Содержание
- 2. Overview P2P file sharing (cont.) Socket programming with TCP Socket programming with UDP
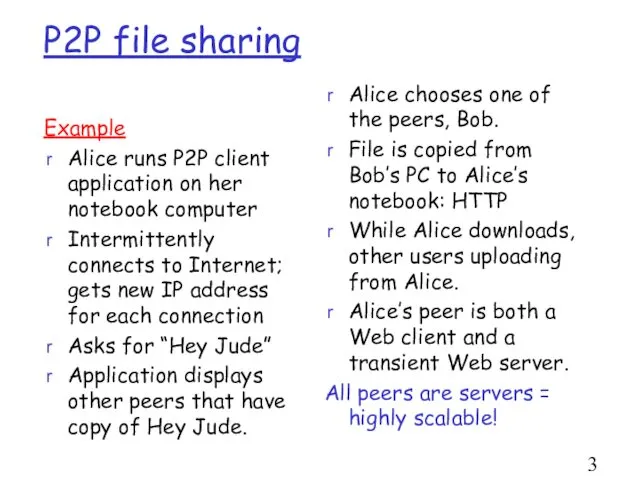
- 3. P2P file sharing Example Alice runs P2P client application on her notebook computer Intermittently connects to
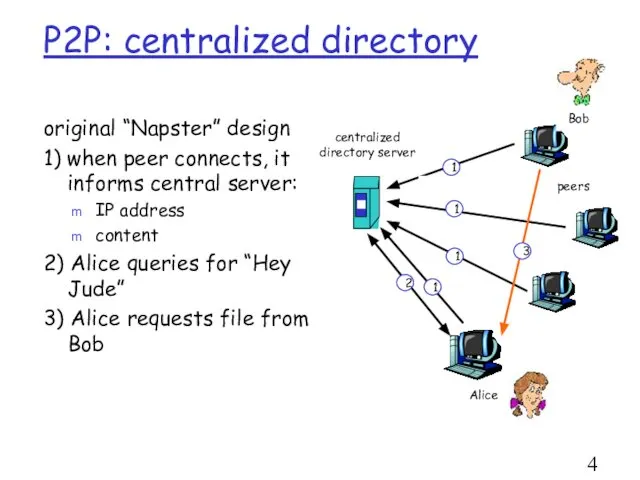
- 4. P2P: centralized directory original “Napster” design 1) when peer connects, it informs central server: IP address
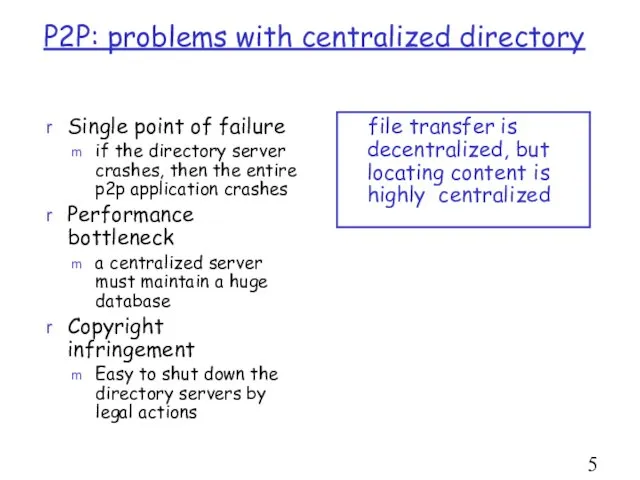
- 5. P2P: problems with centralized directory Single point of failure if the directory server crashes, then the
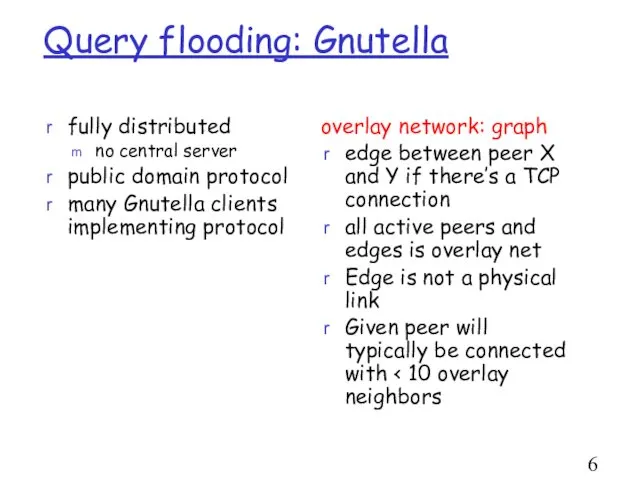
- 6. Query flooding: Gnutella fully distributed no central server public domain protocol many Gnutella clients implementing protocol
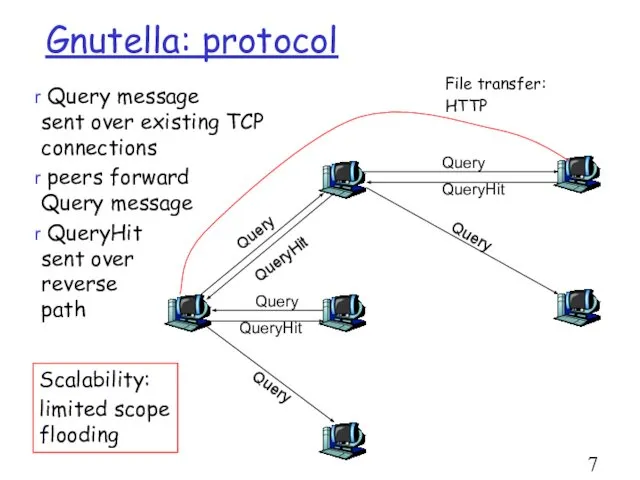
- 7. Gnutella: protocol File transfer: HTTP Query message sent over existing TCP connections peers forward Query message
- 8. Gnutella: Peer joining Joining peer X must find some other peer in Gnutella network: use list
