Содержание
- 2. Confidential Introduction Senior Software Test Automation Engeneer More than 2 year in EPAM Expertise: UI Test
- 3. Confidential Some rules Listen attentively The rule of hand Turn off your phones Be punctual (song
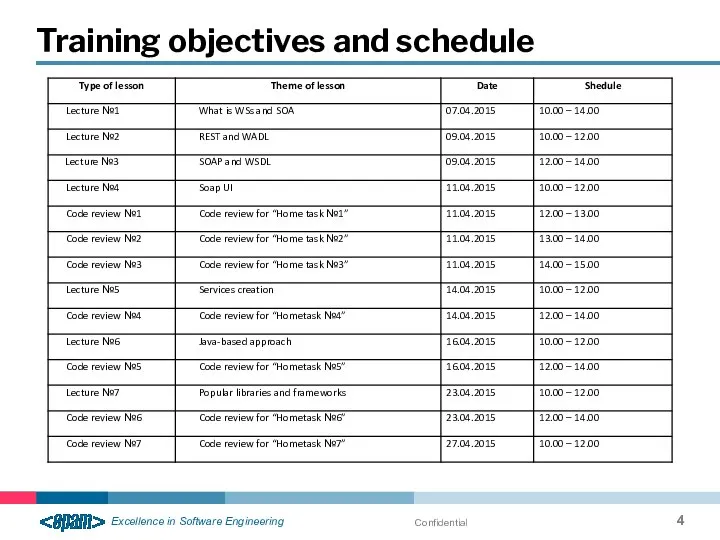
- 4. Confidential Training objectives and schedule
- 5. Confidential Service- Oriented Architecture
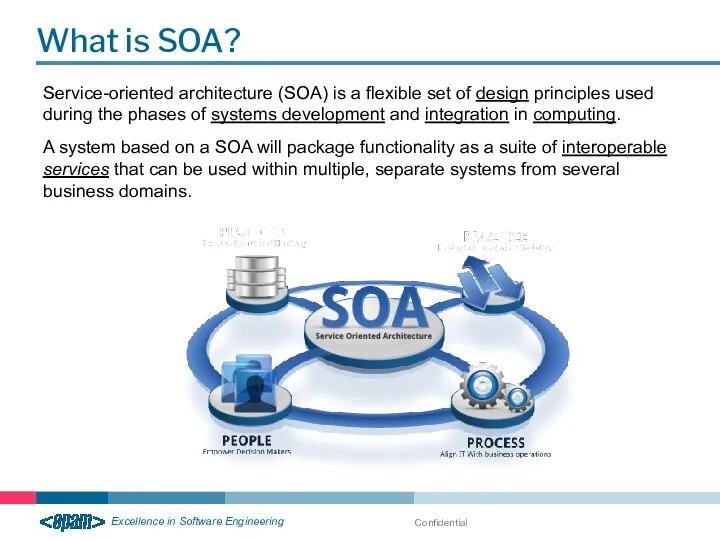
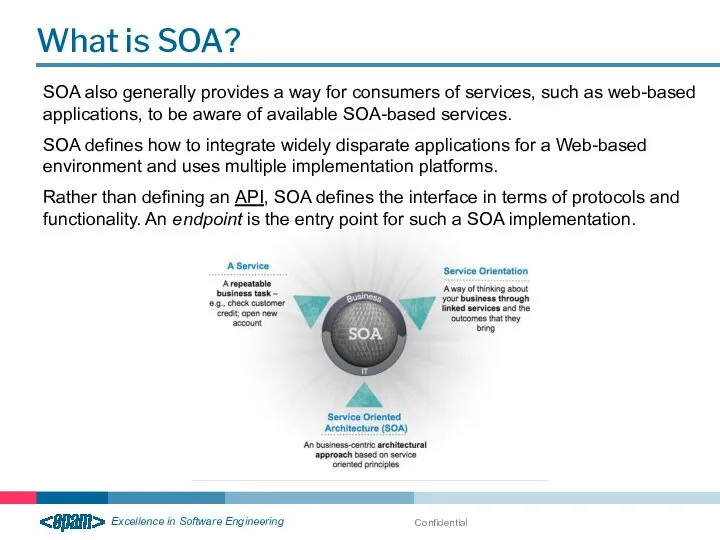
- 6. Confidential What is SOA? Service-oriented architecture (SOA) is a flexible set of design principles used during
