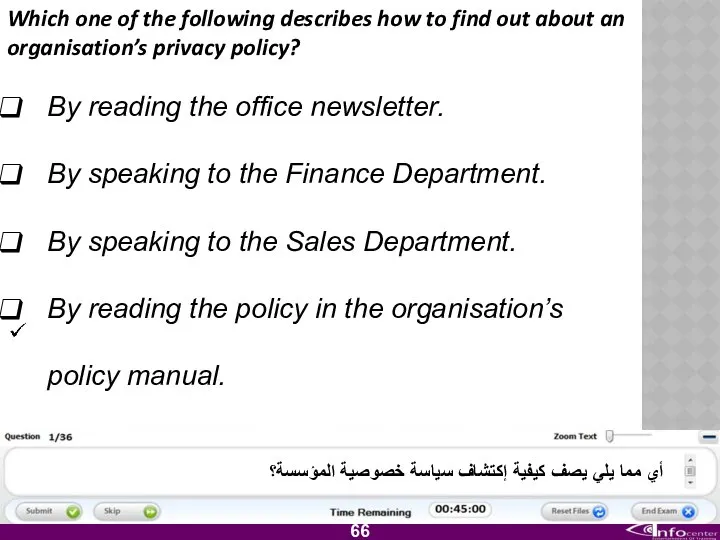
- 67. Which one of the following describes how to find out about an organisation’s privacy policy? By
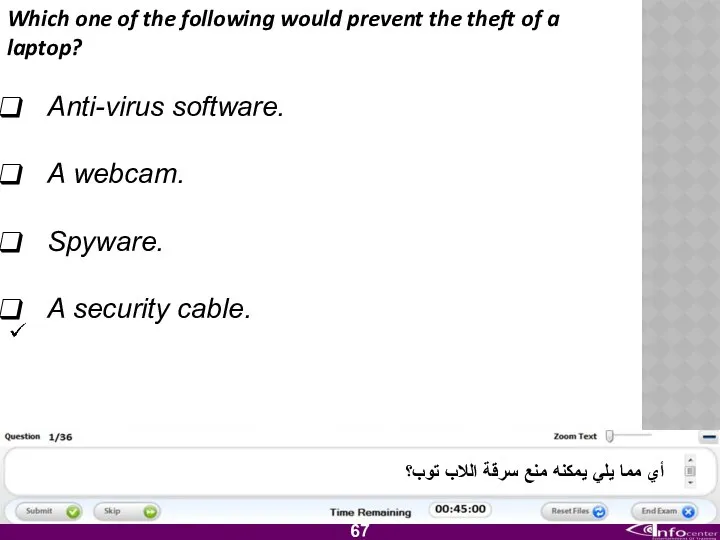
- 68. Which one of the following would prevent the theft of a laptop? Anti-virus software. A webcam.
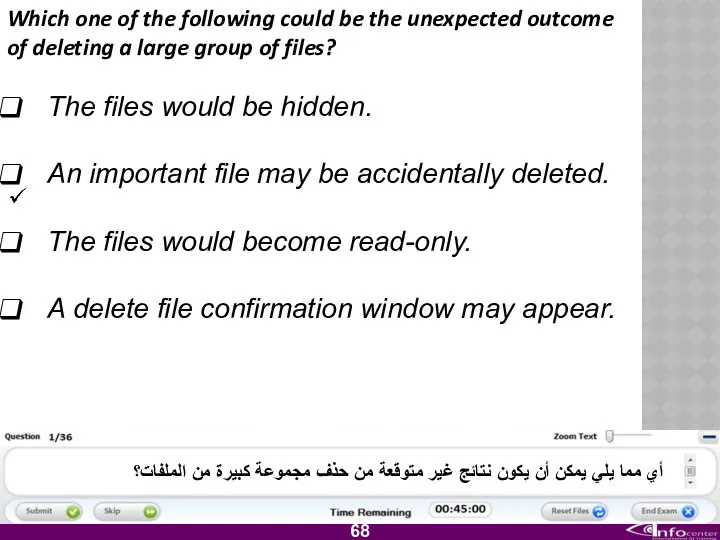
- 69. Which one of the following could be the unexpected outcome of deleting a large group of
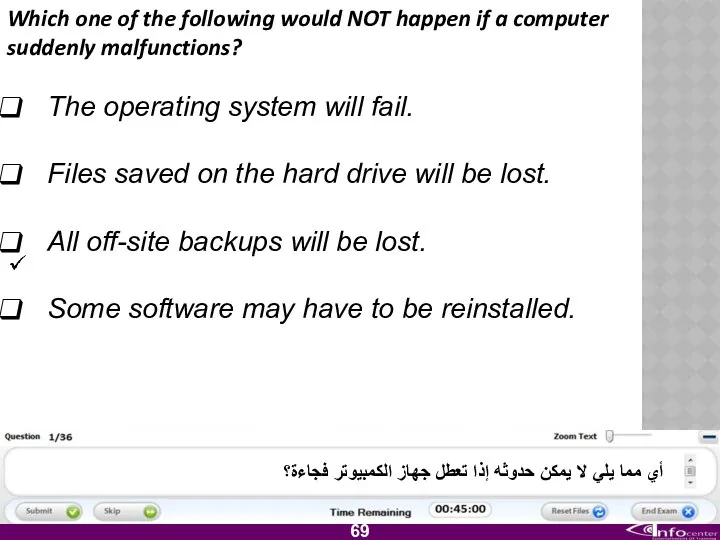
- 70. Which one of the following would NOT happen if a computer suddenly malfunctions? The operating system