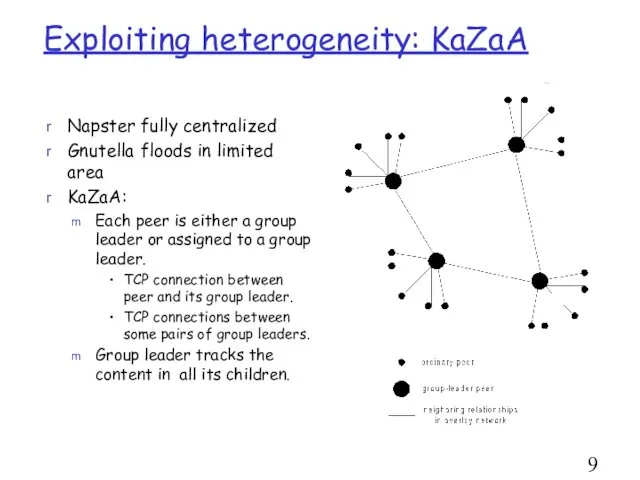
- 9. Exploiting heterogeneity: KaZaA Napster fully centralized Gnutella floods in limited area KaZaA: Each peer is either
- 10. KaZaA: Querying Each file has a hash and a descriptor Client sends keyword query to its
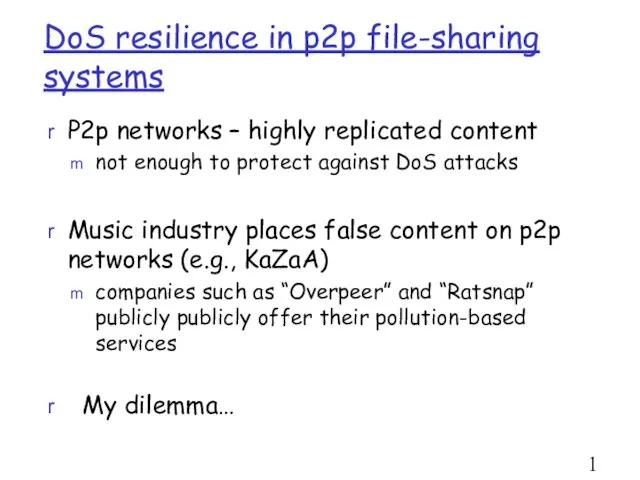
- 11. DoS resilience in p2p file-sharing systems P2p networks – highly replicated content not enough to protect
- 12. DoS resilience in p2p file-sharing systems (cont.) Modeling the propagation of polluted files in the system
- 13. Summary P2P file sharing (cont.) Socket programming with TCP Socket programming with UDP
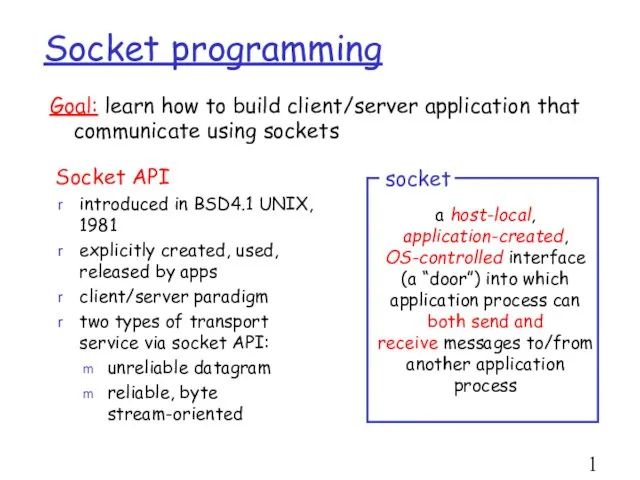
- 14. Socket programming Socket API introduced in BSD4.1 UNIX, 1981 explicitly created, used, released by apps client/server
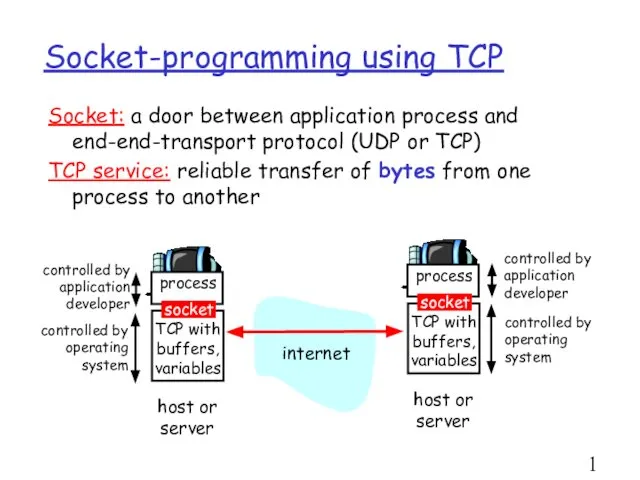
- 15. Socket-programming using TCP Socket: a door between application process and end-end-transport protocol (UDP or TCP) TCP
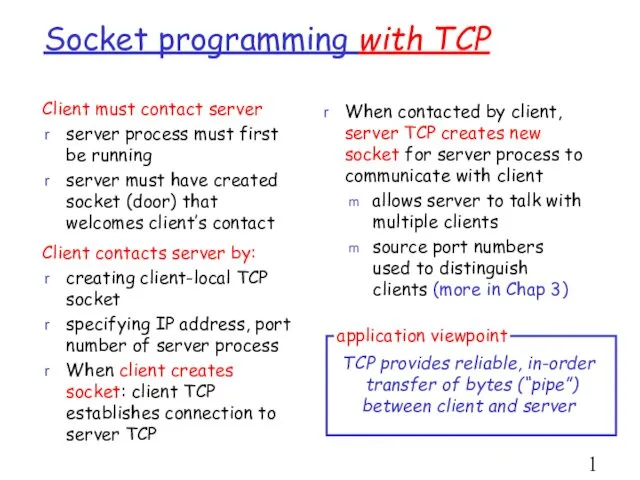