- 7. Confidential What is SOA? SOA also generally provides a way for consumers of services, such as
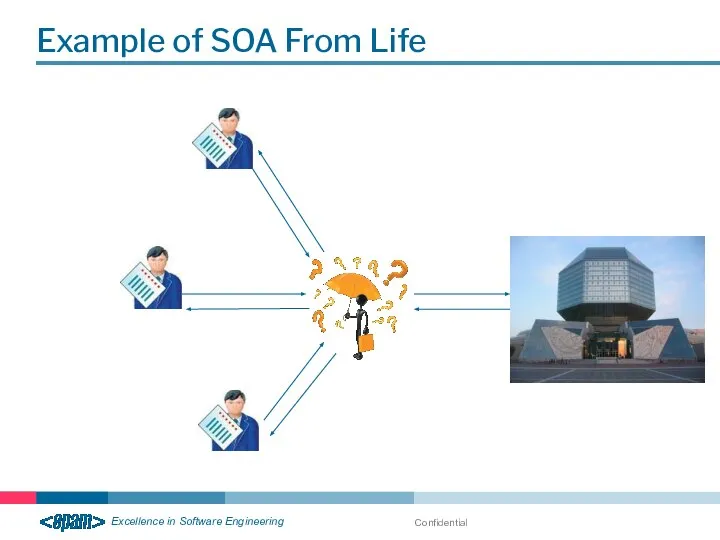
- 8. Confidential Example of SOA From Life
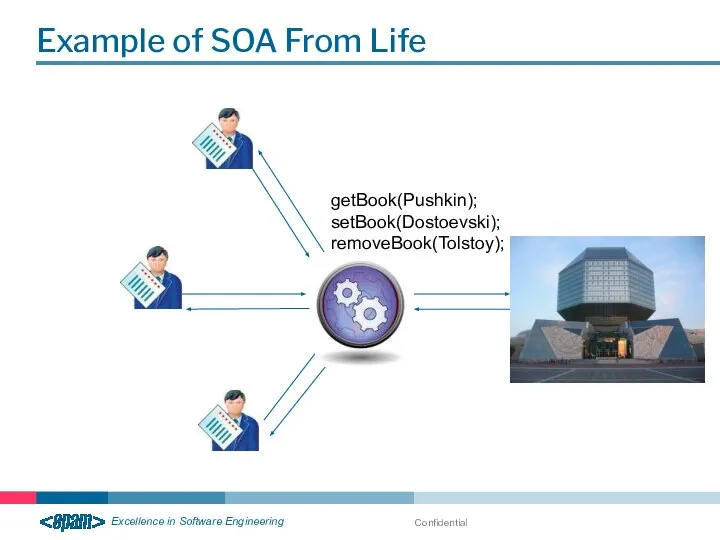
- 9. Confidential Example of SOA From Life getBook(Pushkin); setBook(Dostoevski); removeBook(Tolstoy);
- 10. Confidential SOA Goals Reducing costs when developing applications, due to streamlining the development process; Increased code
- 11. Confidential SOA Principles Architecture is not tied to any particular technology. Independence of the organization system
- 12. Confidential Web- Service