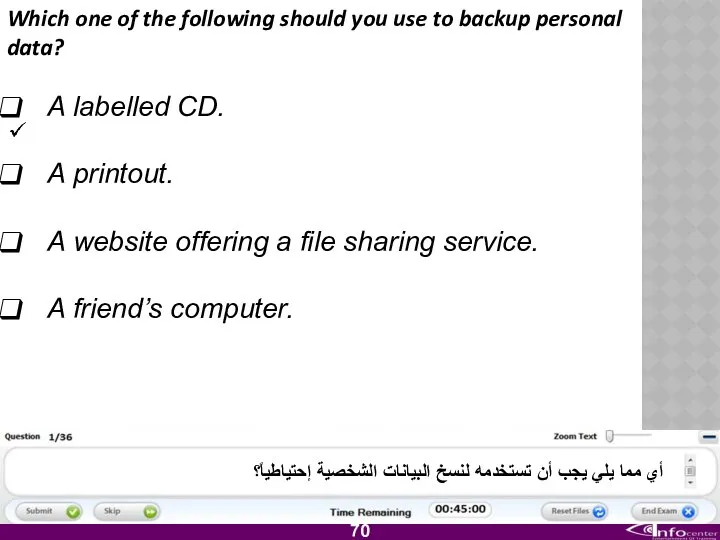
- 71. Which one of the following should you use to backup personal data? A labelled CD. A
- 72. Which one of the following describes why it is important to have a secure off-site backup
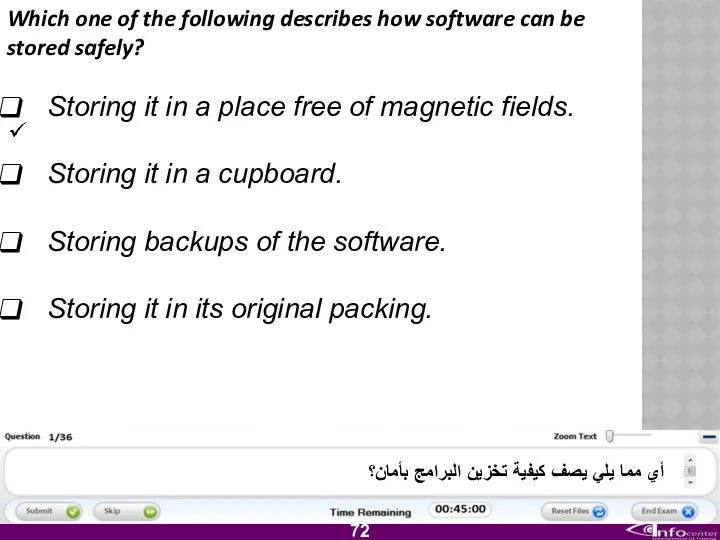
- 73. Which one of the following describes how software can be stored safely? Storing it in a
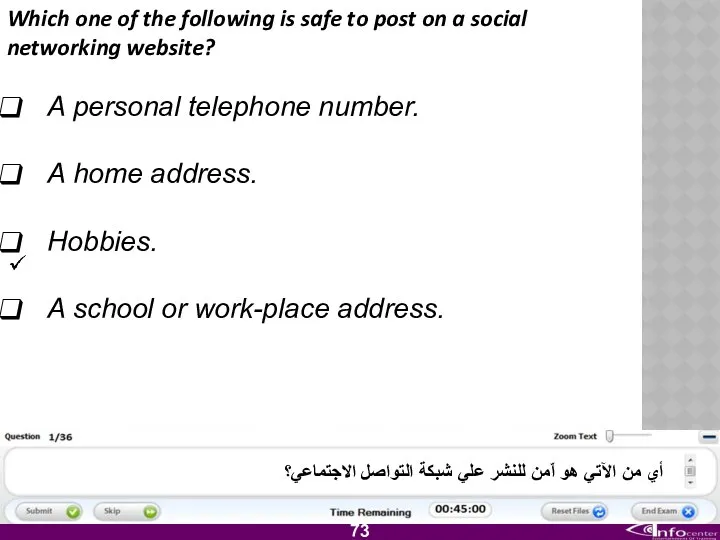
- 74. Which one of the following is safe to post on a social networking website? A personal
