Содержание
- 2. Huge thanks Curtis Mechling http://twitter.com/#!/curtismechling
- 3. Outline This talk is for all audiences, no experience and seasoned .Net developers I’ll be covering
- 4. Steps to reverse .Net app Run the application to understand functionality Decompile the application Review source
- 5. Topic not new Many others before me have discussed the insecurities of .Net applications Mark Pearl
- 6. Reversing and obfuscation What exactly is reversing and obfuscation? Reversing example You’re given an EXE and
- 7. .Net basics .Net, it’s a framework, nuff said Blanket term for microsoft family of technologies Most
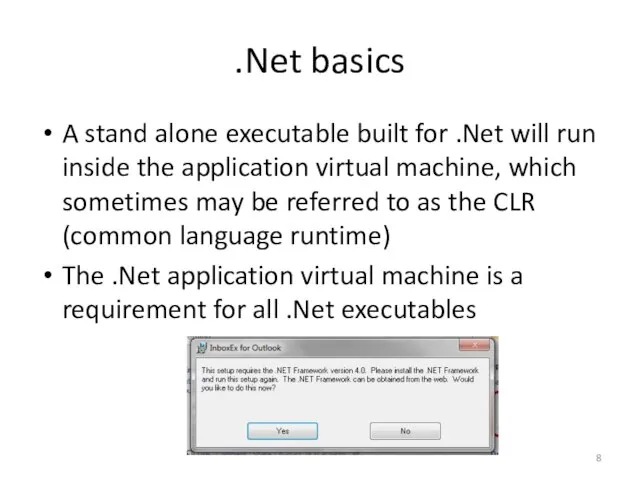
- 8. .Net basics A stand alone executable built for .Net will run inside the application virtual machine,
- 9. Executables There are two main kinds of EXE’s Compiled and interpreted Compiled applications usually require an
- 10. Executables Compiled executables are often built with a higher programming language, such as C++, which then
- 11. Executables Interpreted executables, such as java and .Net, are much easier to reverse The interpreted compilation
- 12. Obfuscation Because it’s trivial to get source code from a .Net application developers will use obfuscation
