Содержание
- 2. Me Software Engineer at Honeywell This presentation in no way represents my employer or what I
- 3. Research Note Mifare Plus Cracking This presentation does not disclose any new vulnerabilities, simply builds on
- 4. Mifare Classic simple storage device read/write access permissions per block via keys e-wallet, access control, transportation,
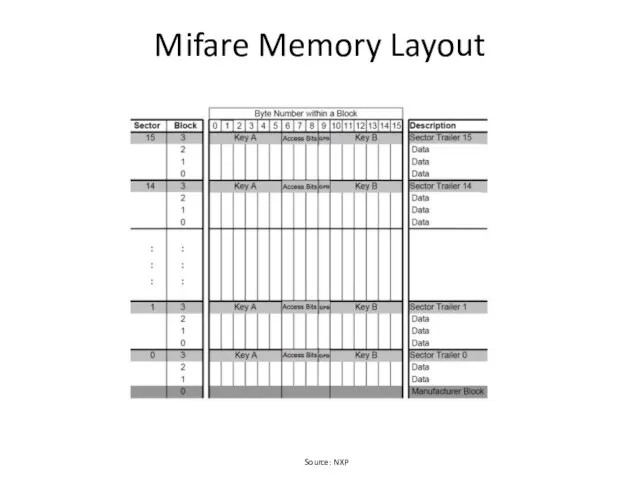
- 5. Mifare Memory Layout Source: NXP
- 6. Mifare Classic Attacks – Card Only Open source NFC tools for Mifare Classic MFOC (Nested Attack)
- 7. Response to Attacks Backwards compatible with Mifare Classic (uses CRYPTO1 as well) IMG URL: https://www.pinterest.com/pin/440297301040955293/ Fixed
- 8. Researchers Response Carlo Meijer and Roel Verdult http://www.cs.ru.nl/~rverdult/Ciphertext-only_Cryptanalysis_on_Hardened_Mifare_Classic_Cards-CCS_2015.pdf Found new card-only attacks (Mifare Plus SL1) Important
- 9. My Goals Reproduce the attack Get the proper hardware and software Improve attack / easier to
- 10. Hardware and Tools SCL3711 (~$30) Proxmark3 ($212) Mifare Plus Cards (~$75) Mifare Reader (~$50) Config Software
- 11. The Hardnested Attack Nested attacked on hardened cards = “hardnested” Requires at least one known key
- 12. What did I actually do? Improving the attack was difficult People a lot smarter than me
- 13. Are you lazy? Everyone is lazy Lets make this easy: Don’t know if you have a
- 14. miLazyCracker modified LibNFC version of MFOC to ID the PRNG Modified LibNFC version of hardnested attack
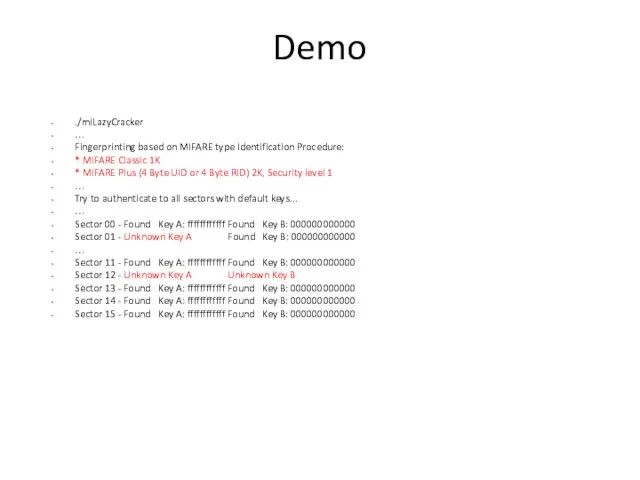
- 15. Demo ./miLazyCracker … Fingerprinting based on MIFARE type Identification Procedure: * MIFARE Classic 1K * MIFARE
- 16. Demo (cont.) PRNG is not vulnerable to nested attack MFOC not possible, detected hardened Mifare Classic
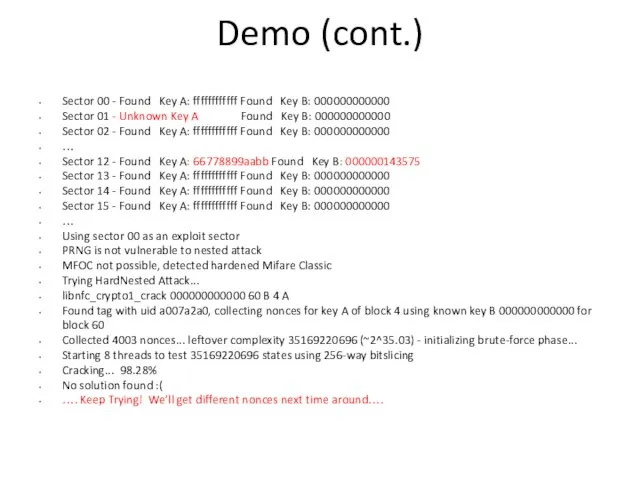
- 17. Demo (cont.) Sector 00 - Found Key A: ffffffffffff Found Key B: 000000000000 Sector 01 -
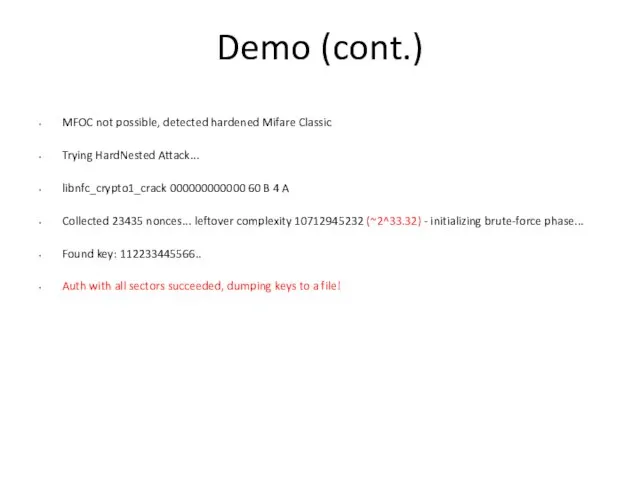
- 18. Demo (cont.) MFOC not possible, detected hardened Mifare Classic Trying HardNested Attack... libnfc_crypto1_crack 000000000000 60 B
- 19. Source Code Released https://github.com/iAmNotSuperman/miLazyCracker/
- 20. Remediation DO NOT USE CUSTOM CRYPTO Mifare Classic should be avoided ** Mifare Plus SL2 and
- 22. Скачать презентацию













 Что наша жизнь?... Игра "Сто к одному"
Что наша жизнь?... Игра "Сто к одному" Этика сетевого общения
Этика сетевого общения История развития вычислительной техники от абака до компьютера