- 75. Which one of the following is most likely to cause repetitive strain injury (RSI)? Viewing a
- 76. Computer use can cause repetitive strain injury (RSI). Which of the following is the best way
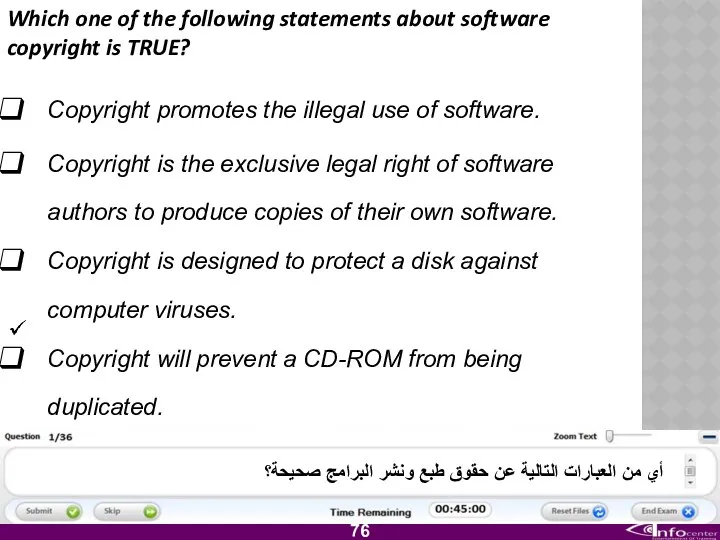
- 77. Which one of the following statements about software copyright is TRUE? Copyright promotes the illegal use
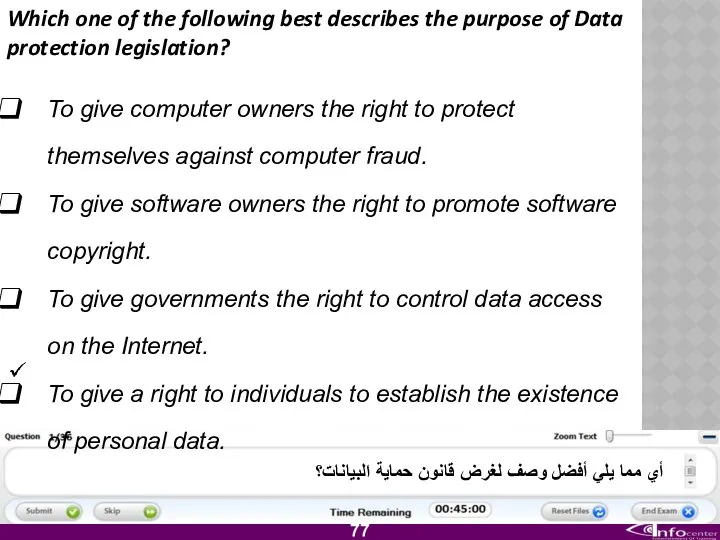
- 78. Which one of the following best describes the purpose of Data protection legislation? To give computer