- 16. Socket programming with TCP Client must contact server server process must first be running server must
- 17. Stream jargon A stream is a sequence of characters that flow into or out of a
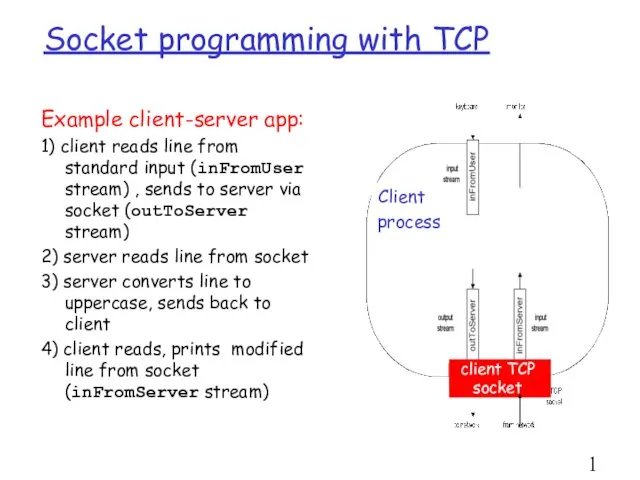
- 18. Socket programming with TCP Example client-server app: 1) client reads line from standard input (inFromUser stream)
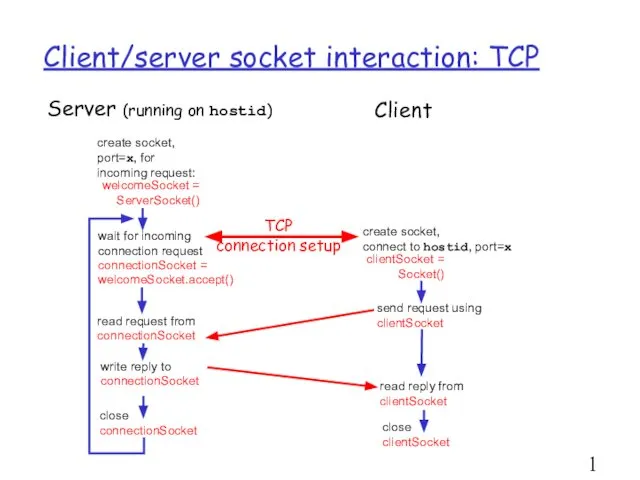
- 19. Client/server socket interaction: TCP Server (running on hostid) Client
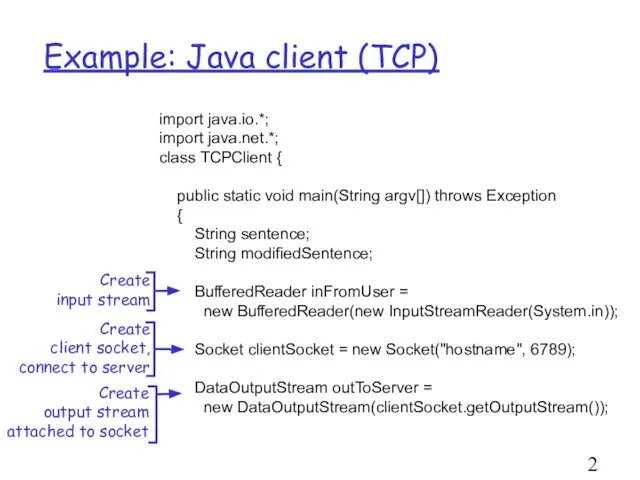
- 20. Example: Java client (TCP) import java.io.*; import java.net.*; class TCPClient { public static void main(String argv[])
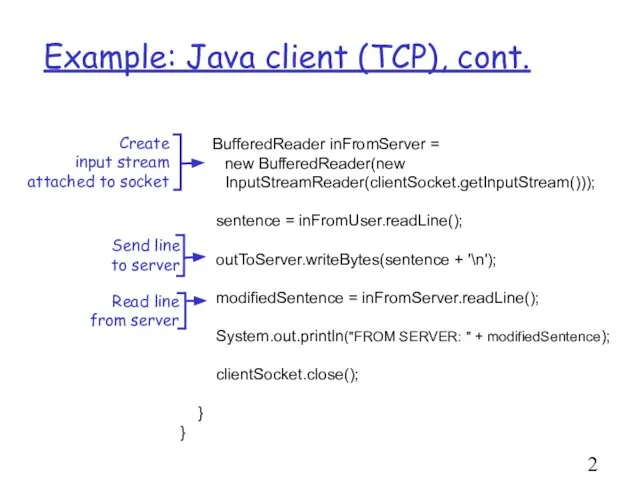
- 21. Example: Java client (TCP), cont. BufferedReader inFromServer = new BufferedReader(new InputStreamReader(clientSocket.getInputStream())); sentence = inFromUser.readLine(); outToServer.writeBytes(sentence +
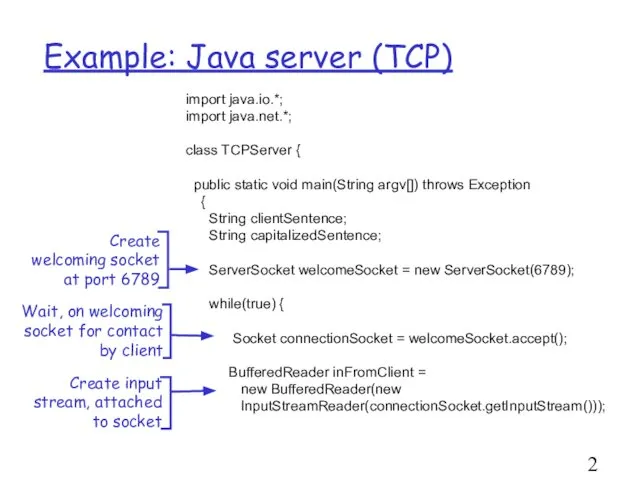
- 22. Example: Java server (TCP) import java.io.*; import java.net.*; class TCPServer { public static void main(String argv[])