- 13. Determine type executable There are a number of ways to determine the type of executable you’re
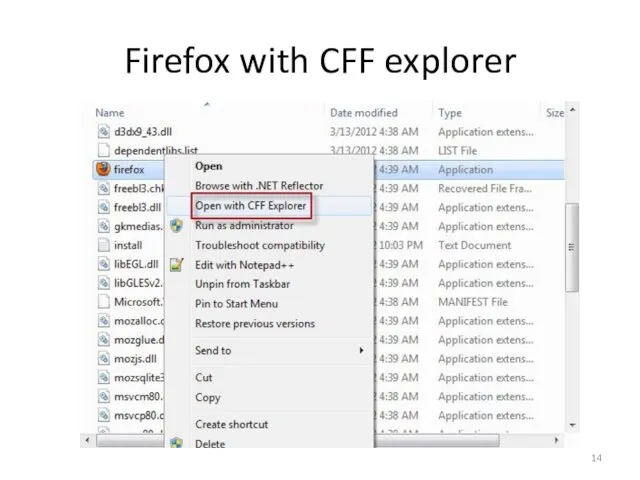
- 14. Firefox with CFF explorer
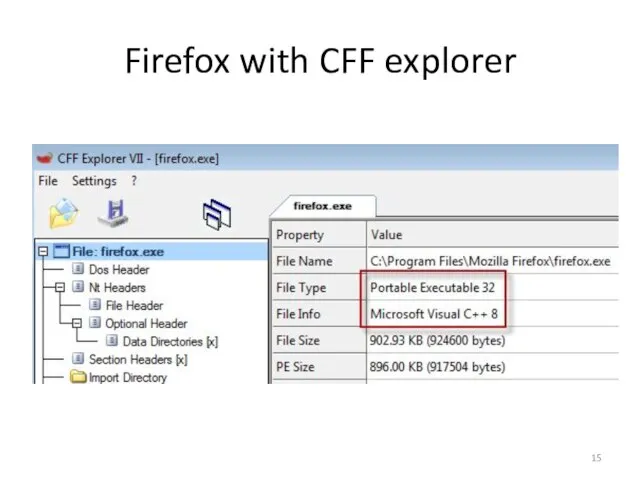
- 15. Firefox with CFF explorer
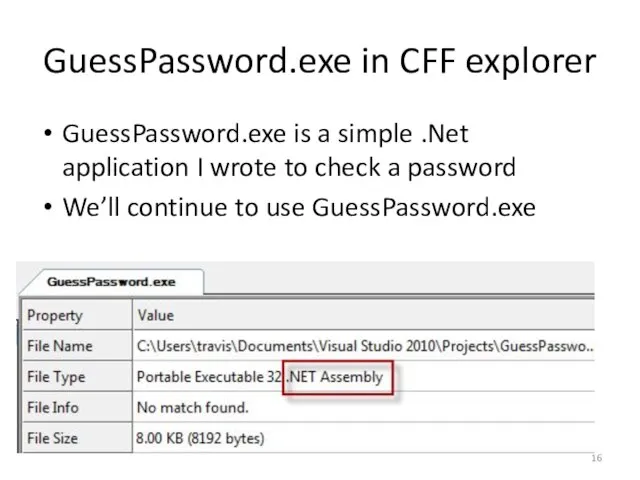
- 16. GuessPassword.exe in CFF explorer GuessPassword.exe is a simple .Net application I wrote to check a password
- 17. Next step > decompile Now you’ve identified the executable was built using .Net Next step is
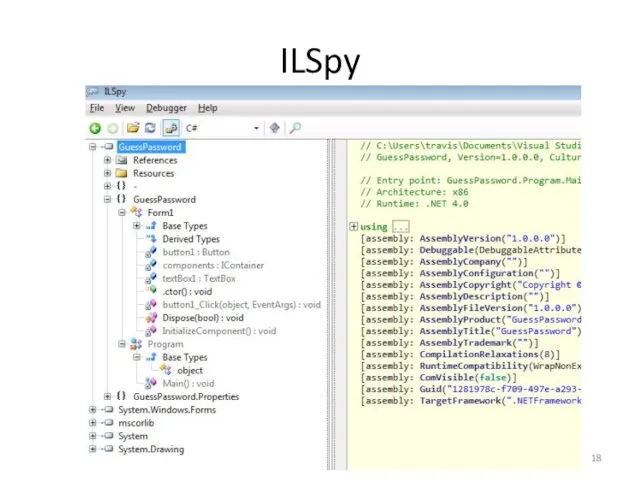
- 18. ILSpy
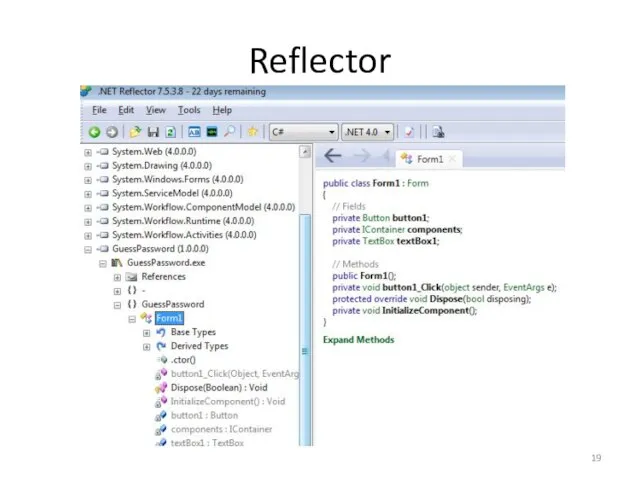
- 19. Reflector
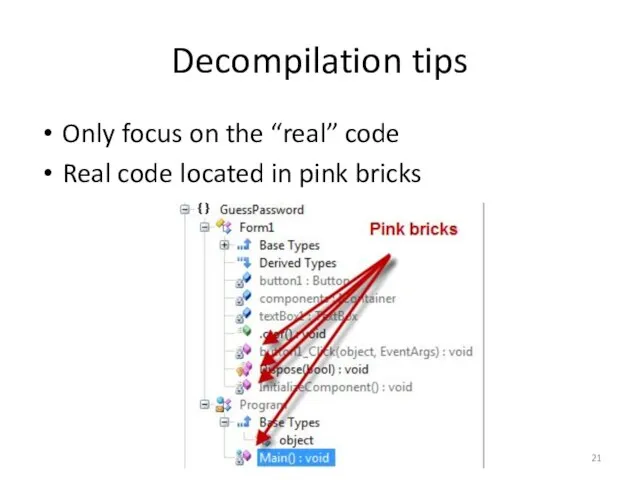
- 20. Decompilation tips Only analyze your exe tree and ignore dependencies that get pulled in
- 21. Decompilation tips Only focus on the “real” code Real code located in pink bricks
- 22. SafeAsHouses.exe Let’s take a look at a real life example SafeAsHouses.exe can be downloaded from from
- 23. SafeAsHouses in ILSpy
- 24. SafeAsHouses in ILSpy So soon as we open SafeAsHouses.exe in ILSpy we see signs of obfuscation
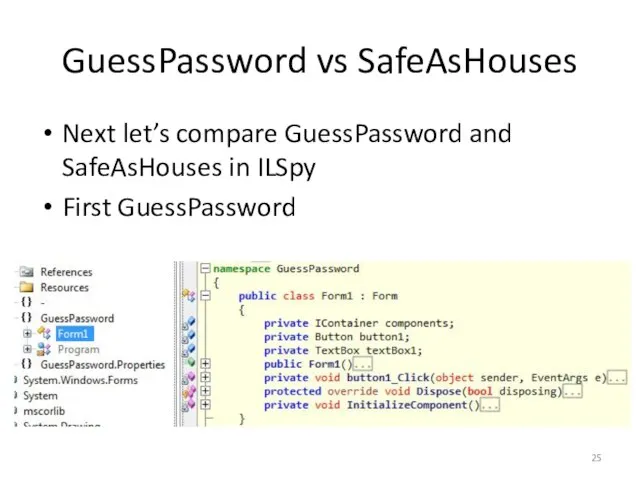
- 25. GuessPassword vs SafeAsHouses Next let’s compare GuessPassword and SafeAsHouses in ILSpy First GuessPassword
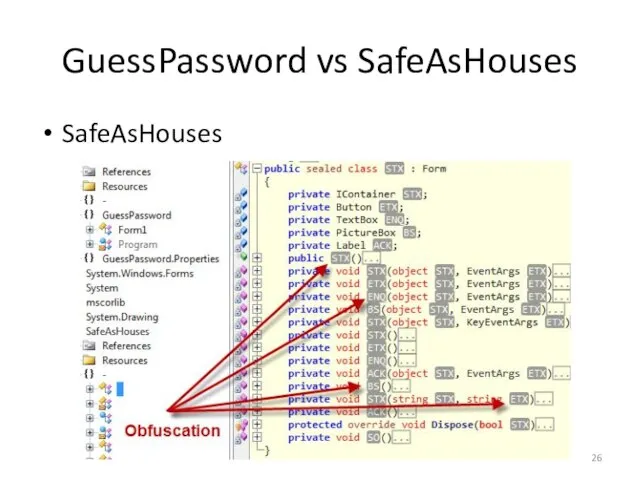