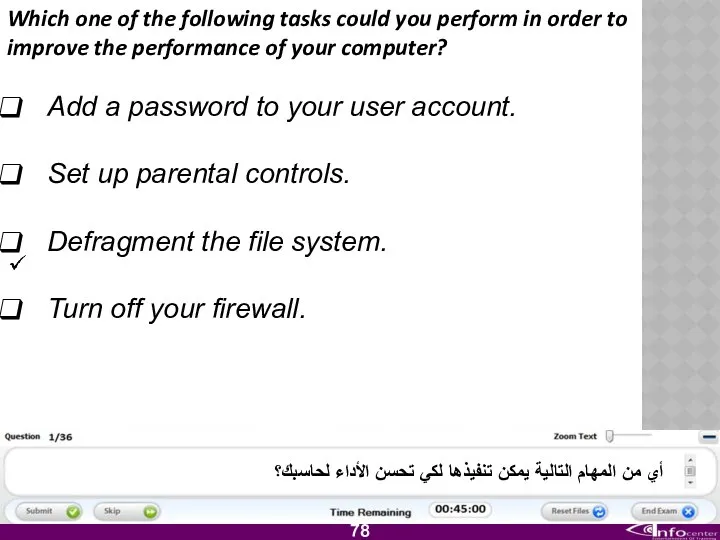
- 79. Which one of the following tasks could you perform in order to improve the performance of
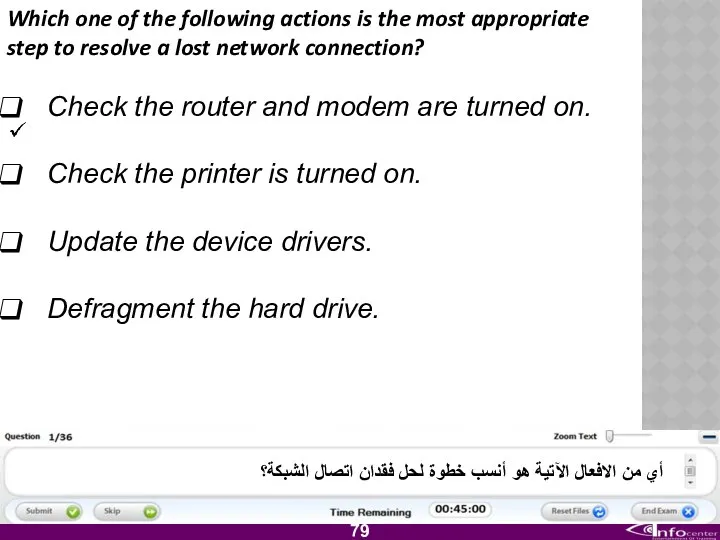
- 80. Which one of the following actions is the most appropriate step to resolve a lost network
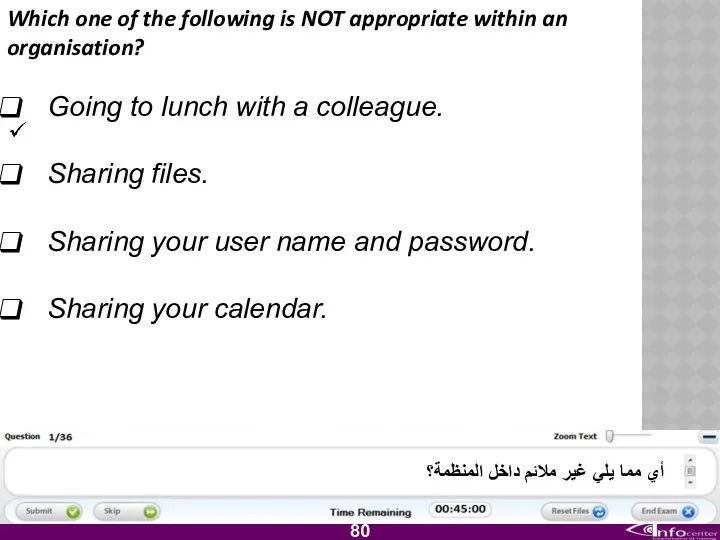
- 81. Which one of the following is NOT appropriate within an organisation? Going to lunch with a
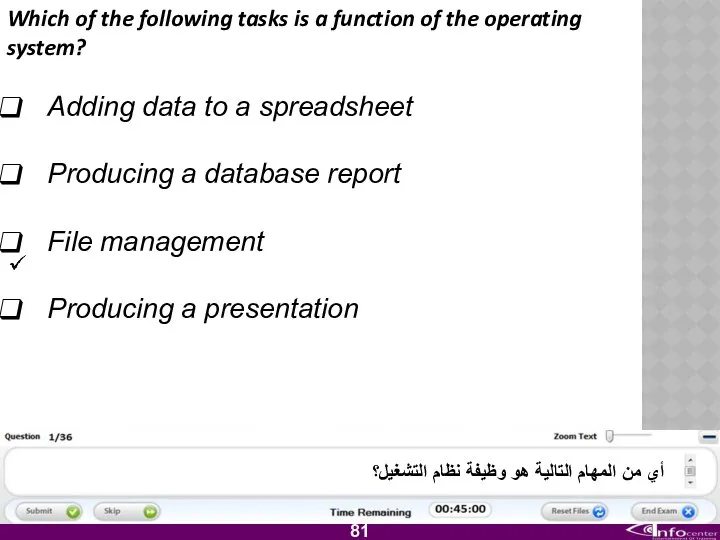