- 13. Confidential Why do we need Web Services?
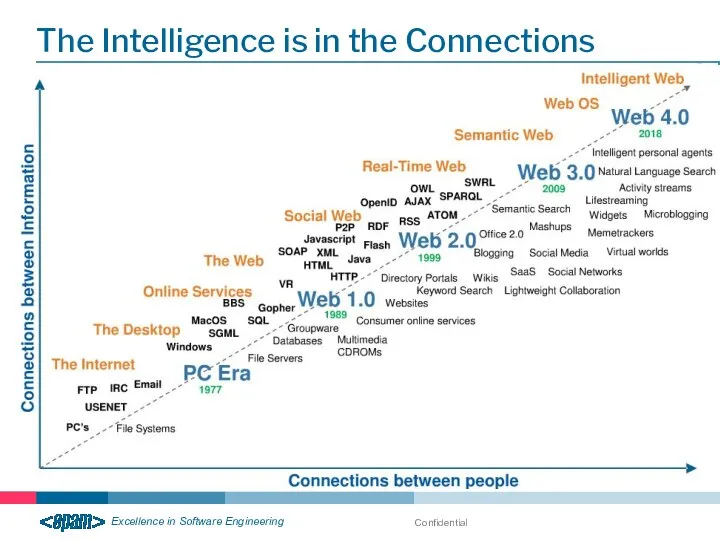
- 14. Confidential The Intelligence is in the Connections
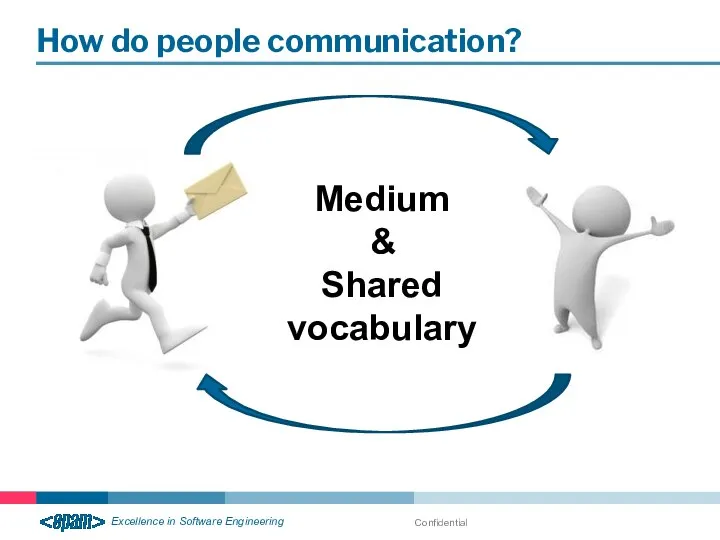
- 15. Confidential How do people communication? Medium & Shared vocabulary
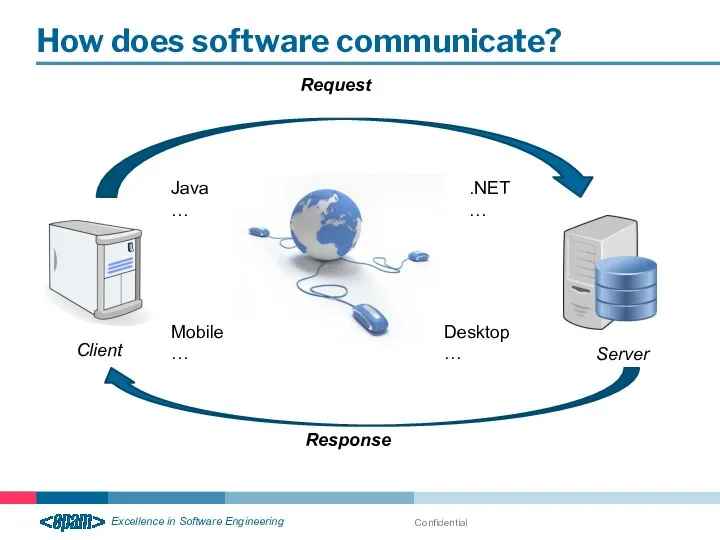
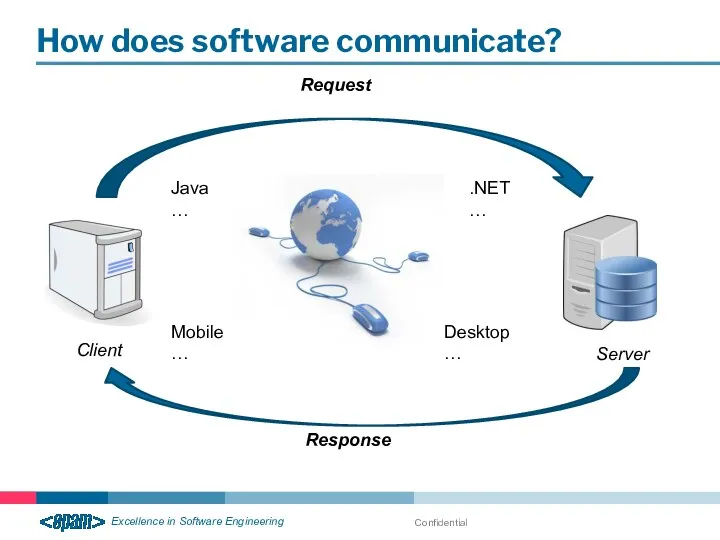
- 16. Confidential How does software communicate? Client Server Java … .NET … Desktop … Mobile … Request
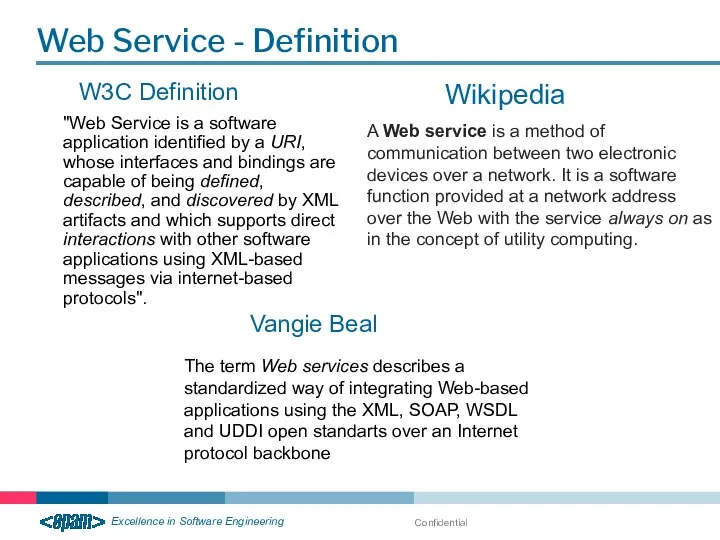
- 17. Confidential Web Service - Definition W3C Definition "Web Service is a software application identified by a
