Содержание
- 2. Thanks for coming!
- 3. WINDOWS POST EXPLOITATION
- 4. About Me / Housekeeping Samuel Gibson Penetration tester Former security administrator Masters in Information Assurance and
- 5. What to Expect What this presentation is not about Exploits “L337 haxoring” Finding sensitive data What
- 6. Exploits are Cool, but Risky Last option Might get flagged by anti-virus Alert target organization Impact
- 7. FLOW OF TALK
- 8. Flow of Talk Attackers have goals (i.e. data theft) Attackers usually need to escalate and pivot
- 9. Details About the REDLAB Network
- 10. Important REDLAB User Accounts REDLAB\Administrator – Built-in Domain Admin Can access anything REDLAB\Aadmin – Alice Admin
- 11. Note on Privilege Escalation Privilege escalation involves gaining additional privileges to gain access to additional resources
- 12. INITIAL ACCESS WIN7USER: Non-admin
- 13. Initial Recon Situational awareness Examine local system Sensitive information (goal) Privileges (current access) Credentials (potential rights
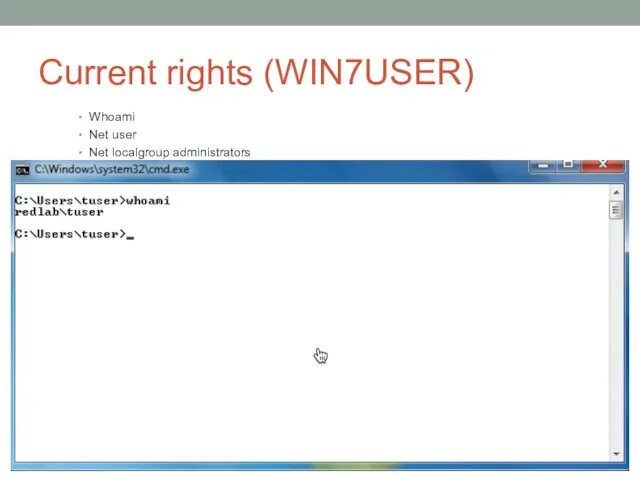
- 14. Current rights (WIN7USER) Whoami Net user Net localgroup administrators