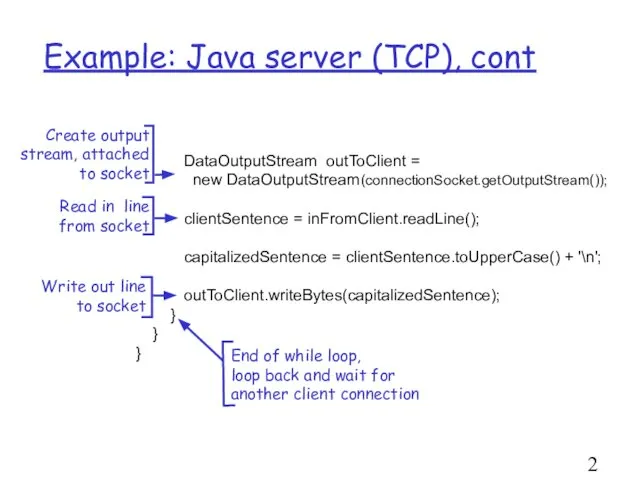
- 23. Example: Java server (TCP), cont DataOutputStream outToClient = new DataOutputStream(connectionSocket.getOutputStream()); clientSentence = inFromClient.readLine(); capitalizedSentence = clientSentence.toUpperCase()
- 24. Outline P2P file sharing (cont.) Socket programming with TCP Socket programming with UDP
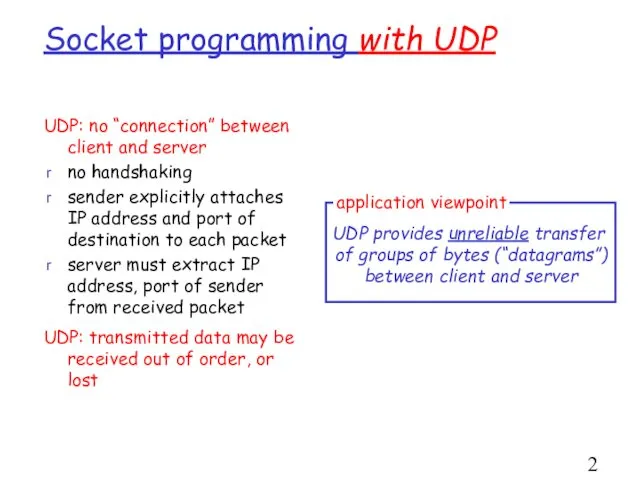
- 25. Socket programming with UDP UDP: no “connection” between client and server no handshaking sender explicitly attaches
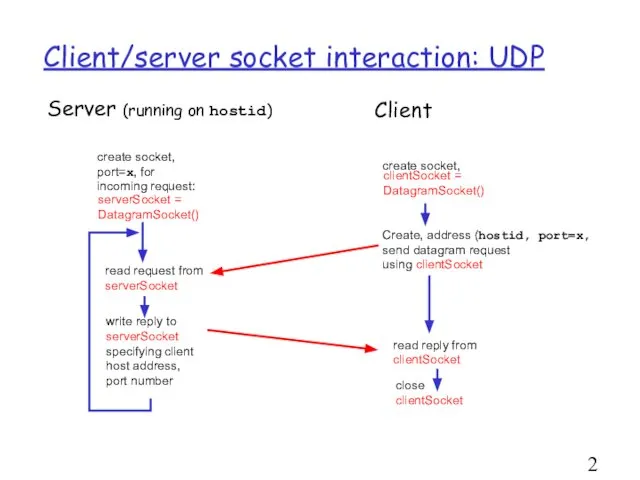
- 26. Client/server socket interaction: UDP Server (running on hostid)
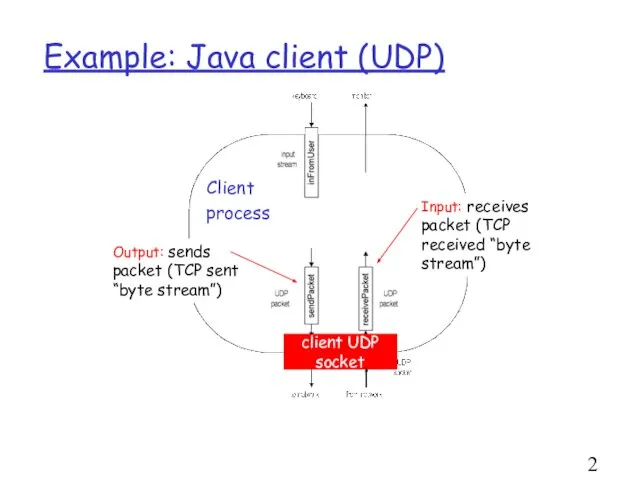
- 27. Example: Java client (UDP) Output: sends packet (TCP sent “byte stream”) Input: receives packet (TCP received
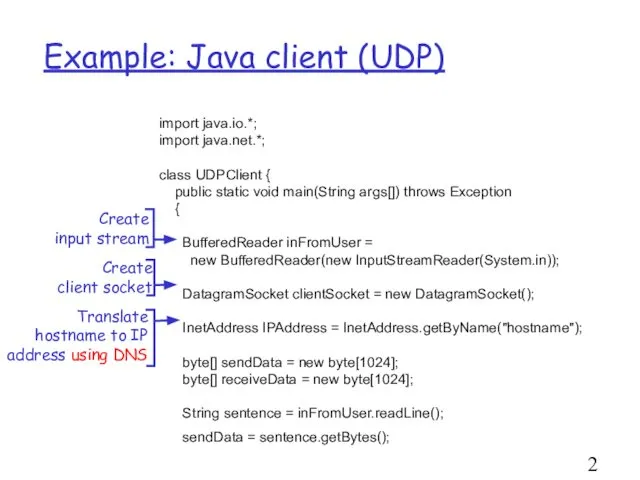
- 28. Example: Java client (UDP) import java.io.*; import java.net.*; class UDPClient { public static void main(String args[])
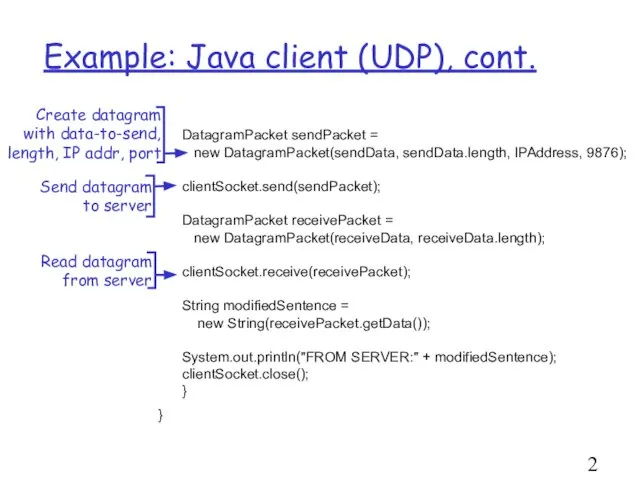
