Содержание
- 2. $WHOAMI Penetration Tester @ SynerComm Bug Bounty Hunter on HackerOne Python enthusiast @Rhynorater @Rhynorater jgardner@synercomm.com
- 3. 5 ROUTES TO DA … and how to protect your administrators
- 4. PERMISSIVE GLOBAL GROUP ACCESS + MIMIKATZ Solution: Apply the principle of least privilege
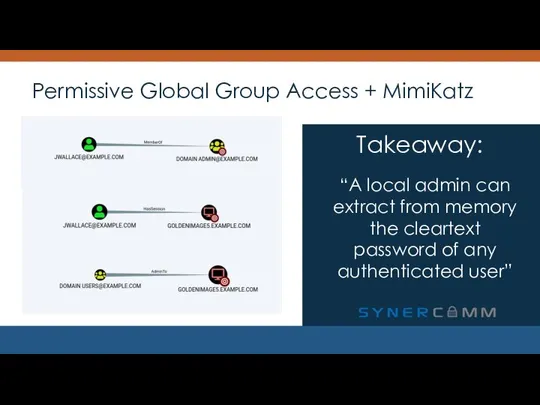
- 5. Permissive Global Group Access + MimiKatz Takeaway:
- 6. Permissive Global Group Access + MimiKatz “A local admin can extract from memory the cleartext password
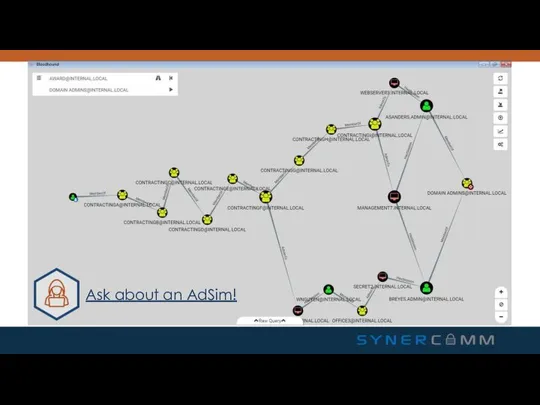
- 7. BloodHound Available on GitHub @BloodhoundAD 10 minute setup Queries DC and domain computer for session and
- 8. Ask about an AdSim!
- 9. Permissive Global Group Access + MimiKatz “A local admin can extract from memory the cleartext password
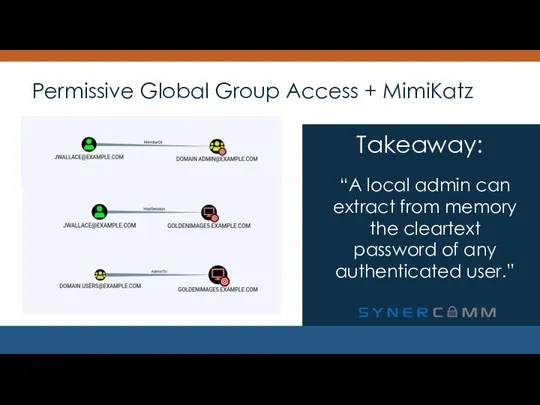
- 10. Permissive Global Group Access + MimiKatz “A local admin can extract from memory the cleartext password
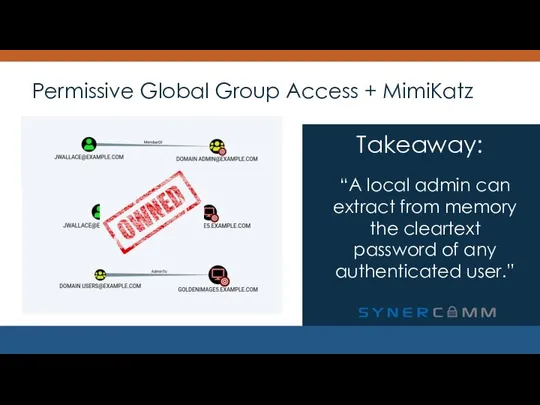
- 11. Permissive Global Group Access + MimiKatz “A local admin can extract from memory the cleartext password
- 12. LLMNR & NBT-NS POISONING Solution: Turn them off.