- 15. Local Escalation Lots of options Unattended install file C:\Windows\Panther\Unattend.xml Automatic logon HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon Always install elevated
- 16. UNQUOTED SERVICE PATHS File Permission-based Privilege Escalation
- 17. Unquoted Service Paths Issue when there is a space in a file path and the attacker
- 18. Potential Paths to Write EXE C:\Program.exe C:\Program Files (x86)\REALTEK\USB.exe This will throw an error on reboot
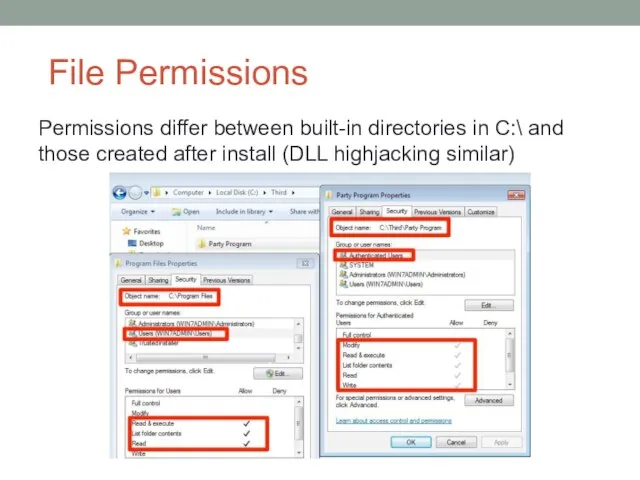
- 19. File Permissions Permissions differ between built-in directories in C:\ and those created after install (DLL highjacking
- 20. GROUP POLICY PREFERENCES Examining Network Resources
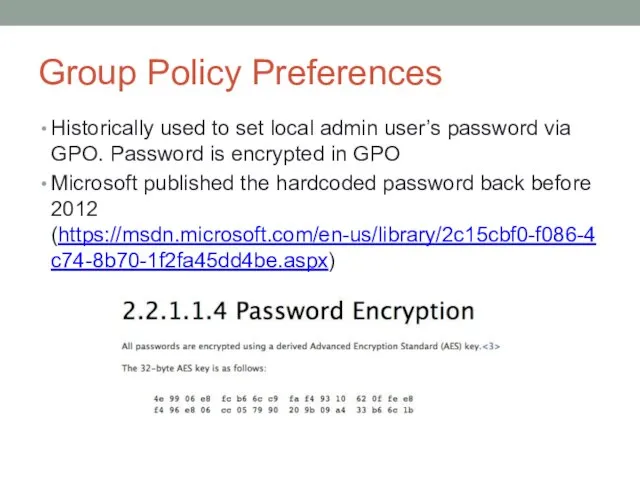
- 21. Group Policy Preferences Historically used to set local admin user’s password via GPO. Password is encrypted
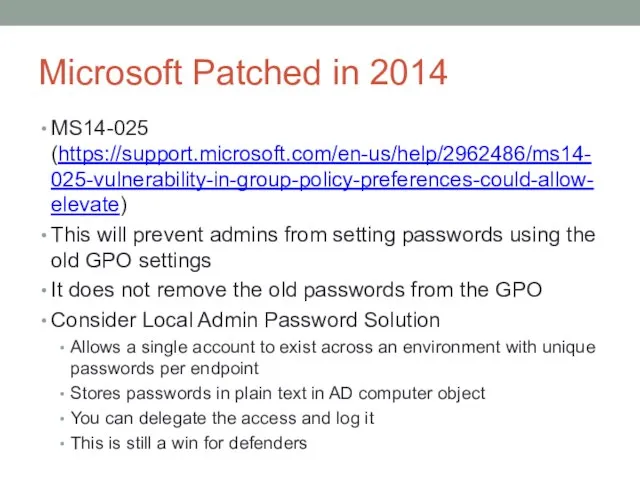
- 22. Microsoft Patched in 2014 MS14-025 (https://support.microsoft.com/en-us/help/2962486/ms14-025-vulnerability-in-group-policy-preferences-could-allow-elevate) This will prevent admins from setting passwords using the old
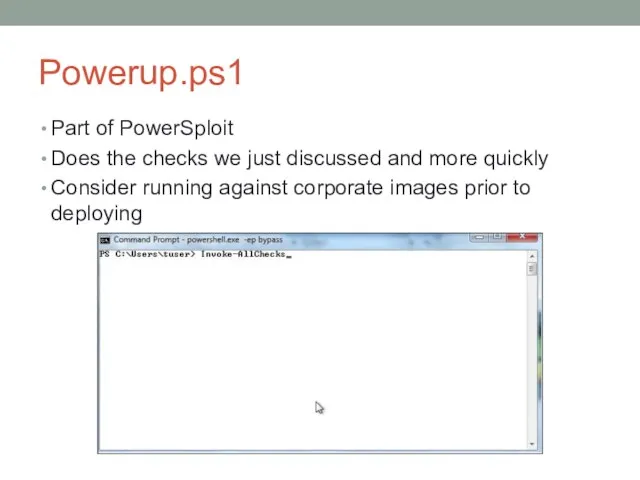