- 18. Confidential Web Service – what are? Web services are application components Communicate using open protocols Can
- 19. Confidential Web Service – type of usage
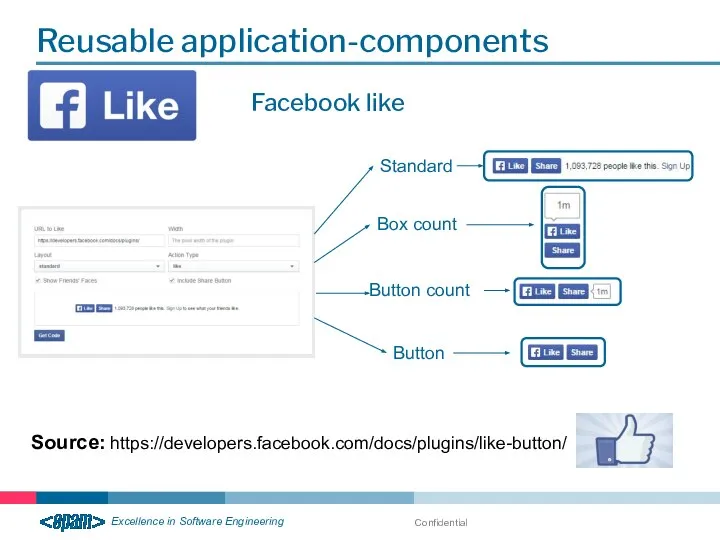
- 20. Confidential Reusable application-components Source: https://developers.facebook.com/docs/plugins/like-button/ Facebook like Standard Box count Button count Button
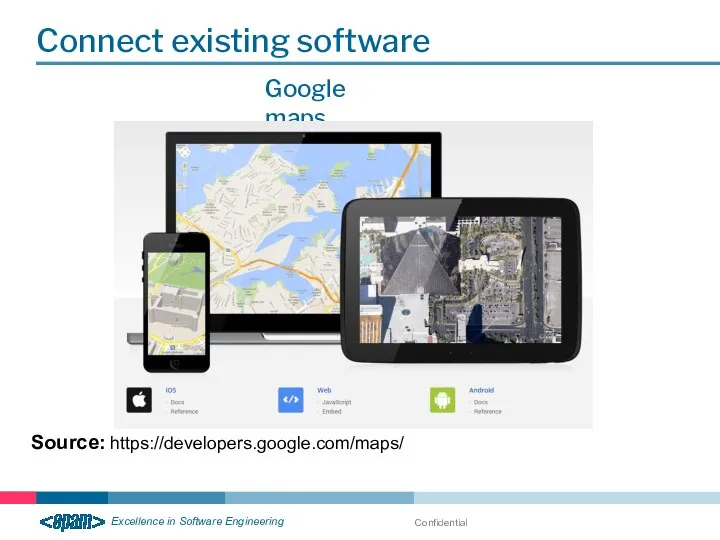
- 21. Confidential Connect existing software Google maps Source: https://developers.google.com/maps/
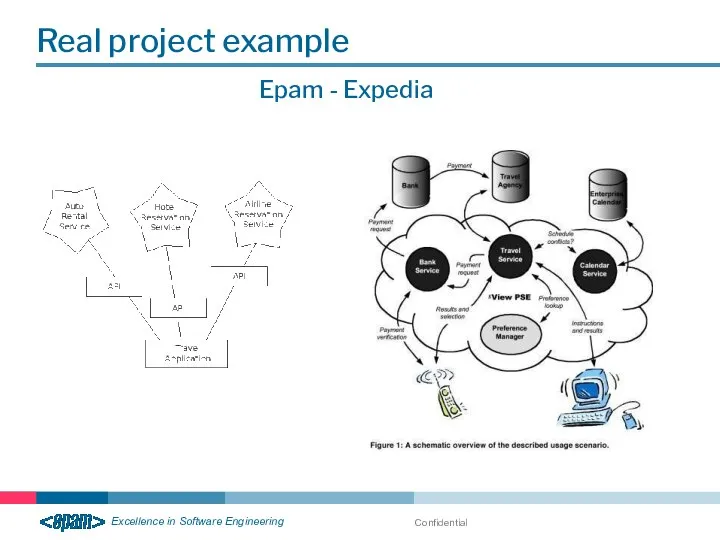
- 22. Confidential Real project example Epam - Expedia