- 29. Example: Java client (UDP), cont. DatagramPacket sendPacket = new DatagramPacket(sendData, sendData.length, IPAddress, 9876); clientSocket.send(sendPacket); DatagramPacket receivePacket
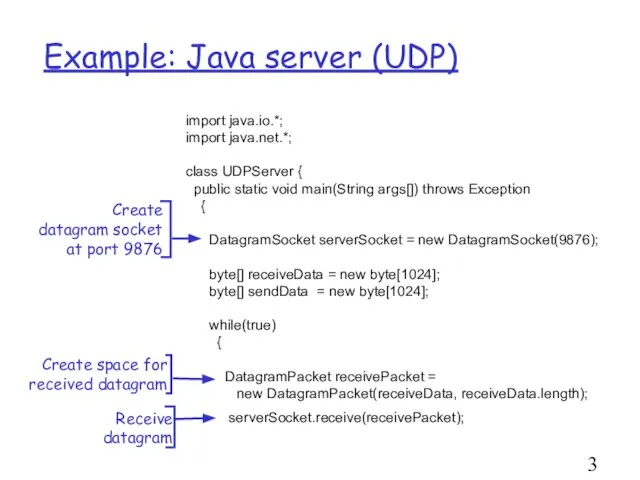
- 30. Example: Java server (UDP) import java.io.*; import java.net.*; class UDPServer { public static void main(String args[])
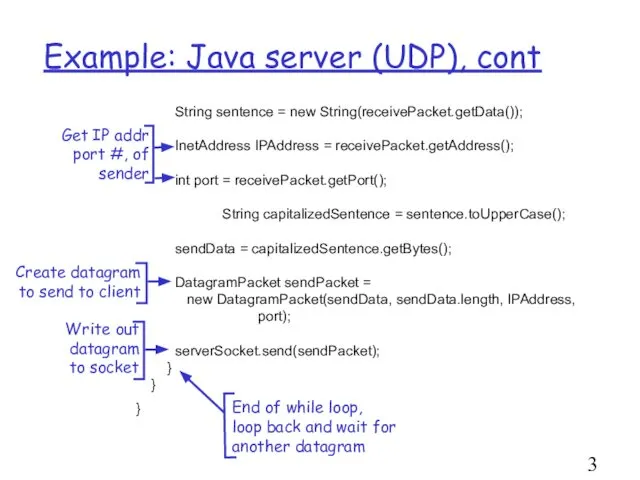
- 31. Example: Java server (UDP), cont String sentence = new String(receivePacket.getData()); InetAddress IPAddress = receivePacket.getAddress(); int port
- 32. Summary P2P file sharing (cont.) Socket programming with TCP Socket programming with UDP
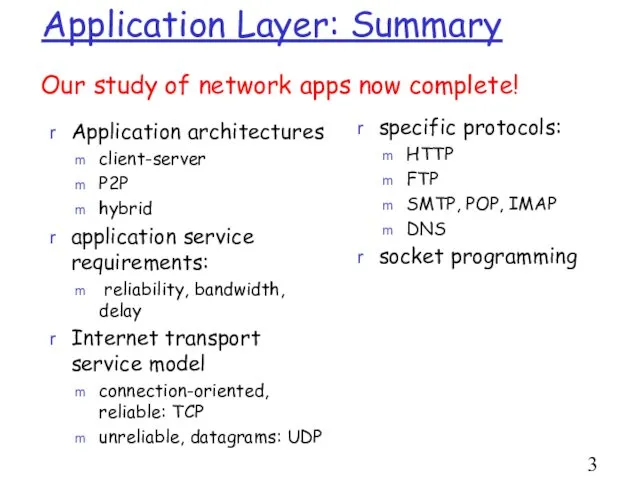
- 33. Application Layer: Summary Application architectures client-server P2P hybrid application service requirements: reliability, bandwidth, delay Internet transport
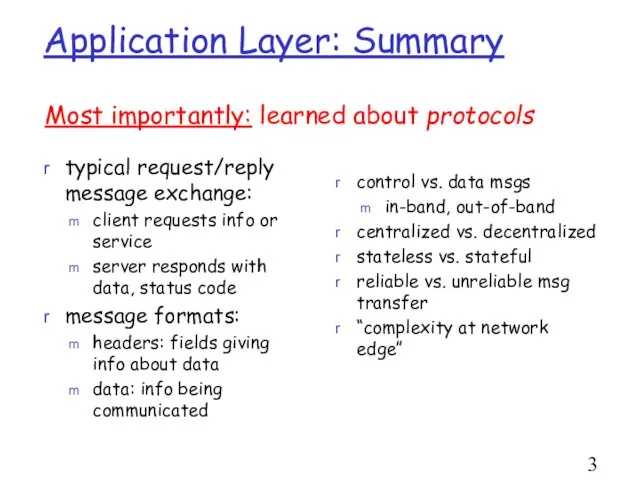
- 34. Application Layer: Summary typical request/reply message exchange: client requests info or service server responds with data,