- 82. Which of the following tasks is a function of the operating system? Adding data to a
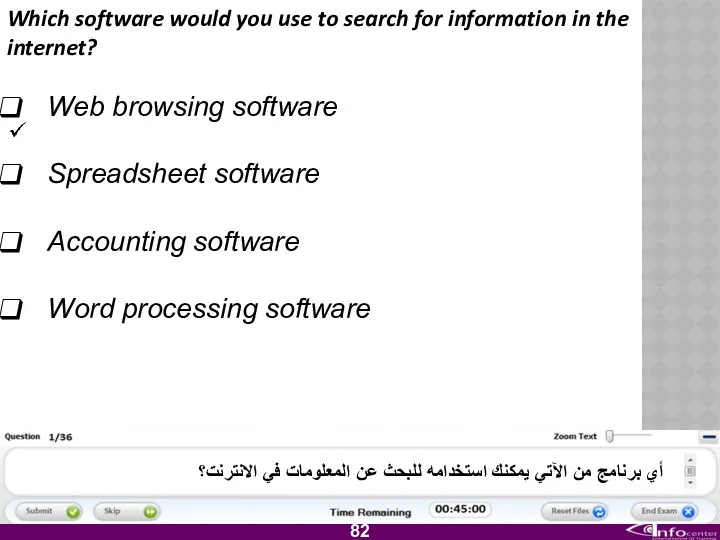
- 83. Which software would you use to search for information in the internet? Web browsing software Spreadsheet
- 84. An intranet is: A network operating system A network filing system A private company network A
- 85. Which of the following tasks would be more suited to a person rather than a computer?
- 86. Which of the following is NOT a use of computer applications in a school? Class timetabling