- 23. Confidential Real project example Epam - Expedia
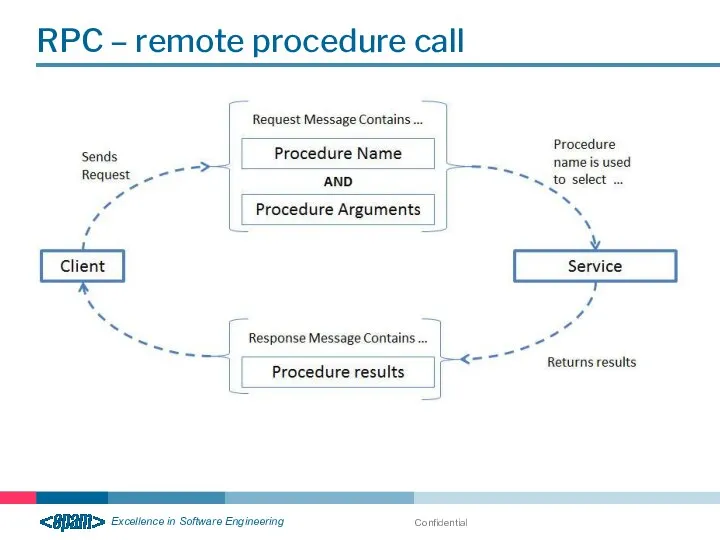
- 24. RPC – remote procedure call Confidential
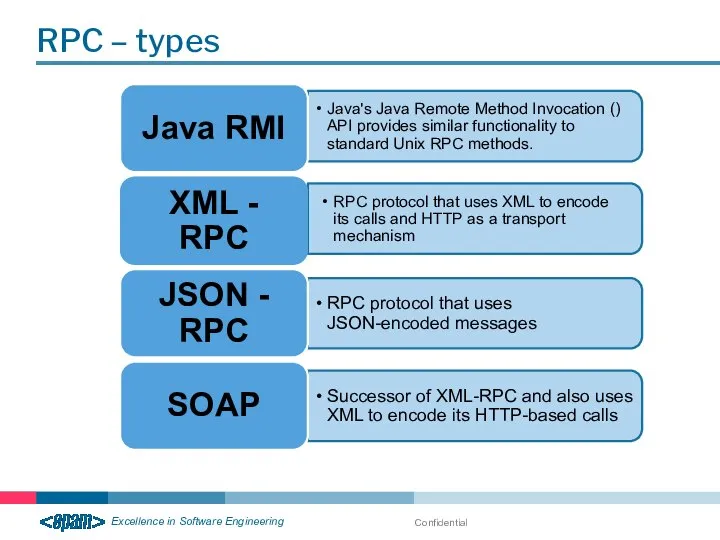
- 25. RPC – types Confidential
- 26. Confidential How does software communicate? Client Server Java … .NET … Desktop … Mobile … Request
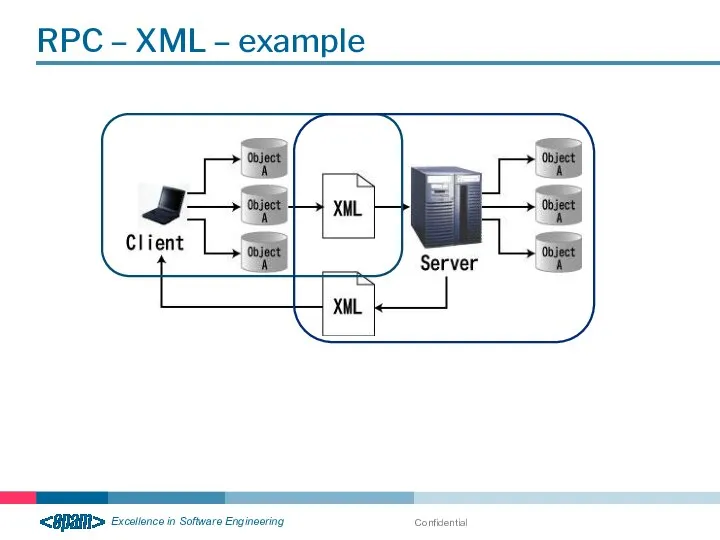
- 27. RPC – XML – example Confidential
- 28. Confidential Web services & Web applications
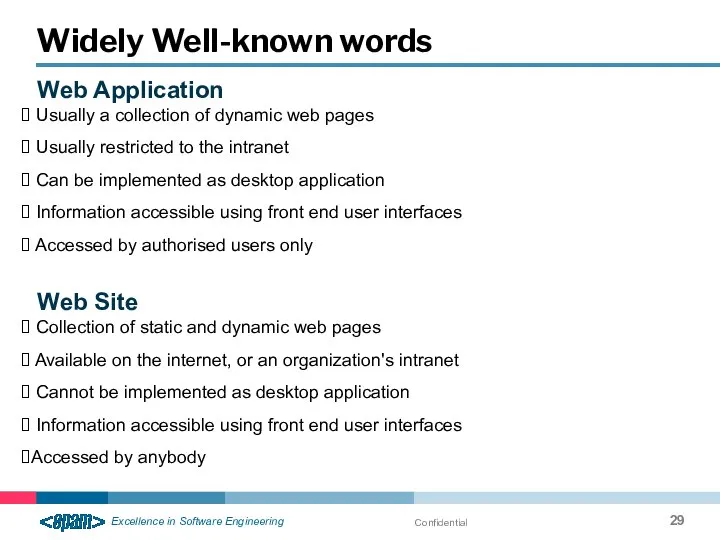
- 29. Confidential Widely Well-known words Web Application Usually a collection of dynamic web pages Usually restricted to