- 26. GuessPassword vs SafeAsHouses SafeAsHouses
- 27. More obfuscation Here we see more signs of obfuscation In GuessPassword we see how things should
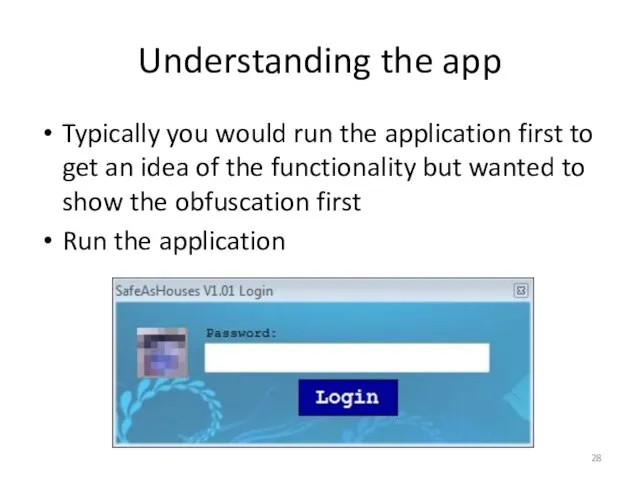
- 28. Understanding the app Typically you would run the application first to get an idea of the
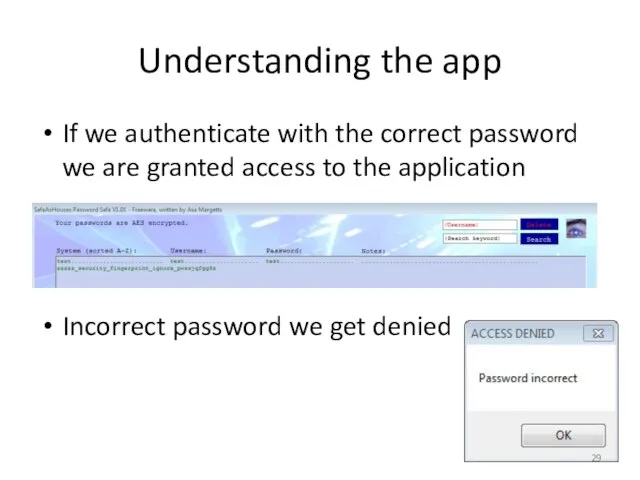
- 29. Understanding the app If we authenticate with the correct password we are granted access to the
- 30. Items of interest The application asks for input Incorrect password presents a pop up stating “Password
- 31. Items of interest The main idea is to take certain areas of interest inside the application
- 32. Searching for items of interest Now that we’ve done some recon and understand the type of
- 33. Decompile code into text file
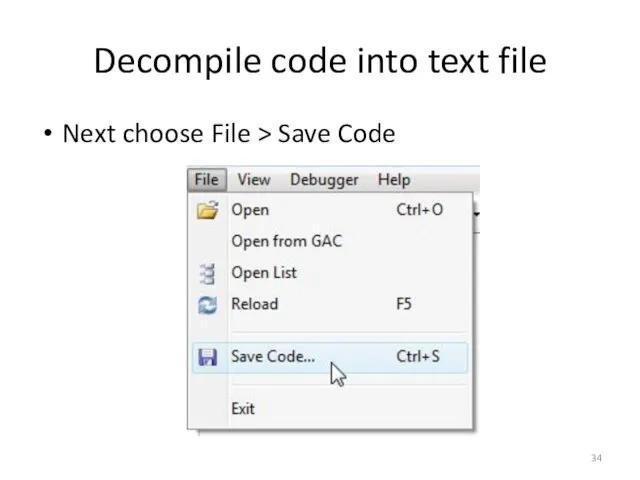
- 34. Decompile code into text file Next choose File > Save Code
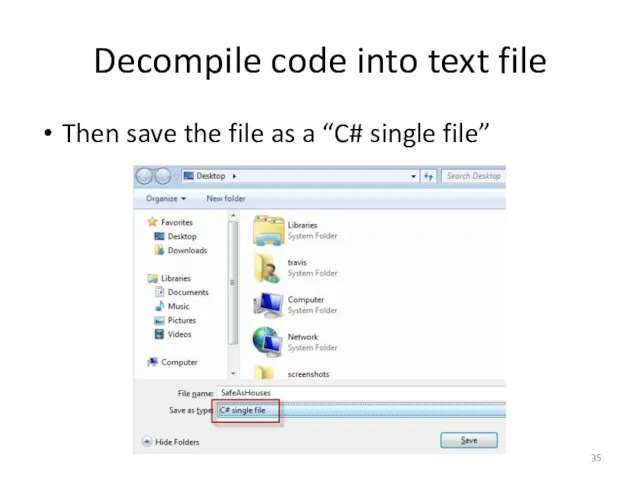
- 35. Decompile code into text file Then save the file as a “C# single file”
- 36. Decompile code into text file At this point you can use your favorite text editor to
- 37. Reflector code search plugin Reflector’s code search plugin is very convenient in that you don’t have
- 38. Items of interest The application asks for input Incorrect password presents a pop up stating “Password