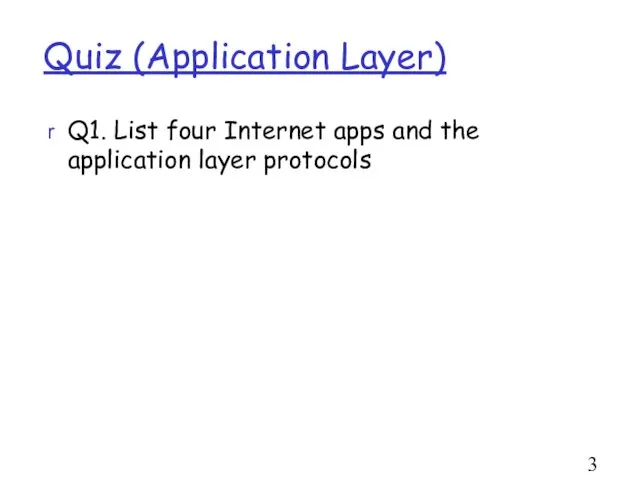
- 35. Quiz (Application Layer) Q1. List four Internet apps and the application layer protocols
- 36. Quiz Q2. What is the difference between network architecture and application architecture?
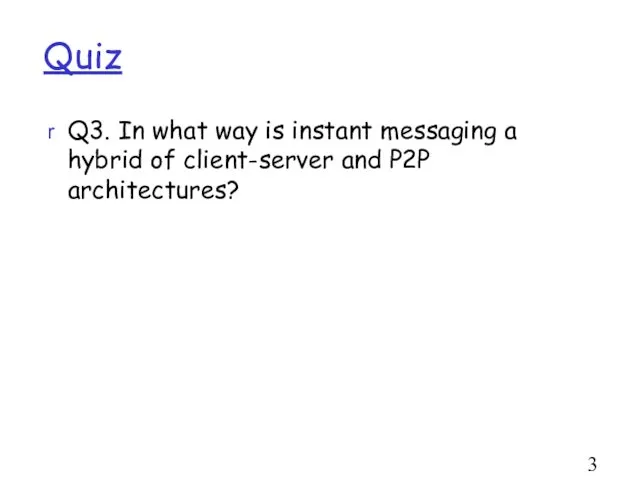
- 37. Quiz Q3. In what way is instant messaging a hybrid of client-server and P2P architectures?
- 38. Quiz Q4. For a communication session between a pair of processes, which process is the client
- 39. Quiz Q5. Do you agree with the statement: “In P2p file sharing, there is no notion
- 40. Quiz Q6. What information is used by a process running on one host to identify a
- 41. Quiz Q9. What is meant by a handshaking protocol?
- 42. Quiz Q10. Why HTTP, FTP, SMTP, POP3, and IMAP run on top of TCP rather than
- 43. Quiz Q12. What is the difference between persistent HTTP with pipelining and persistent HTTP without pipelining?
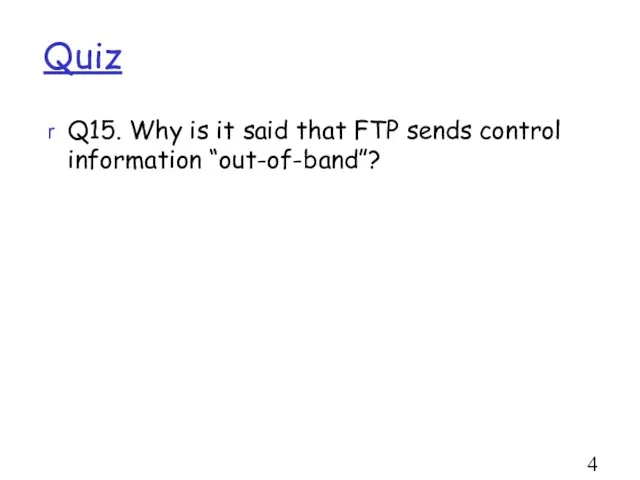
- 44. Quiz Q15. Why is it said that FTP sends control information “out-of-band”?