- 87. What is the best way of preventing your computer from being infected with a virus? Only
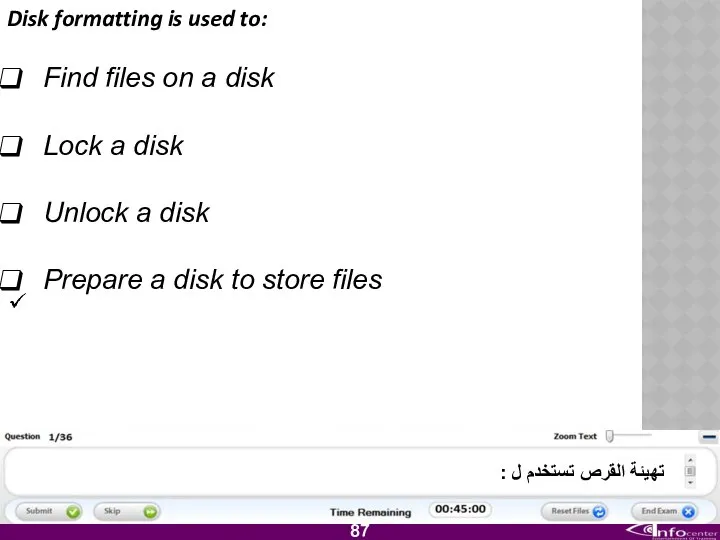
- 88. Disk formatting is used to: Find files on a disk Lock a disk Unlock a disk
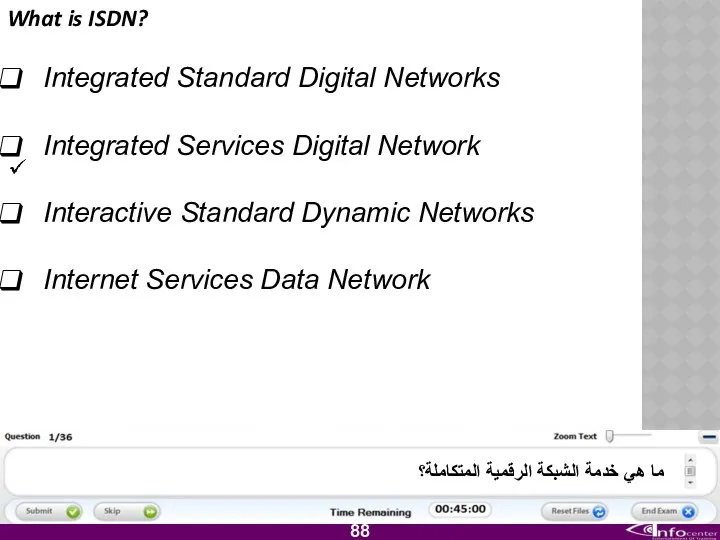
- 89. What is ISDN? Integrated Standard Digital Networks Integrated Services Digital Network Interactive Standard Dynamic Networks Internet
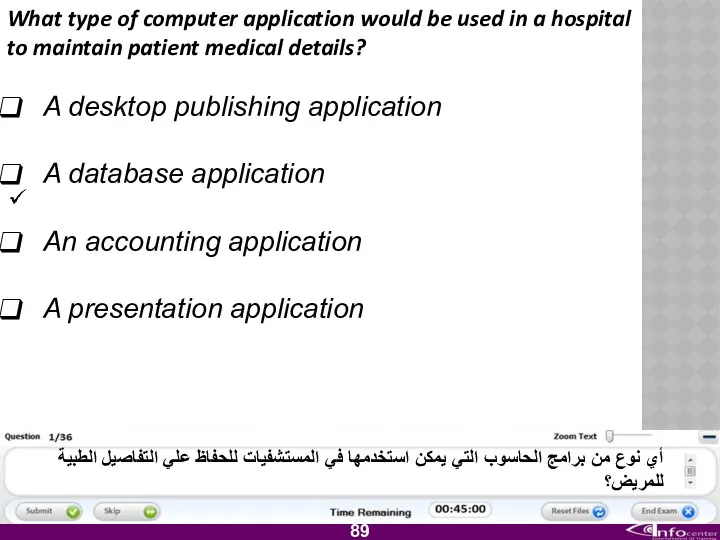
- 90. What type of computer application would be used in a hospital to maintain patient medical details?