- 39. Application asks for input A popular way of taking form input in a .Net application is
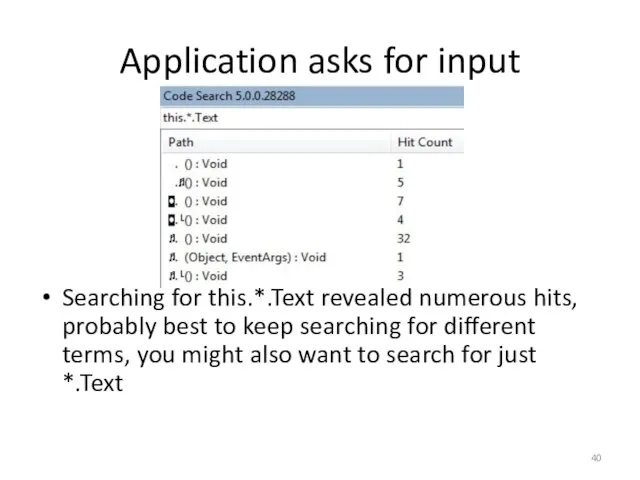
- 40. Application asks for input Searching for this.*.Text revealed numerous hits, probably best to keep searching for
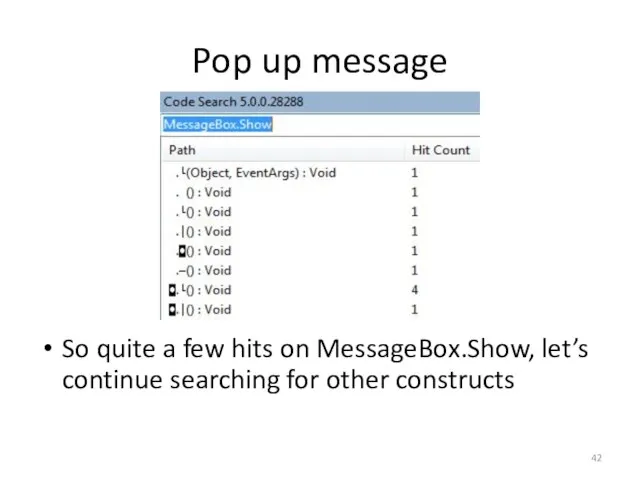
- 41. Pop up message A pop up box is typically done with the “MessageBox.Show” method Two arguments
- 42. Pop up message So quite a few hits on MessageBox.Show, let’s continue searching for other constructs
- 43. Pop up message The pop up message states “Password incorrect” We should search the code for
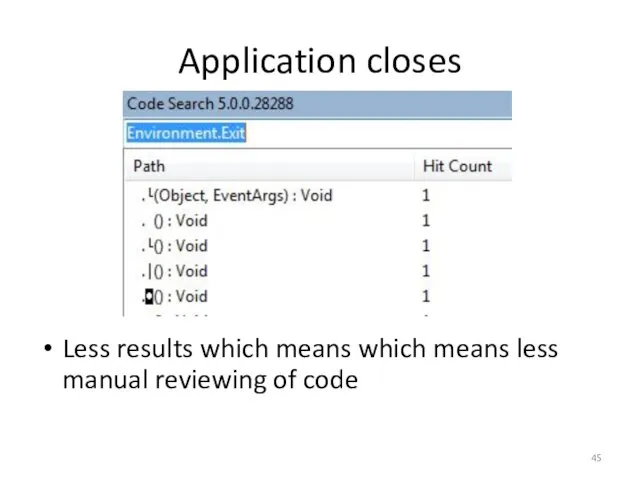
- 44. Application closes If you enter an incorrect password you’ll get a pop up, after clicking OK
- 45. Application closes Less results which means which means less manual reviewing of code
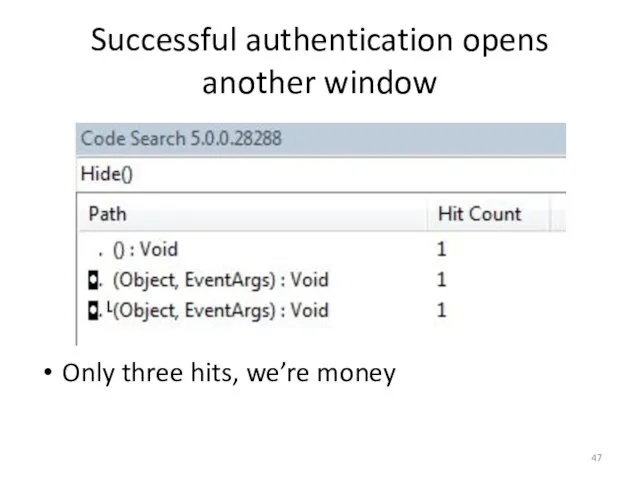
- 46. Successful authentication opens another window Probably the most popular way to show one window then hide
- 47. Successful authentication opens another window Only three hits, we’re money
- 48. Code search plugin Using this plugin we were able to narrow down to only three locations
- 49. First hit, found the functionality