- 45. Quiz Q19. Is it possible for an organization’s Web server and mail server to have exactly
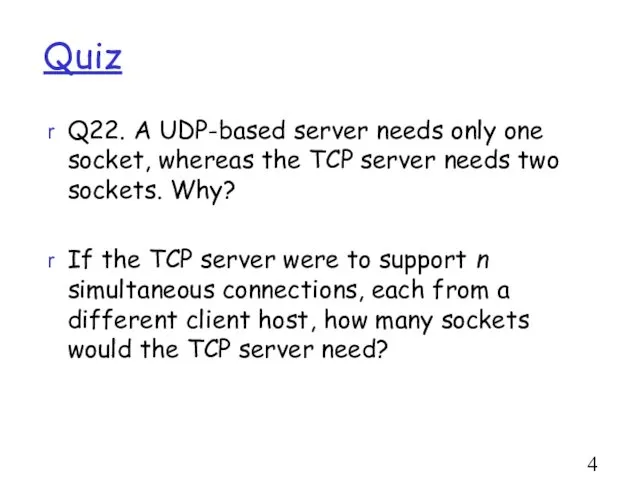
- 46. Quiz Q22. A UDP-based server needs only one socket, whereas the TCP server needs two sockets.
- 47. Quiz (Chapter 1) Q3. What is a client program? What is a server program? Does a
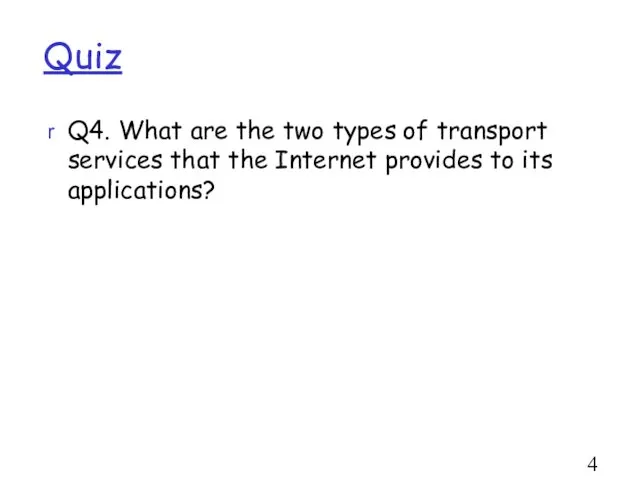
- 48. Quiz Q4. What are the two types of transport services that the Internet provides to its
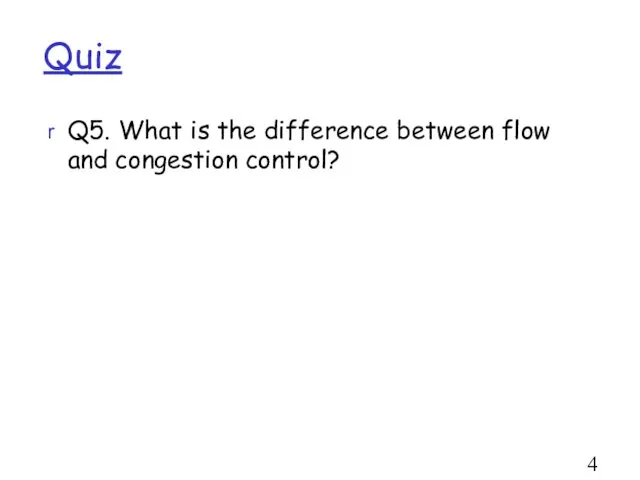
- 49. Quiz Q5. What is the difference between flow and congestion control?
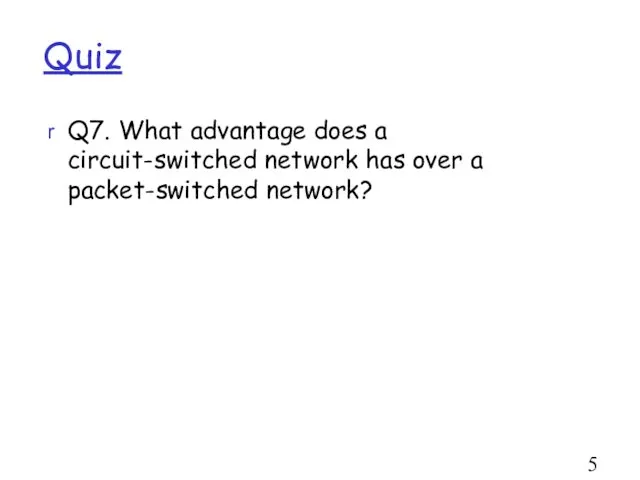
- 50. Quiz Q7. What advantage does a circuit-switched network has over a packet-switched network?
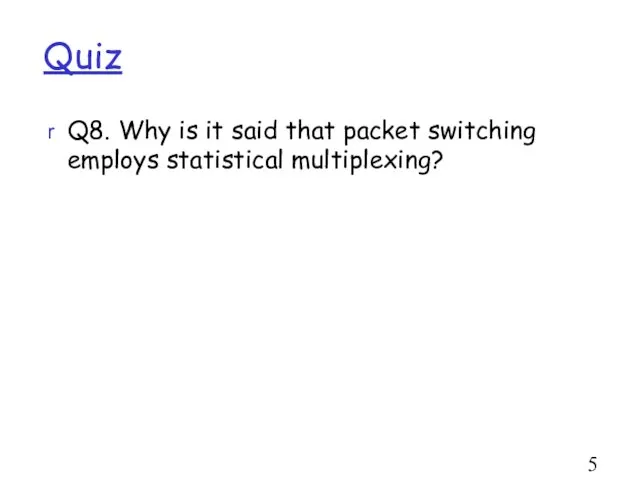
- 51. Quiz Q8. Why is it said that packet switching employs statistical multiplexing?