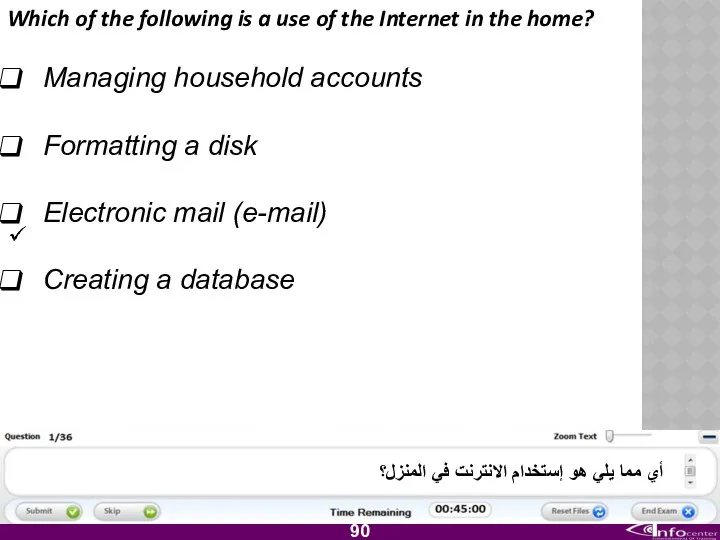
- 91. Which of the following is a use of the Internet in the home? Managing household accounts
- 92. If you were working from home, what software application could be used to communicate directly with
- 93. Which of the following can be an advantage of electronic documents? They can never be lost
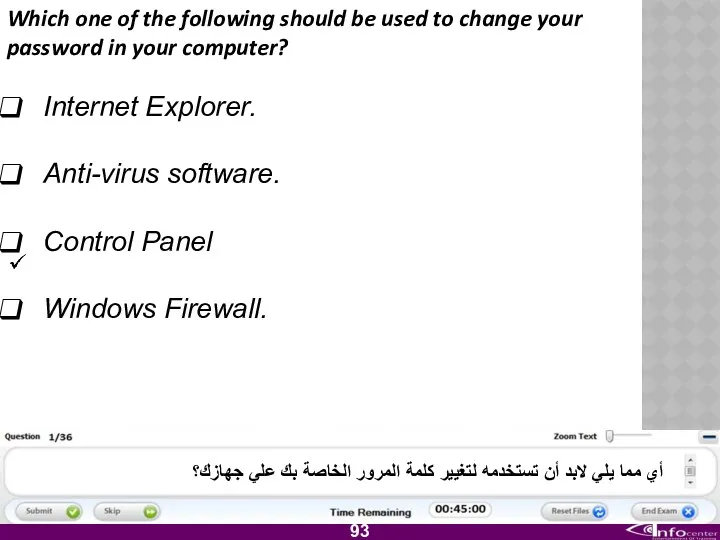
- 94. Which one of the following should be used to change your password in your computer? Internet
- 96. Скачать презентацию


















 Student life
Student life Our teachers are the best
Our teachers are the best Module 3. lesson 3d
Module 3. lesson 3d Презентация At the zoo
Презентация At the zoo The system of the English phonemes Done by Smailova E. 303 group
The system of the English phonemes Done by Smailova E. 303 group Text about landmarks in Russia
Text about landmarks in Russia Fabrics
Fabrics Презентация к уроку английского языка "Лондон" - скачать бесплатно__
Презентация к уроку английского языка "Лондон" - скачать бесплатно__ Презентация к уроку английского языка "Diana - the People's Princess" - скачать
Презентация к уроку английского языка "Diana - the People's Princess" - скачать  Alexei Kondratyevich Savrasov (Russian: Алексе́й Кондра́тьевич Савра́сов)
Alexei Kondratyevich Savrasov (Russian: Алексе́й Кондра́тьевич Савра́сов)  Основной государственный экзамен (ОГЭ) по английскому языку
Основной государственный экзамен (ОГЭ) по английскому языку Предлоги места в английском языке
Предлоги места в английском языке Comparison of adjectives and adverbs
Comparison of adjectives and adverbs Sequence of tenses. Правило согласования (последовательности) времен в сложноподчиненных предложениях
Sequence of tenses. Правило согласования (последовательности) времен в сложноподчиненных предложениях Презентация основные положения кейнсианской теории
Презентация основные положения кейнсианской теории Презентация к уроку английского языка "Царевна лягушка" - скачать бесплатно
Презентация к уроку английского языка "Царевна лягушка" - скачать бесплатно Скачать Zoo tour. Экскурсия в зоопарк
Скачать Zoo tour. Экскурсия в зоопарк Презентация к уроку английского языка "Английский вокруг нас" -
Презентация к уроку английского языка "Английский вокруг нас" -  Special questions in Present Simple
Special questions in Present Simple Repoted speech
Repoted speech Slang. Difference between Jargon, slang and cant
Slang. Difference between Jargon, slang and cant My future profession pharmacist
My future profession pharmacist Конструкция наличия места и отсутствия
Конструкция наличия места и отсутствия England - Foggy Albion
England - Foggy Albion  My family
My family Have got
Have got Wedding ceremony in Great Britain
Wedding ceremony in Great Britain Презентация к уроку английского языка "We are the World" - скачать
Презентация к уроку английского языка "We are the World" - скачать