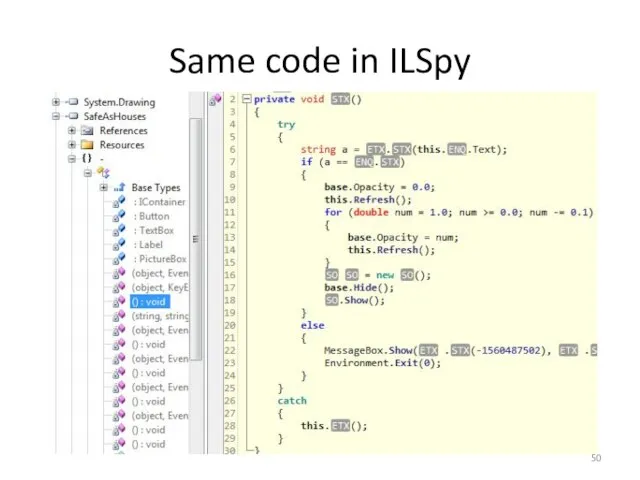
- 50. Same code in ILSpy
- 51. Explanation of code Line 6: developer is assigning variable “a” to whatever you type into the
- 52. Subverting authentication Now that we’ve found the code that performs the authentication we want to subvert
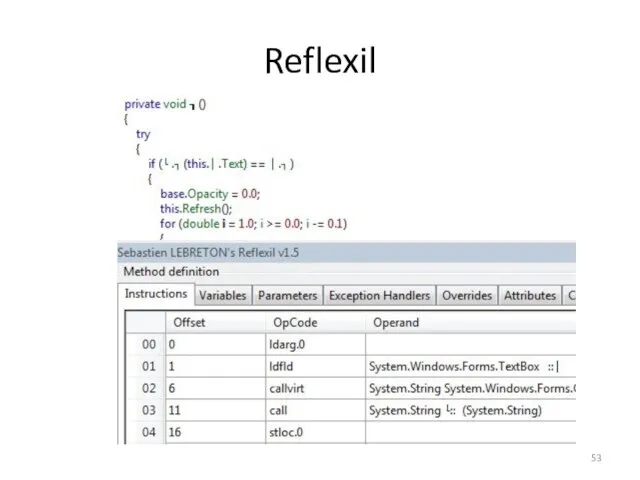
- 53. Reflexil
- 54. Reflexil The bottom half of the previous screen shot shows the reflexil plugin to reflector With
- 55. CIL Lower level language used by the .Net application virtual machine So your higher level programming,
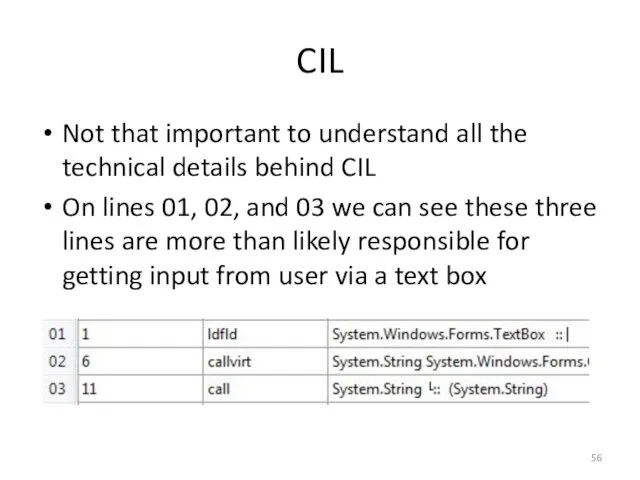
- 56. CIL Not that important to understand all the technical details behind CIL On lines 01, 02,
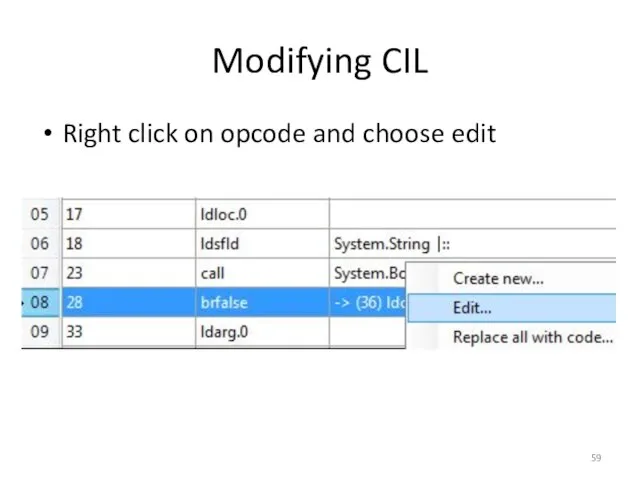
- 57. Modifying CIL Looking through the code and CIL we see an interesting instruction on line 07
- 58. Modifying CIL You’ll also notice the operand for the opcode on line 08 is “->(36)” This
- 59. Modifying CIL Right click on opcode and choose edit
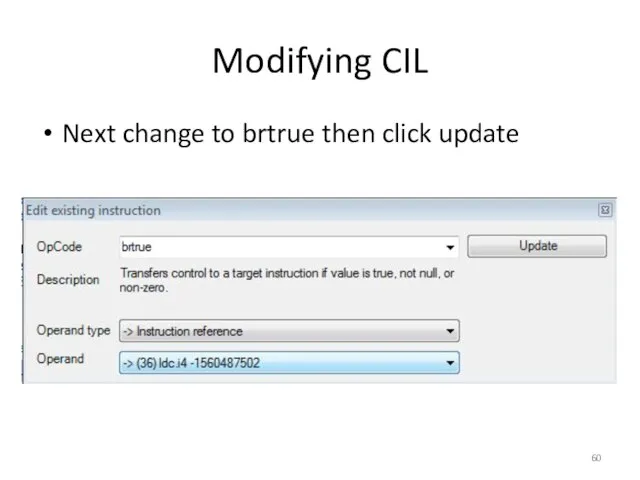
- 60. Modifying CIL Next change to brtrue then click update
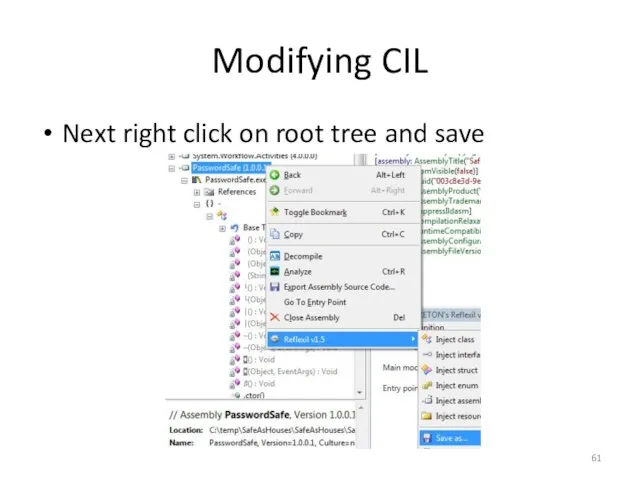
- 61. Modifying CIL Next right click on root tree and save
- 62. Patched executable Now you’ve successfully patched a .Net executable If we run this we can provide