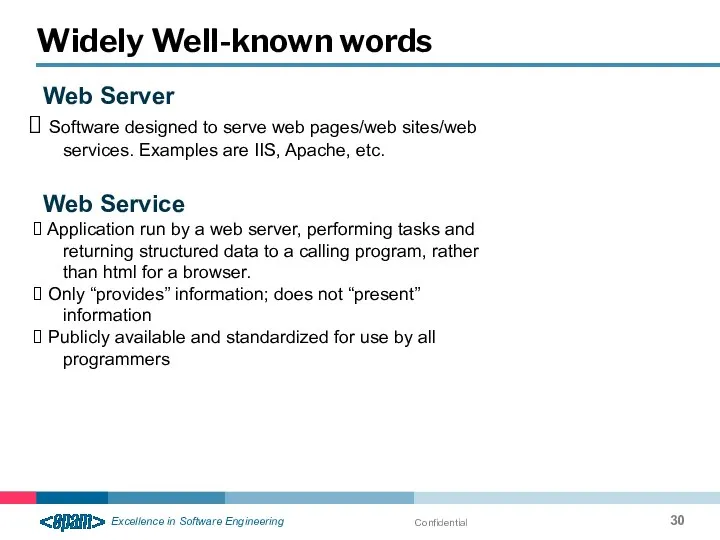
- 30. Confidential Widely Well-known words Web Server Software designed to serve web pages/web sites/web services. Examples are
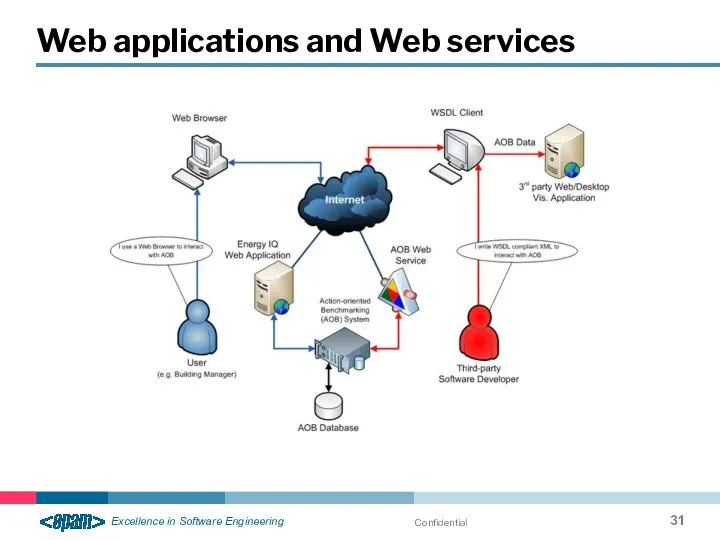
- 31. Confidential Web applications and Web services
- 32. Confidential Extensible Markup Language (XML)
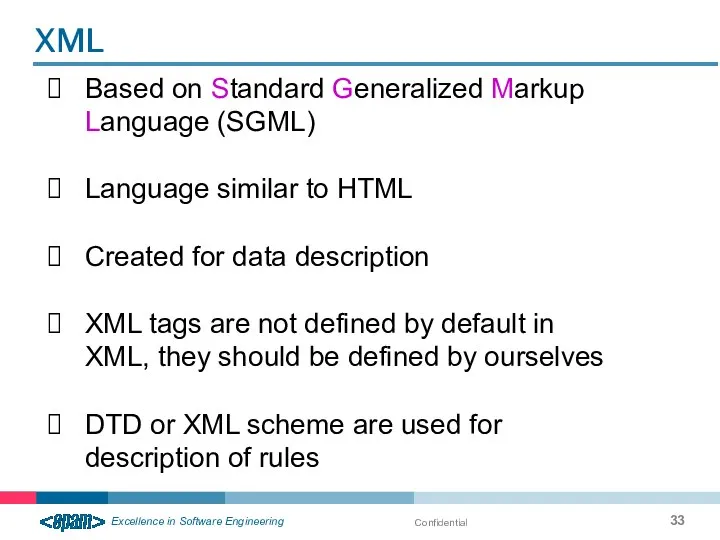
- 33. Confidential Based on Standard Generalized Markup Language (SGML) Language similar to HTML Created for data description
- 34. Confidential XML data can be stored as in separate file as well as inside of HTML,