- 23. Powerup.ps1 Part of PowerSploit Does the checks we just discussed and more quickly Consider running against
- 24. FINDING ADMIN ON OTHER SYSTEMS Finding Shares Using Current Credentials
- 25. Eventually Look to Other Hosts Can’t escalate locally or need to find target data Search for
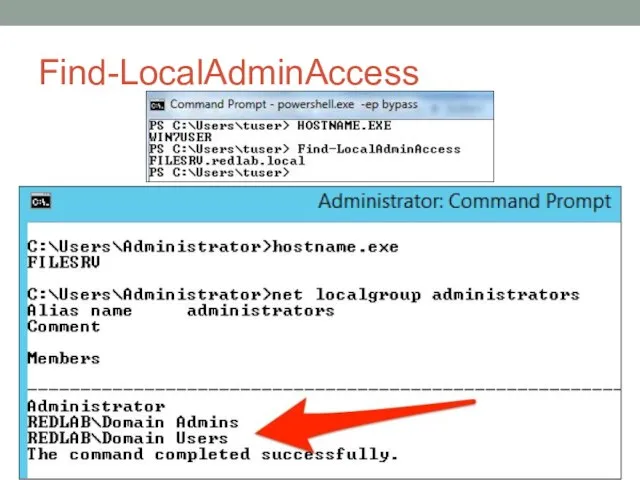
- 26. Find-LocalAdminAccess
- 27. WRITE PERMISSIONS ON SHARES
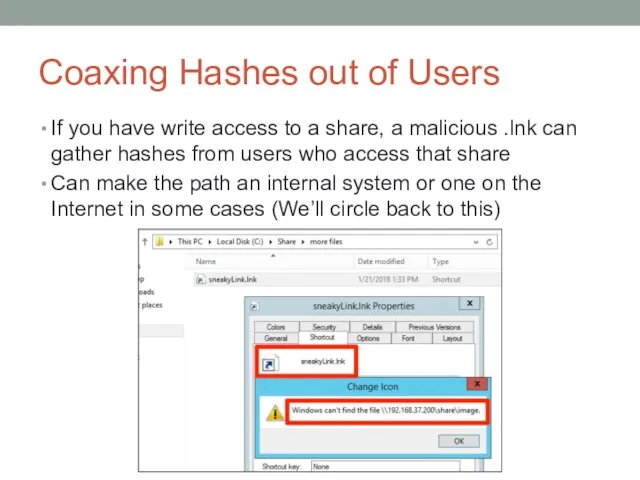
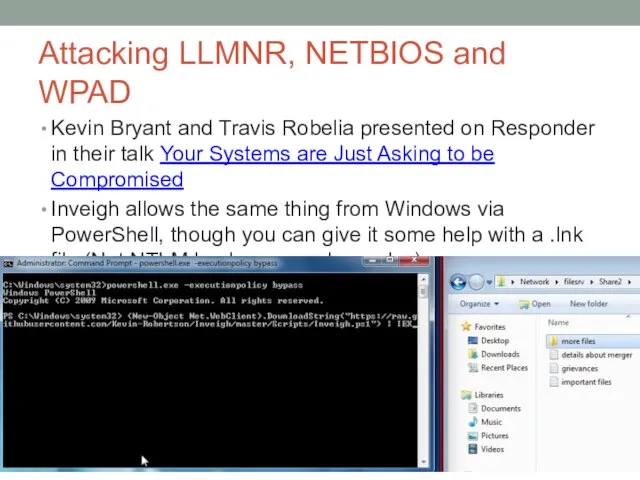
- 28. Coaxing Hashes out of Users If you have write access to a share, a malicious .lnk
- 29. CHECK NETWORK DEVICES Printers or Other Systems with Default Credentials
- 30. Check Printers for Default Passwords Printers often have default admin credentials MFPs have ability to scan
- 31. KERBEROASTING Still as a Regular User
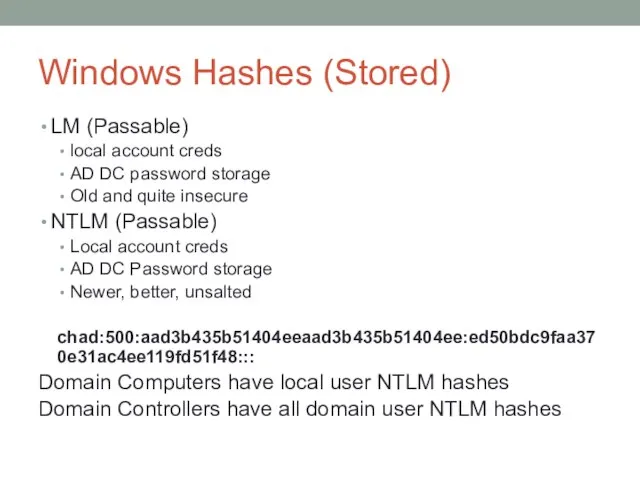
- 32. Windows Hashes (Stored) LM (Passable) local account creds AD DC password storage Old and quite insecure
- 33. Kerberos (Oversimplified) Centralized user authentication that relies on a centralized infrastructure for authentication Does not send
- 34. SQL Server Express on FILESRV Service Principal Name (SPN) in Active Directory