- 63. Deleting code blocks
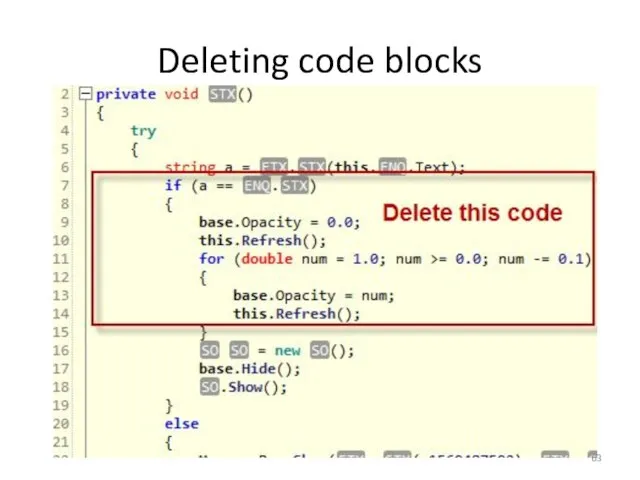
- 64. Delete code blocks Delete lines 1-28 Save the patched application Run it again and now it
- 65. Missing code block
- 66. Great success We’ve successfully modified the application to subvert authentication If we had obtained this executable
- 67. Easier reversing via deobfuscation There is a slightly easier way to go about reversing an obfuscated
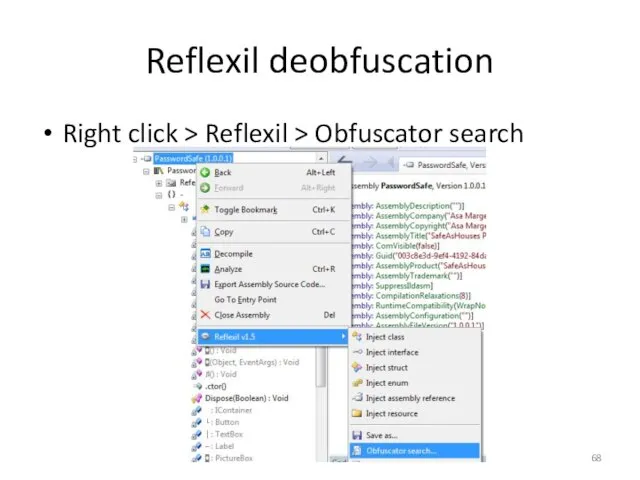
- 68. Reflexil deobfuscation Right click > Reflexil > Obfuscator search
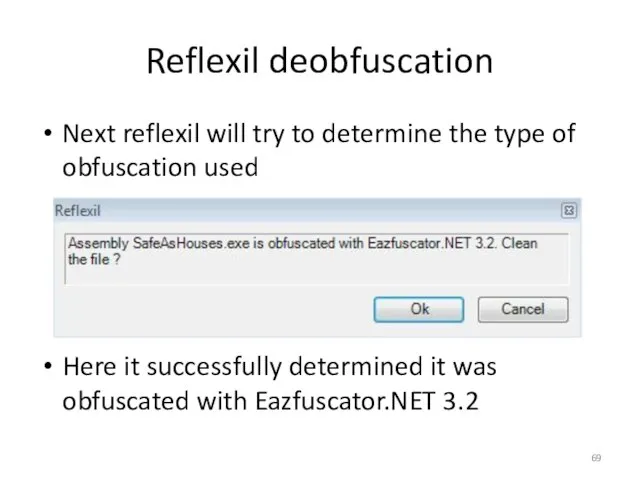
- 69. Reflexil deobfuscation Next reflexil will try to determine the type of obfuscation used Here it successfully
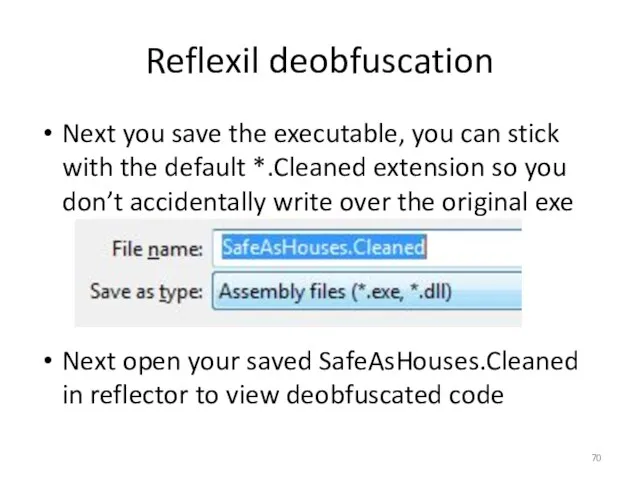
- 70. Reflexil deobfuscation Next you save the executable, you can stick with the default *.Cleaned extension so
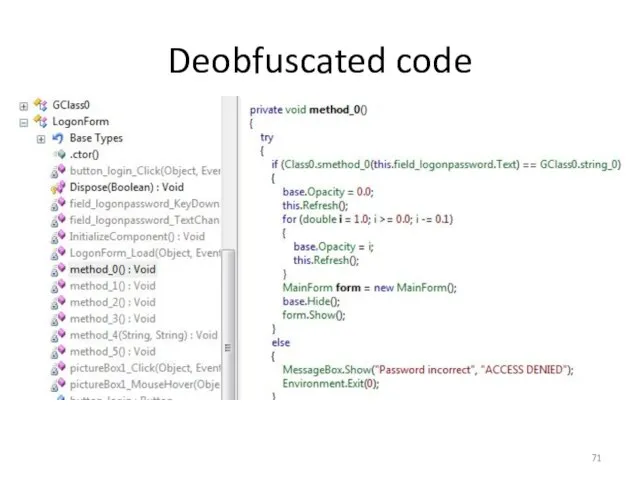
- 71. Deobfuscated code
- 72. Deobfuscated code So reflexil actually does a nice job on getting us better source code It
- 73. Steps to reverse .Net app Run the application to understand functionality Decompile the application Review source
- 74. Wrapping up A standalone .Net executable will more than likely be very easy to decompile to
