LEGITIMATE APPLICATIONS
Tracking Software (tracking software) is widely used and legal for
monitoring PCs.
Adware can openly be included in composition of free and shareware software. The user agrees to view advertising to have any further opportunity (for example - to use this program free of charge). In this case, the presence of adware should clearly prescribed in the end-user agreement (EULA).
Software modifications to the system can used for personalization of the desired user.
Program the remote control and monitoring can used for remote technical support or access to their own resources, which are located on the remote computer.
Program for automatic download can used to automatically updates, applications and OS updates.
Program for the analysis of security systems used to study the vulnerability of computer systems and other perfectly legitimate purposes.
Passive tracking technologies may be useful to personalize web pages visited by user.












 Линейные цепи постоянного тока
Линейные цепи постоянного тока Понятие и общие правила производства следственных действий Работу выполнили Пустовая Анастасия, Мятлик Елена, Ю-103
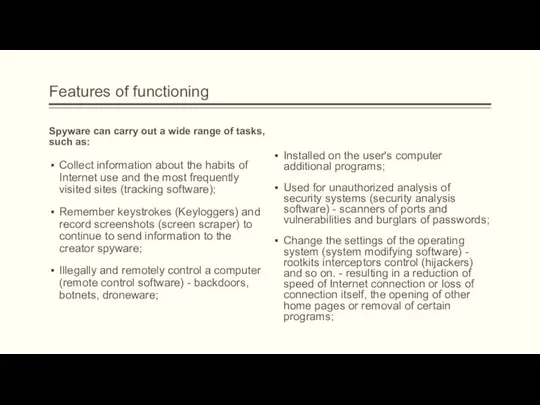
Понятие и общие правила производства следственных действий Работу выполнили Пустовая Анастасия, Мятлик Елена, Ю-103 Определение усилий в стержнях фермы
Определение усилий в стержнях фермы Лидер и мир. Что предполагает Евангелие
Лидер и мир. Что предполагает Евангелие Культурное наследие Латвии
Культурное наследие Латвии ФЕРМЕНТЫ
ФЕРМЕНТЫ Министерства США
Министерства США Прерывания в микропроцессорах
Прерывания в микропроцессорах Системы жизнеобеспечения населенных мест и зданий
Системы жизнеобеспечения населенных мест и зданий МЕТОДИКА РАСКРЫТИЯ ПОЛОСТЕЙ РАЗЛИЧНЫХ ГРУПП ЗУБОВ
МЕТОДИКА РАСКРЫТИЯ ПОЛОСТЕЙ РАЗЛИЧНЫХ ГРУПП ЗУБОВ Технология ТО и ремонта. Ходовая часть
Технология ТО и ремонта. Ходовая часть Архитектура и искусство Великобритании XVIІІ в
Архитектура и искусство Великобритании XVIІІ в Цели и инструменты денежно-кредитной политики. Горовых.А.Е
Цели и инструменты денежно-кредитной политики. Горовых.А.Е Путешествие на планету Знаний
Путешествие на планету Знаний Фундаменты. Классификация
Фундаменты. Классификация Гостевой этикет
Гостевой этикет Интернет жұмыс
Интернет жұмыс Обучение атакующим действиям в футболе юношей 14-15 лет с использованием индивидуальной групповой тактики
Обучение атакующим действиям в футболе юношей 14-15 лет с использованием индивидуальной групповой тактики Развитие спортивно-оздоровительного туризма в России
Развитие спортивно-оздоровительного туризма в России Биологическая обратная связь (БОС) в спорте
Биологическая обратная связь (БОС) в спорте Отчет о практике по получению первичных профессиональных умений и навыков. Объект практики СИУ-филиал РАНХиГС
Отчет о практике по получению первичных профессиональных умений и навыков. Объект практики СИУ-филиал РАНХиГС Нормативная база ценообразования в строительстве
Нормативная база ценообразования в строительстве НЕ продавай себя Не делайтесь рабами людей
НЕ продавай себя Не делайтесь рабами людей Базовый гардероб
Базовый гардероб Общение в Интернете
Общение в Интернете Архитектура ПК. Устройство ПК
Архитектура ПК. Устройство ПК САВАЛА Автор: Данила Гришаев, 2 «Б» класс, СОШ № 2, г.Жердевка, Тамбовская область Руководи
САВАЛА Автор: Данила Гришаев, 2 «Б» класс, СОШ № 2, г.Жердевка, Тамбовская область Руководи Code Validation. CSS reset and validation
Code Validation. CSS reset and validation