- 35. Confidential Give the life for derived from the XML languages like WAP and WML For communication
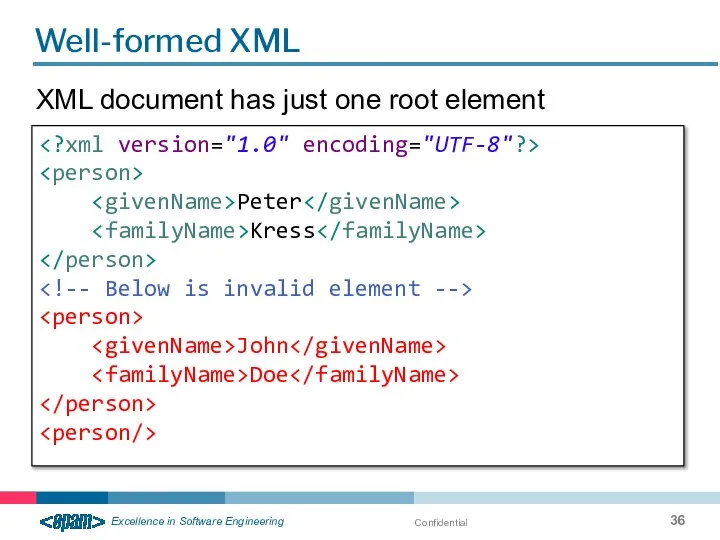
- 36. Confidential Well-formed XML Peter Kress John Doe XML document has just one root element
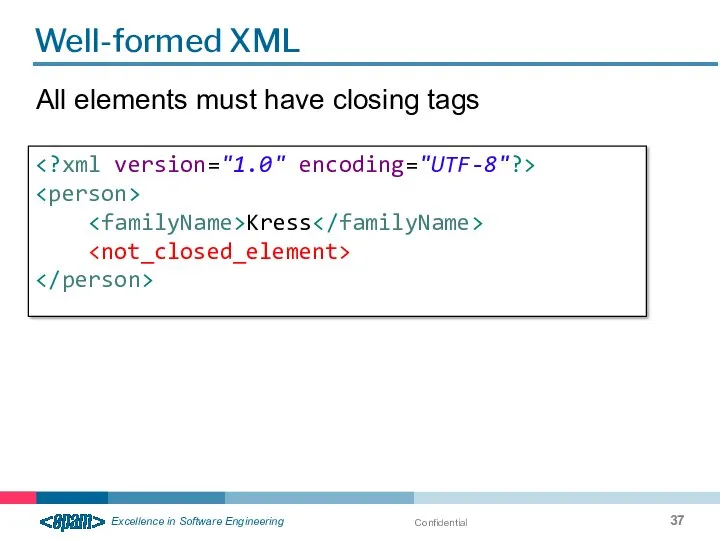
- 37. Confidential Well-formed XML All elements must have closing tags Kress
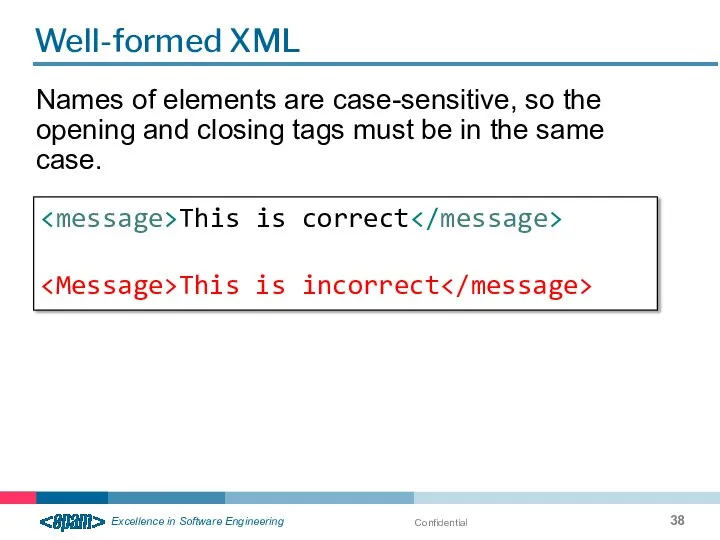
- 38. Confidential Well-formed XML Names of elements are case-sensitive, so the opening and closing tags must be
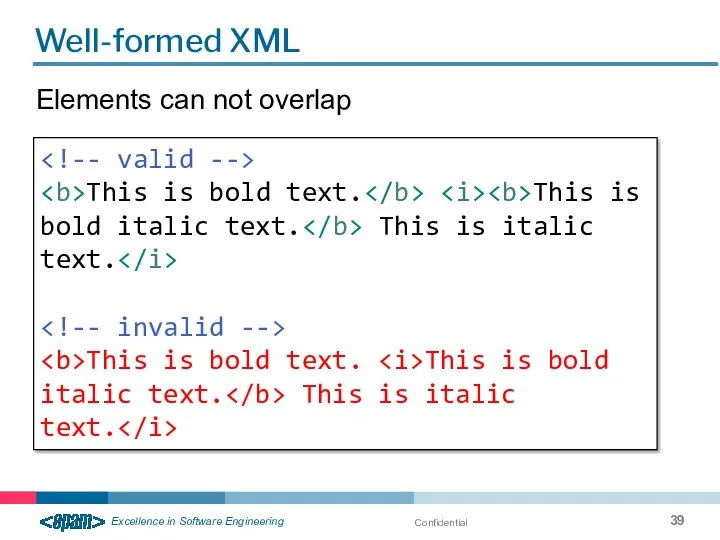
- 39. Confidential Well-formed XML Elements can not overlap This is bold text. This is bold italic text.