- 35. Important SQLService Account Details SamAccountName : sqlservice DistinguishedName : CN=Important SQLService,CN=Users,DC=redlab,DC=local ServicePrincipalName : MSSQLSvc/FILESRV.redlab.local:SQLEXPRESS SPNs uniquely
- 36. Attacking Kerberos Attacking Kerberos: Kicking the Guard Dog of Hades It’s possible to request a Ticket
- 37. Kerberoasting Attack
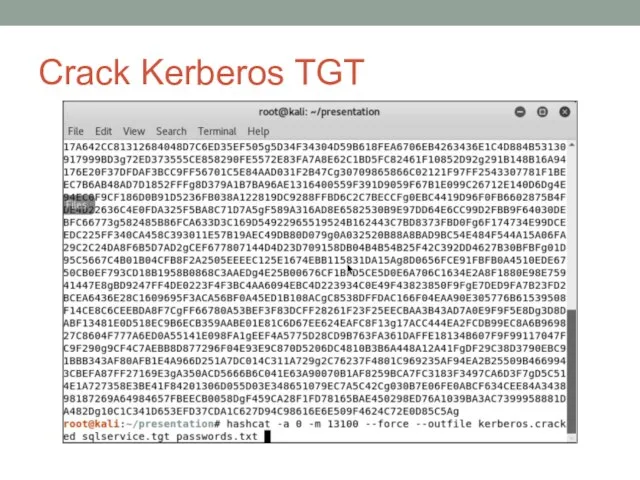
- 38. Crack Kerberos TGT
- 39. PASSWORD SPRAYING
- 40. Get a List of Domain Users Any authenticated user can pull a list of all domain
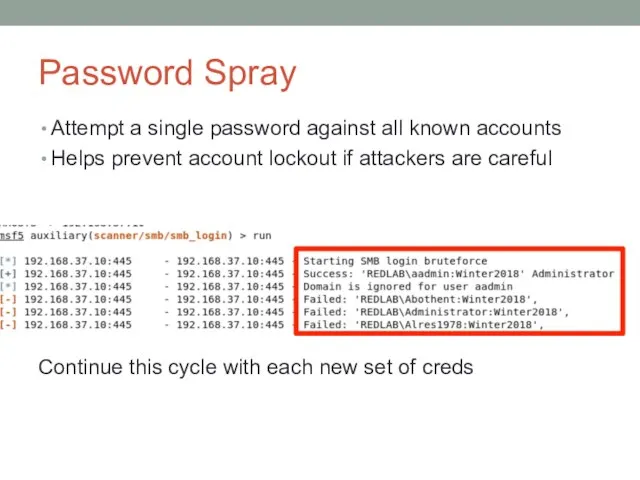
- 41. Password Spray Attempt a single password against all known accounts Helps prevent account lockout if attackers
- 42. ADMIN ACCESS Further Local Attack Opportunities
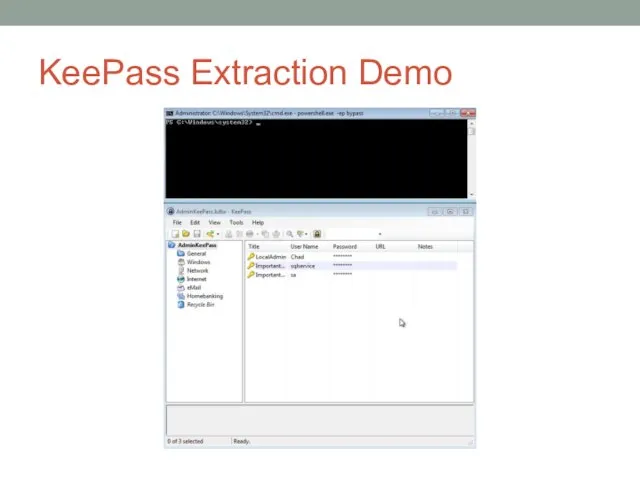
- 43. Extract KeePass Keys KeePass is a popular password database Shared between users With admin rights, it’s
- 44. KeePass Extraction Demo
- 45. NETWORK-BASED ATTACKS LLMNR, NETBIOS, and WPAD
- 46. Attacking LLMNR, NETBIOS and WPAD Kevin Bryant and Travis Robelia presented on Responder in their talk
- 47. LOCAL ADMIN CAN DUMP LOCAL CREDENTIALS
- 48. Metasploit Simplifies This I personally use Metasploit with credentials more than I use it to exploit