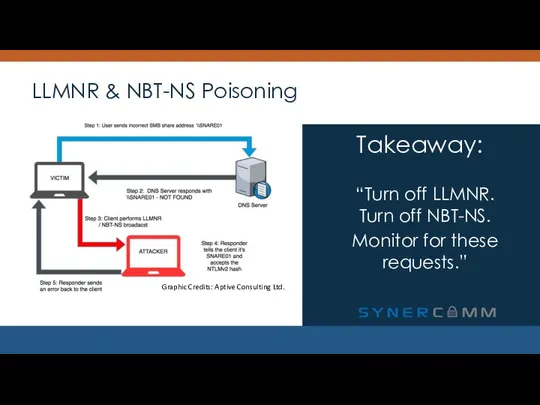
- 13. LLMNR & NBT-NS Poisoning “Turn off LLMNR. Turn off NBT-NS. Monitor for these requests.” Takeaway: Graphic
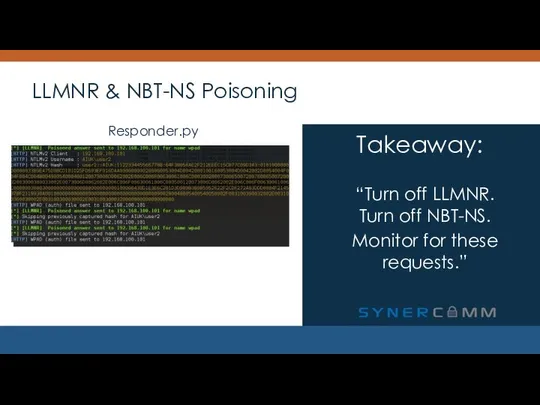
- 14. LLMNR & NBT-NS Poisoning “Turn off LLMNR. Turn off NBT-NS. Monitor for these requests.” Takeaway: Responder.py
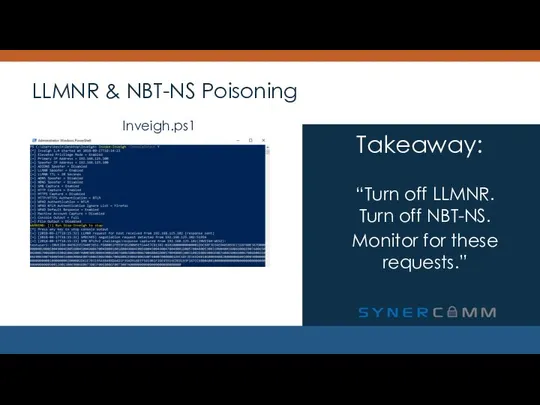
- 15. LLMNR & NBT-NS Poisoning “Turn off LLMNR. Turn off NBT-NS. Monitor for these requests.” Takeaway: Inveigh.ps1
- 16. LLMNR & NBT-NS Poisoning “Turn off LLMNR. Turn off NBT-NS. Monitor for these requests.” Takeaway: The
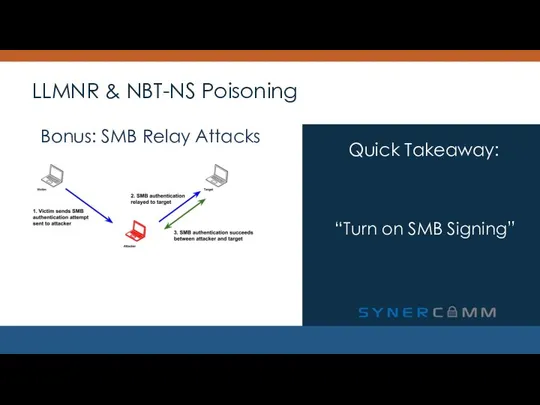
- 17. LLMNR & NBT-NS Poisoning “Turn on SMB Signing” Quick Takeaway: Bonus: SMB Relay Attacks
- 18. SYSVOL PASSWORDS + LEAKED AES KEYS Solution: Delete the XML files. Just delete them.