- 76. Скачать презентацию








































 Структура книги
Структура книги Устройства хранения информации
Устройства хранения информации Файловая система
Файловая система Презентация "Правила безопасной работы в сети Интернет" - скачать презентации по Информатике
Презентация "Правила безопасной работы в сети Интернет" - скачать презентации по Информатике Средства массовой информации
Средства массовой информации Метод координат. Способы кодирования информации
Метод координат. Способы кодирования информации Новостной сайт
Новостной сайт Структуированные переменные данные
Структуированные переменные данные Электронные таблицы. Формулы
Электронные таблицы. Формулы Базы данных. Основные понятия и общие представления
Базы данных. Основные понятия и общие представления Базовая настройка коммутаторов 3028, 3526, 1210-28P
Базовая настройка коммутаторов 3028, 3526, 1210-28P Представление информации. Информация и информационные процессы
Представление информации. Информация и информационные процессы Защита информационных процессов в компьютерных системах. Тема 4
Защита информационных процессов в компьютерных системах. Тема 4 Теоретические методы исследования в технологическом образовании. Абстракция. Структурно-функциональные модели
Теоретические методы исследования в технологическом образовании. Абстракция. Структурно-функциональные модели Учебный курс Язык UML в анализе и проектировании программных систем и бизнес-процессов Лекция 1 Базовые принципы и понятия техн
Учебный курс Язык UML в анализе и проектировании программных систем и бизнес-процессов Лекция 1 Базовые принципы и понятия техн Паттерн Singleton
Паттерн Singleton Графики и диаграммы. Наглядное представление о соотношении величин
Графики и диаграммы. Наглядное представление о соотношении величин Базы данных
Базы данных Графы. Состав графа
Графы. Состав графа Обработка информации
Обработка информации ЭБС Лань
ЭБС Лань Простейшие конструкции языка Pascal
Простейшие конструкции языка Pascal Особенности средств разработки информационной системы
Особенности средств разработки информационной системы Презентация Основы логики
Презентация Основы логики Виды компьютерной графики. 8 класс
Виды компьютерной графики. 8 класс GIT : getting decentralized
GIT : getting decentralized Текст как форма представления информации
Текст как форма представления информации Разработка автоматизированной системы управления технологическими процессами ООО «Связьторг»
Разработка автоматизированной системы управления технологическими процессами ООО «Связьторг»