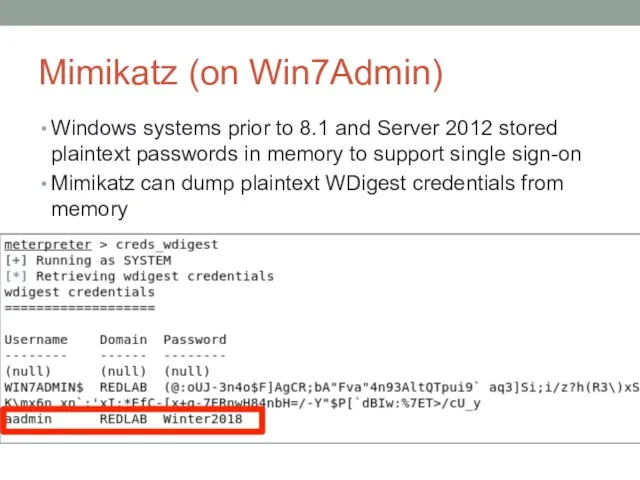
- 49. Mimikatz (on Win7Admin) Windows systems prior to 8.1 and Server 2012 stored plaintext passwords in memory
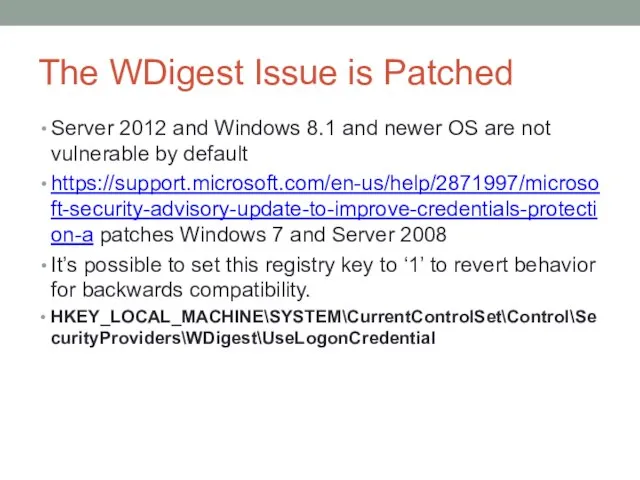
- 50. The WDigest Issue is Patched Server 2012 and Windows 8.1 and newer OS are not vulnerable
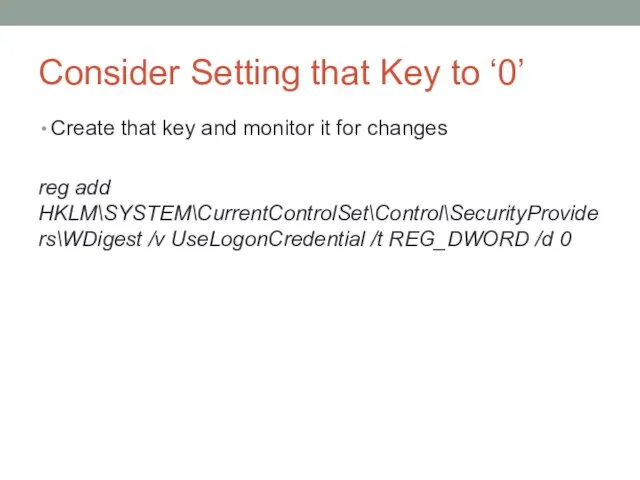
- 51. Consider Setting that Key to ‘0’ Create that key and monitor it for changes reg add
- 52. DOMAIN ADMIN Hashes and Pivots
- 53. Can use AD Admin Account to Dump Domain Hashes
- 54. Hashes Can Be Cracked or Passed Attackers can pass those hashes to the SMB service to
- 55. Pass the Hash
- 56. Pass the Hash Only works for members of the local Administrators group Can be mitigated to
- 57. WRAP UP
- 58. Lots of Content Survey of methods of escalating privileges and gathering credentials available to all levels
- 59. Questions? I work for a company called Sikich LLP Pentesting / QSA / Forensics samuel[dot]gibson[at]sikich[dot]com Feel
- 60. Next Months MeetUp: Monday March 5th! (Speaker Matt Miller)
- 61. Recordings on website: ECInfoSec.com
- 62. Donations and company sponsorships are welcome to help grow EC InfoSec!