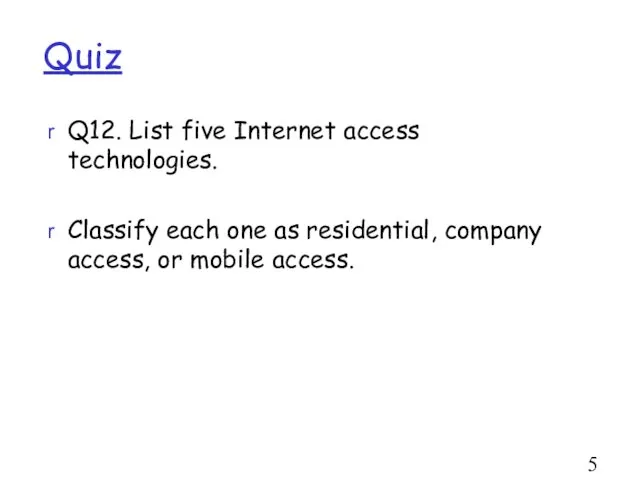
- 52. Quiz Q12. List five Internet access technologies. Classify each one as residential, company access, or mobile
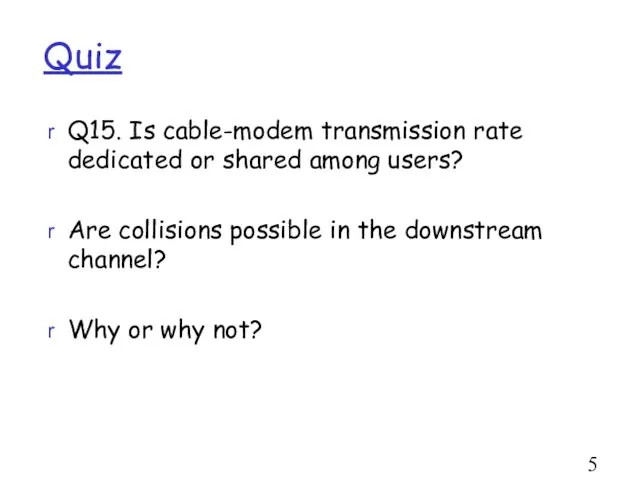
- 53. Quiz Q15. Is cable-modem transmission rate dedicated or shared among users? Are collisions possible in the
- 54. Quiz Q19. Consider sending packet from a sending host to a receiving host over a fixed
- 55. Quiz Q21. What are the five layers in the Internet protocol stack?
- 57. Скачать презентацию













 Презентация "Информация в обществе и технике" - скачать презентации по Информатике
Презентация "Информация в обществе и технике" - скачать презентации по Информатике Методики застосування інтернет-ресурсів у дистанційному навчанні
Методики застосування інтернет-ресурсів у дистанційному навчанні Лекция Криптосистемы с открытым ключем Лектор: профессор Яковлев В.А.
Лекция Криптосистемы с открытым ключем Лектор: профессор Яковлев В.А. МОУ СОШ с УИОП г. Кирс Верхнекамского района Стаж работы - 34года Высшая категория Почетный работник общего образован
МОУ СОШ с УИОП г. Кирс Верхнекамского района Стаж работы - 34года Высшая категория Почетный работник общего образован Алгоритм
Алгоритм О чём может рассказать библиотека
О чём может рассказать библиотека היררכיה נכונה באתר – מחקר מילות מפתח -זנב ארוך
היררכיה נכונה באתר – מחקר מילות מפתח -זנב ארוך Робота з базами даних
Робота з базами даних Скрытые виды. Проблемы представления в базе данных
Скрытые виды. Проблемы представления в базе данных Презентация "Информация и информационные процессы." - скачать презентации по Информатике_
Презентация "Информация и информационные процессы." - скачать презентации по Информатике_ Основы программирования. Представление данных в памяти
Основы программирования. Представление данных в памяти Checker Framework. Аннотации для статического анализа кода
Checker Framework. Аннотации для статического анализа кода Оптимизация и публикация статей. РСЯ-Марафон. (Занятие 3)
Оптимизация и публикация статей. РСЯ-Марафон. (Занятие 3) Компоненты Angular. Занятие №3-4
Компоненты Angular. Занятие №3-4 Техническая защита информации и компьютерной безопасности
Техническая защита информации и компьютерной безопасности Безопасность школьников в сети интернета
Безопасность школьников в сети интернета Совершенствование организации и управления системы общественного пассажирского транспорта г. Волгограда
Совершенствование организации и управления системы общественного пассажирского транспорта г. Волгограда Информационное взаимодействие в сфере обязательного медицинского страхования
Информационное взаимодействие в сфере обязательного медицинского страхования Алгоритмы и программирование, язык Паскаль (часть 2)
Алгоритмы и программирование, язык Паскаль (часть 2) Архитектура операционных систем. Определение операционной системы
Архитектура операционных систем. Определение операционной системы Информация, информирование и информационные системы ОВД
Информация, информирование и информационные системы ОВД ПАСКАЛЬ
ПАСКАЛЬ Презентация "Человек и информация 8 класс" - скачать презентации по Информатике
Презентация "Человек и информация 8 класс" - скачать презентации по Информатике Мова HTML. Створення галереї засобами CSS
Мова HTML. Створення галереї засобами CSS Создание объектов в 3d max. Задание 2
Создание объектов в 3d max. Задание 2 Результаты контент-анализа транслирования образа Беларуси в российском СМИ
Результаты контент-анализа транслирования образа Беларуси в российском СМИ Блочная вёрстка
Блочная вёрстка Введение. Этапы развития информационного общества, технических средств и информационных ресурсов
Введение. Этапы развития информационного общества, технических средств и информационных ресурсов