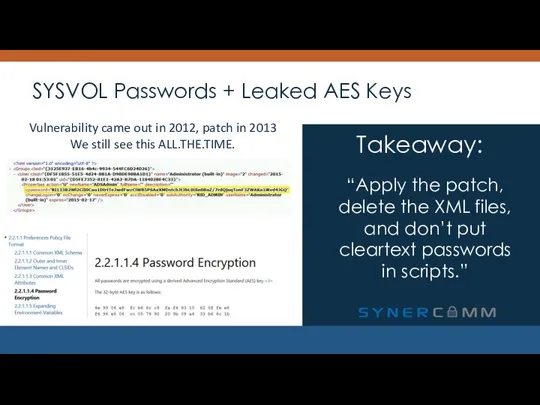
- 19. SYSVOL Passwords + Leaked AES Keys “Apply the patch, delete the XML files, and don’t put
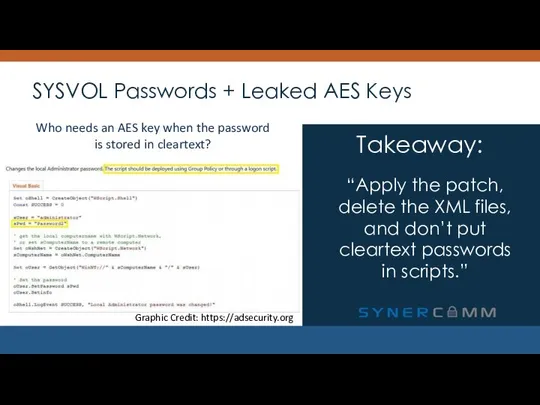
- 20. SYSVOL Passwords + Leaked AES Keys “Apply the patch, delete the XML files, and don’t put
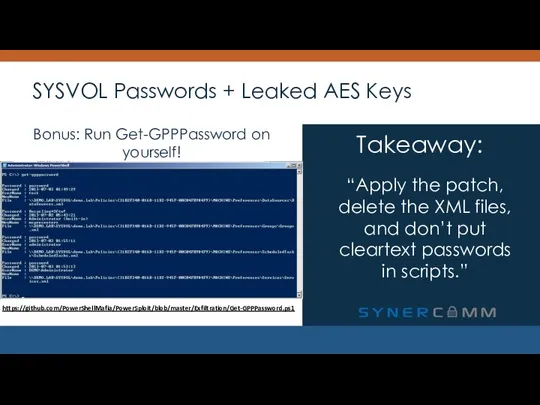
- 21. SYSVOL Passwords + Leaked AES Keys “Apply the patch, delete the XML files, and don’t put
- 22. SYSVOL Passwords + Leaked AES Keys “Apply the patch, delete the XML files, and don’t put
- 23. KERBEROASTING Solution: Long Service Account Passwords
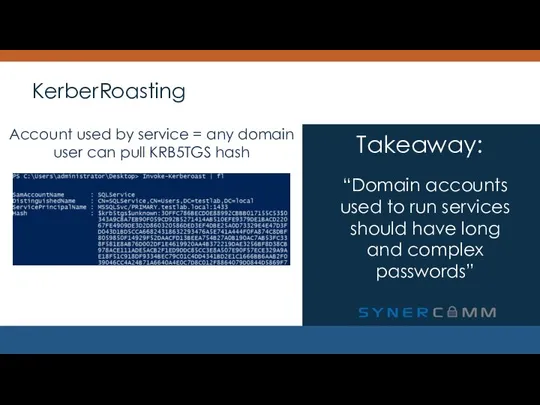
- 24. KerberRoasting “Domain accounts used to run services should have long and complex passwords” Takeaway: Account used
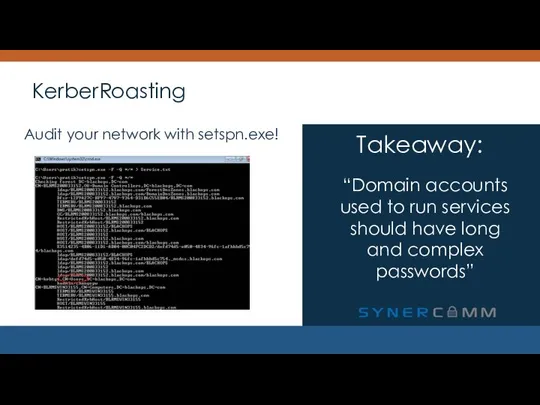
- 25. KerberRoasting “Domain accounts used to run services should have long and complex passwords” Takeaway: Audit your
- 26. DC BACKUPS Solution: Ensure no one but Domain Admins can access your DC backups
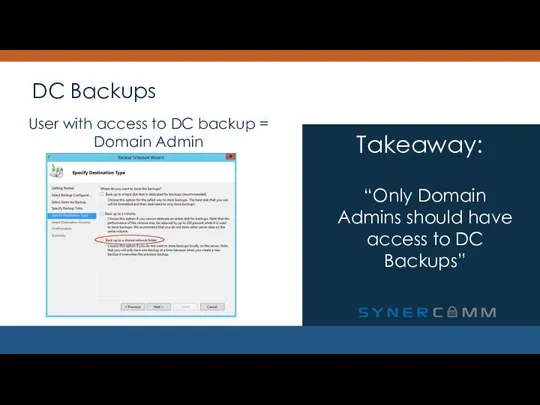
- 27. DC Backups “Only Domain Admins should have access to DC Backups” Takeaway: User with access to
- 28. Takeaways A local admin can extract from memory the cleartext password of any authenticated user Turn
- 29. DA101 - Kit https://www.SHELLNTELL.com/blog/da-101 Question or Help? Justin Gardner – jgardner@synercomm.com
- 31. Скачать презентацию












 О специальной оценке условий труда
О специальной оценке условий труда Терроризм - угроза обществу
Терроризм - угроза обществу Влияние никотина и алкоголя на организм человека
Влияние никотина и алкоголя на организм человека Презентация ПРАВИЛА ДОРОЖНОГО ДВИЖЕНИЯ И СТАТИСТИКА ДОРОЖНО-ТРАНСПОРТНЫХ ПРОИСШЕСТВИЙ
Презентация ПРАВИЛА ДОРОЖНОГО ДВИЖЕНИЯ И СТАТИСТИКА ДОРОЖНО-ТРАНСПОРТНЫХ ПРОИСШЕСТВИЙ Опасные и вредные прозводственные факторы
Опасные и вредные прозводственные факторы Организация рабочего места для электромонтажных работ
Организация рабочего места для электромонтажных работ Красный, жёлтый, зелёный, мы должны о них всё знать!
Красный, жёлтый, зелёный, мы должны о них всё знать! Правовое регулирование безопасности туризма от чрезвычайных ситуаций в Российской Федерации
Правовое регулирование безопасности туризма от чрезвычайных ситуаций в Российской Федерации Безопасные действия в условиях ЧС военного характера
