Содержание
- 2. Outline: Introduction Objectives Methodology Results and conclusion References
- 4. Introduction Cloud computing facilitates enormous support of the public, business and emerging applications.
- 5. Introduction In cloud network environment, the data security is playing crucial roles.
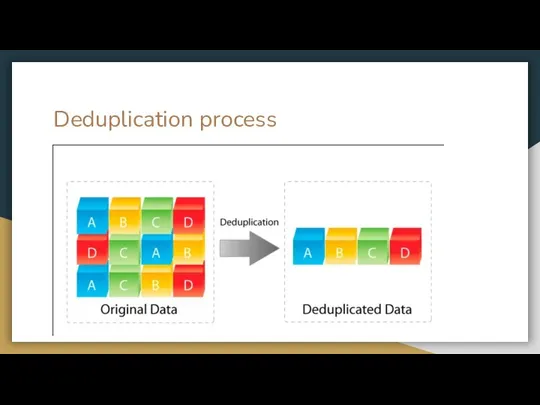
- 6. Deduplication process
- 7. Objectives Introduce a new access control mechanism which is working dynamic in nature that is based
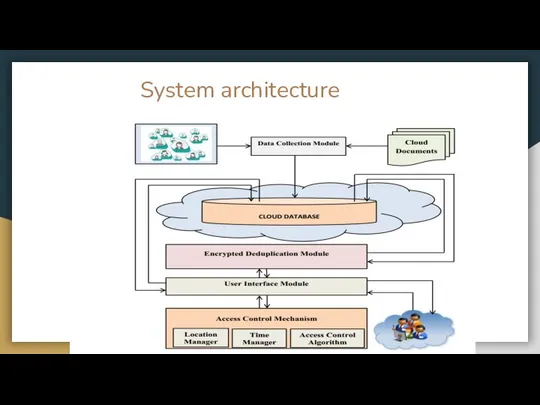
- 8. System architecture
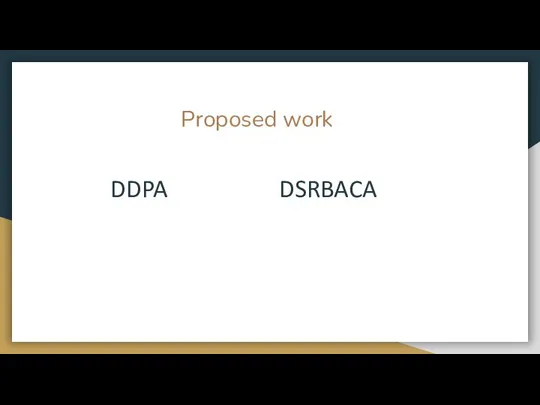
- 9. Proposed work DDPA DSRBACA
- 10. DDPA:
- 11. DDPA:
- 12. Dynamic spatial role based access control algorithm
- 13. DSRBACA:
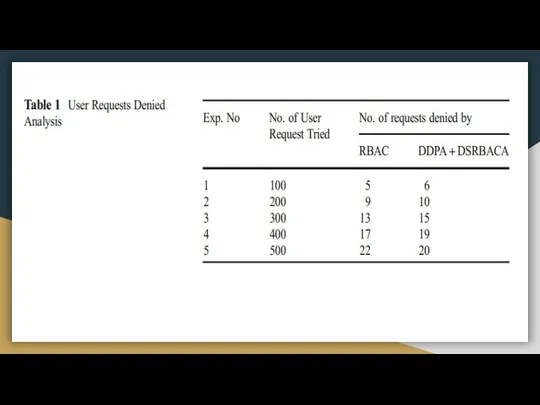
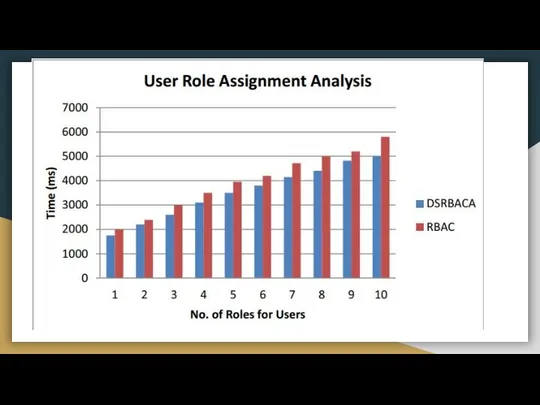
- 16. Results and conclusion A new machine learning application has been developed for providing security to the
- 17. References 1. Alabdulatif A, Kumarage H, Khalil I, Yi X (2017) Privacy-preserving anomaly detection in cloud
- 19. Скачать презентацию







 Предмет, объект и составные части информатики. Системы счисления. (Тема 1)
Предмет, объект и составные части информатики. Системы счисления. (Тема 1) Теория реляционной модели данных
Теория реляционной модели данных Правила и рекомендации службы кибербезопасности (СКБ)
Правила и рекомендации службы кибербезопасности (СКБ) Дмитрий Сотников [MVP] Quest Software
Дмитрий Сотников [MVP] Quest Software  БАЗЫ ДАННЫХ. ИНФОРМАЦИОННЫЕ СИСТЕМЫ Информационные системы Базы данных (БД) Реляционные БД Работа с таблицами Проектировани
БАЗЫ ДАННЫХ. ИНФОРМАЦИОННЫЕ СИСТЕМЫ Информационные системы Базы данных (БД) Реляционные БД Работа с таблицами Проектировани Программист
Программист Паскаль и информатика
Паскаль и информатика Файловые системы. Файловая система NTFS. Общие сведения
Файловые системы. Файловая система NTFS. Общие сведения Big Data. Эксгумация больших данных
Big Data. Эксгумация больших данных Разработка и исследование моделей на компьютере
Разработка и исследование моделей на компьютере Внутренние устройства ПК
Внутренние устройства ПК Память, переменные
Память, переменные Билет в будущее. Обработка фотографий. Создание контента
Билет в будущее. Обработка фотографий. Создание контента Автоматизированная система учёта потребления ресурсов в сфере ЖКХ
Автоматизированная система учёта потребления ресурсов в сфере ЖКХ Программное управление работой компьютера. Язык программирования Паскаль
Программное управление работой компьютера. Язык программирования Паскаль Методы решения творческих задач
Методы решения творческих задач Устройство компьютера для малышей
Устройство компьютера для малышей Решение текстовых логических задач Раздел: алгебра логики и логические основы ПК
Решение текстовых логических задач Раздел: алгебра логики и логические основы ПК  Дисковые накопители для ноутбуков и ПК
Дисковые накопители для ноутбуков и ПК  Методические рекомендации по оформлению стенной печати на курсе
Методические рекомендации по оформлению стенной печати на курсе Стандарты программной инженерии
Стандарты программной инженерии Верстка. Логические блоки. Боевой шаблон для работы
Верстка. Логические блоки. Боевой шаблон для работы Всероссийский семейный флешмоб - челлендж
Всероссийский семейный флешмоб - челлендж Компьютер и его влияние на здоровье человека
Компьютер и его влияние на здоровье человека Язык SQL (DML)
Язык SQL (DML) Video games
Video games Алгоритм и его формальное исполнение
Алгоритм и его формальное исполнение Понятие о локальных сетях
Понятие о локальных сетях