Содержание
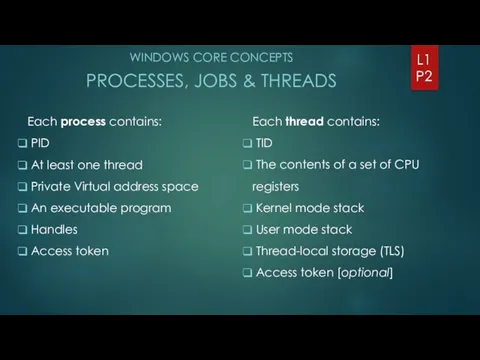
- 2. WINDOWS CORE CONCEPTS PROCESSES, JOBS & THREADS L1 P2 Each process contains: PID At least one
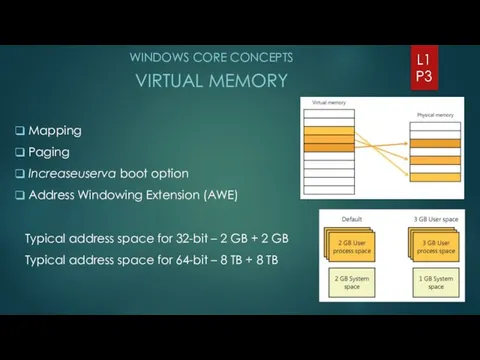
- 3. WINDOWS CORE CONCEPTS VIRTUAL MEMORY L1 P3 Mapping Paging Increaseuserva boot option Address Windowing Extension (AWE)
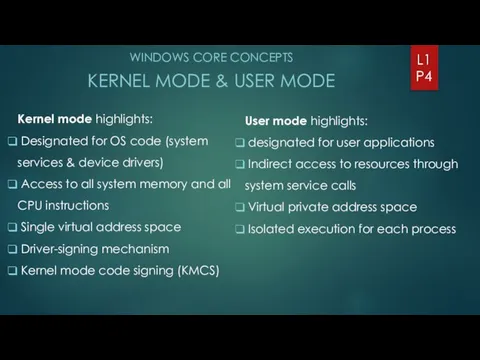
- 4. WINDOWS CORE CONCEPTS KERNEL MODE & USER MODE L1 P4 Kernel mode highlights: Designated for OS
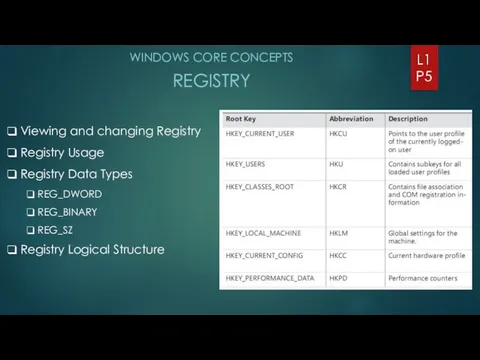
- 5. WINDOWS CORE CONCEPTS REGISTRY L1 P5 Viewing and changing Registry Registry Usage Registry Data Types REG_DWORD
- 6. WINDOWS CORE CONCEPTS OBJECTS & HANDLES L1 P6 Objects Providing human-readable names for system resources Sharing
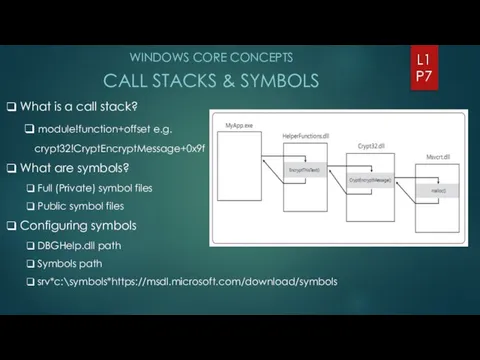
- 7. WINDOWS CORE CONCEPTS CALL STACKS & SYMBOLS L1 P7 What is a call stack? module!function+offset e.g.
- 9. Скачать презентацию

 Информатика вокруг нас
Информатика вокруг нас Электронные таблицы
Электронные таблицы Определение и объявление функций пользователя. Лекция 10 по алгоритмизации и программированию
Определение и объявление функций пользователя. Лекция 10 по алгоритмизации и программированию Data Modeling and Databases
Data Modeling and Databases Операционные системы WINDOWS
Операционные системы WINDOWS Функциональная схема компьютера
Функциональная схема компьютера Локальные и глобальные компьютерные сети
Локальные и глобальные компьютерные сети Передача данных. Протоколы передачи данных UDP, TCP/IP. Серверы виртуальных приборов. (Лекция 5)
Передача данных. Протоколы передачи данных UDP, TCP/IP. Серверы виртуальных приборов. (Лекция 5) Создание трехмерного мира в SketchU. Введение в трехмерную графику. (Урок 1)
Создание трехмерного мира в SketchU. Введение в трехмерную графику. (Урок 1) Примеры символьной обработки (язык C, лекция 9)
Примеры символьной обработки (язык C, лекция 9) Spyware - one of the most dangerous forms of malware
Spyware - one of the most dangerous forms of malware Теория журналистики. Анализ текстов политического обозревателя современной системы СМИ России. Александр Векслер
Теория журналистики. Анализ текстов политического обозревателя современной системы СМИ России. Александр Векслер Вебинар MLMPRAVDA.RU
Вебинар MLMPRAVDA.RU Язык программирования PYTHON
Язык программирования PYTHON Двоичное кодирование графической информации
Двоичное кодирование графической информации Методики повышения защищенности программ от сбоев, за счет адаптивных коррекций стандарта кодирования
Методики повышения защищенности программ от сбоев, за счет адаптивных коррекций стандарта кодирования Компьютерная графика (Autodesk 3ds max). Полигональное моделирование. (Лекция 4.1)
Компьютерная графика (Autodesk 3ds max). Полигональное моделирование. (Лекция 4.1) Интерактивные операционные системы. Системы реального времени
Интерактивные операционные системы. Системы реального времени Графический интерфейс Windows
Графический интерфейс Windows Язык запросов к реляционным базам данных. Операторы манипулирования и изменения данных
Язык запросов к реляционным базам данных. Операторы манипулирования и изменения данных Программирование (Python). Введение
Программирование (Python). Введение Технологии проектирования информационных систем. Применение сетей Петри для моделирования бизнес-процессов
Технологии проектирования информационных систем. Применение сетей Петри для моделирования бизнес-процессов Improvement methods and algorithms of displaying operational information
Improvement methods and algorithms of displaying operational information История вычислительной техники
История вычислительной техники Sissejuhatus informaatikasse. 11. Loeng
Sissejuhatus informaatikasse. 11. Loeng Программирование в компьютерных сетях
Программирование в компьютерных сетях Классификация онтологий по степени формальности представления
Классификация онтологий по степени формальности представления Как получить услугу на портале gosuslugi.ru
Как получить услугу на портале gosuslugi.ru