- 63. Contact us! On MeetUp.com admin@ECInfoSec.com
- 64. Chat with each other on Slack! Join Link On Website: ECInfoSec.com
- 65. Raise your hand if you would be willing to present a topic in April or May!
- 66. Please fill out and hand in the survey!
- 68. Скачать презентацию

































 Киберпреступность: исследование истории вопроса
Киберпреступность: исследование истории вопроса Медиа-карта региона: Реклама в СМИ
Медиа-карта региона: Реклама в СМИ Анализ цифровых изображений. Oz PhotoExpert Server Edition
Анализ цифровых изображений. Oz PhotoExpert Server Edition Основные функции СМИ
Основные функции СМИ Виды баз данных БД
Виды баз данных БД Мобильные 4G сети
Мобильные 4G сети ArchiCAD. Инстумент перекрытия
ArchiCAD. Инстумент перекрытия Презентация "Методические рекомендации по Созданию сайта" - скачать презентации по Информатике
Презентация "Методические рекомендации по Созданию сайта" - скачать презентации по Информатике Проектирование высокоскоростной КС для реализации автоматизированной системы обработки информации и управления предприятием
Проектирование высокоскоростной КС для реализации автоматизированной системы обработки информации и управления предприятием Новые системы онлайн
Новые системы онлайн Всемирная паутина. Информация и информационные процессы
Всемирная паутина. Информация и информационные процессы Операторы и функции
Операторы и функции Модель и цели моделирования
Модель и цели моделирования Условный и сложный операторы . Операторы цикла. Массивы.
Условный и сложный операторы . Операторы цикла. Массивы.  Измерение информации. Алфавитный и содержательный подходы
Измерение информации. Алфавитный и содержательный подходы Презентация к ЛР1
Презентация к ЛР1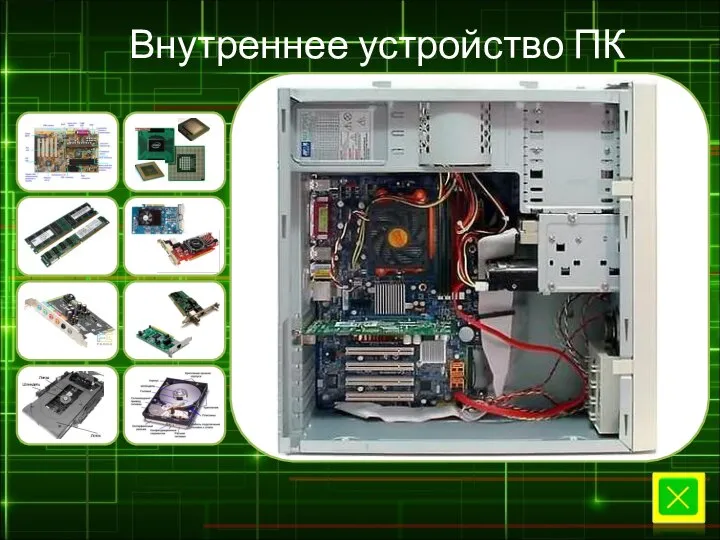 Презентация "ВНУТРЕННЕЕ УСТРОЙСТВО ПК" - скачать презентации по Информатике
Презентация "ВНУТРЕННЕЕ УСТРОЙСТВО ПК" - скачать презентации по Информатике Правила для администраторов
Правила для администраторов Поиск недостающей информации, сбор, анализ
Поиск недостающей информации, сбор, анализ Современные медиа и новые форматы
Современные медиа и новые форматы Управление памятью
Управление памятью Управление доступностью информационных ресурсов с помощью программы ИКС
Управление доступностью информационных ресурсов с помощью программы ИКС Численное решение одномерных задач динамики сплошных сред с учетом симметрии
Численное решение одномерных задач динамики сплошных сред с учетом симметрии Урок 1 Основные этапы становления информационного общества
Урок 1 Основные этапы становления информационного общества Электронные ресурсы сети Интернет для успешного обучения и самообразования
Электронные ресурсы сети Интернет для успешного обучения и самообразования Основы логики
Основы логики 3D чашка
3D чашка Учётные записи пользователя в Windows 11
Учётные записи пользователя в Windows 11