Безопасные действия в условиях ЧС военного характера Организационно-штатная структура
Организационно-штатная структура Опасные ситуации на улице
Опасные ситуации на улице Автономное существование человека в условиях природной среды
Автономное существование человека в условиях природной среды Сабақтың тақырыбы: Еңбекті қорғаудың теориялық негіздері
Сабақтың тақырыбы: Еңбекті қорғаудың теориялық негіздері Безопасность на водных объектах
Безопасность на водных объектах Международный день борьбы с наркоманией
Международный день борьбы с наркоманией Антитеррор. Безопасность для детей. Действия персонала и учащихся школы при угрозе террористического акта
Антитеррор. Безопасность для детей. Действия персонала и учащихся школы при угрозе террористического акта Чрезвычайные ситуации техногенного характера и защита населения от их последствий
Чрезвычайные ситуации техногенного характера и защита населения от их последствий Средства индивидуальной защиты
Средства индивидуальной защиты Промышленная безопасность
Промышленная безопасность Медицинское снабжение формирований и учреждений, предназначенных для медико-санитарного обеспечения населения в ЧС
Медицинское снабжение формирований и учреждений, предназначенных для медико-санитарного обеспечения населения в ЧС Защита человека и производственных объектов от опасных факторов комплексного характера – от пожара
Защита человека и производственных объектов от опасных факторов комплексного характера – от пожара Ручные и звуковые сигналы
Ручные и звуковые сигналы Защита населения и хозяйственных объектов в чрезвычайных ситуациях. Радиационная безопасность
Защита населения и хозяйственных объектов в чрезвычайных ситуациях. Радиационная безопасность Статистика курения в мире
Статистика курения в мире Интеллектуальная игра по правилам пожарной безопасности
Интеллектуальная игра по правилам пожарной безопасности Организация санитарно-гигиенических и противоэпидемических мероприятий среди населения в военное время
Организация санитарно-гигиенических и противоэпидемических мероприятий среди населения в военное время Политика по охране труда и безопасности
Политика по охране труда и безопасности Откажись от спайсов - выбери жизнь
Откажись от спайсов - выбери жизнь