История развития вычислительной техники от абака до компьютера Мультимедийнные технологии в среде PowerPoint 2007
Мультимедийнные технологии в среде PowerPoint 2007 Fundamental test process
Fundamental test process Понятие о динамических данных. Работа с динамическими массивами
Понятие о динамических данных. Работа с динамическими массивами Презентация "Манипуляторы" - скачать презентации по Информатике
Презентация "Манипуляторы" - скачать презентации по Информатике Операционные системы
Операционные системы Аттестационная работа. Оформление кабинета технологии с помощью компьютера
Аттестационная работа. Оформление кабинета технологии с помощью компьютера Экспертные системы. Принятие решений в системах ЗИ на основе нечеткой логики. Лекция 3
Экспертные системы. Принятие решений в системах ЗИ на основе нечеткой логики. Лекция 3 Построение нетривиальных запросов. Лекция 7
Построение нетривиальных запросов. Лекция 7 Разработка программного модуля для учета штатного состава сотрудников на примере МАОУ Средняя общеобразовательная школа №21
Разработка программного модуля для учета штатного состава сотрудников на примере МАОУ Средняя общеобразовательная школа №21 Photoshop
Photoshop Программирование на языке Python
Программирование на языке Python Ms Project 2013. Просмотр отчетов
Ms Project 2013. Просмотр отчетов Как настроить The bat. The Bat - популярная почтовая программа
Как настроить The bat. The Bat - популярная почтовая программа Критерии оценки методов защиты информации
Критерии оценки методов защиты информации Журналистика как вид деятельности
Журналистика как вид деятельности Робота з кластером ІФКС
Робота з кластером ІФКС История создания сети. Компьютерные сети
История создания сети. Компьютерные сети Зарубежные информационные ресурсы негуманитарных отраслей науки и практики. (Тема 4)
Зарубежные информационные ресурсы негуманитарных отраслей науки и практики. (Тема 4) Основные логические операции
Основные логические операции Базы данных
Базы данных Проектирование системы видеонаблюдения с передачей данных по Wi-Fi
Проектирование системы видеонаблюдения с передачей данных по Wi-Fi Развивающая игра Прочитай по первым буквам. Часть 2 Слова из 4 букв
Развивающая игра Прочитай по первым буквам. Часть 2 Слова из 4 букв Устройства ввода и вывода информации
Устройства ввода и вывода информации Стандартные функции
Стандартные функции Презентация "Техника безопасности и организация рабочего места при работе на ПК" - скачать презентации по Информатике
Презентация "Техника безопасности и организация рабочего места при работе на ПК" - скачать презентации по Информатике