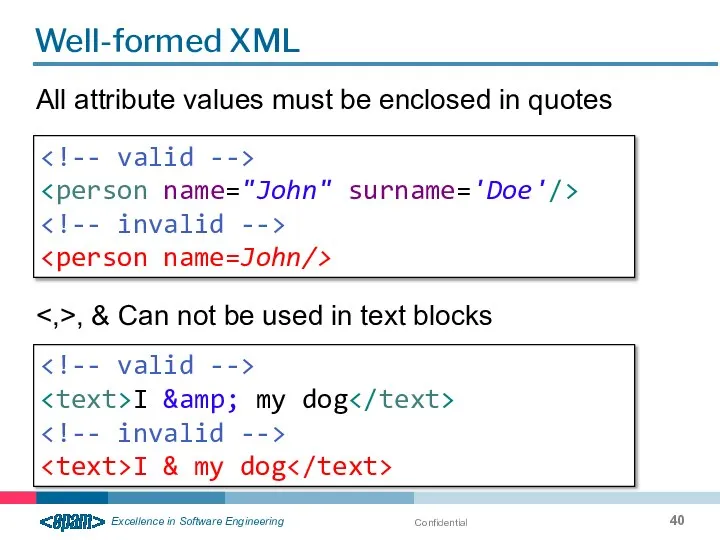
- 40. Confidential Well-formed XML All attribute values must be enclosed in quotes I & my dog I
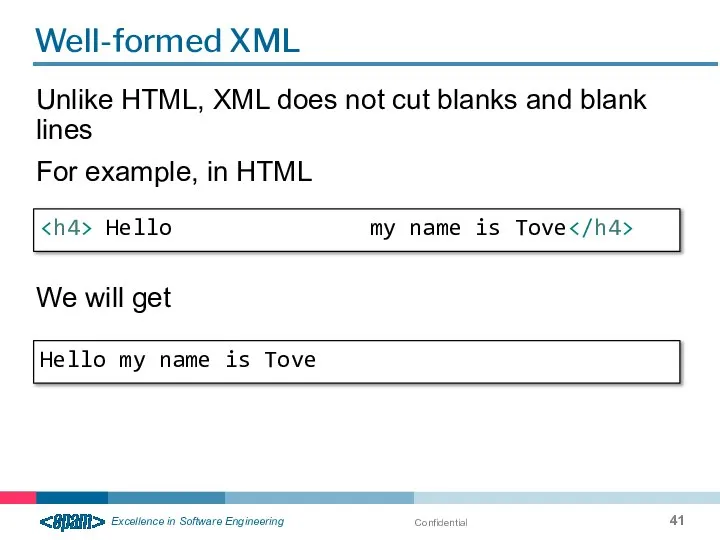
- 41. Confidential Well-formed XML Unlike HTML, XML does not cut blanks and blank lines Hello my name
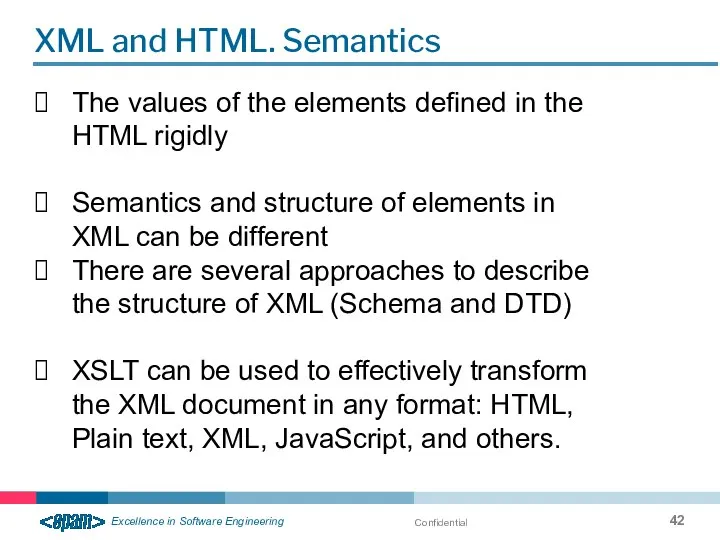
- 42. Confidential XML and HTML. Semantics The values of the elements defined in the HTML rigidly Semantics
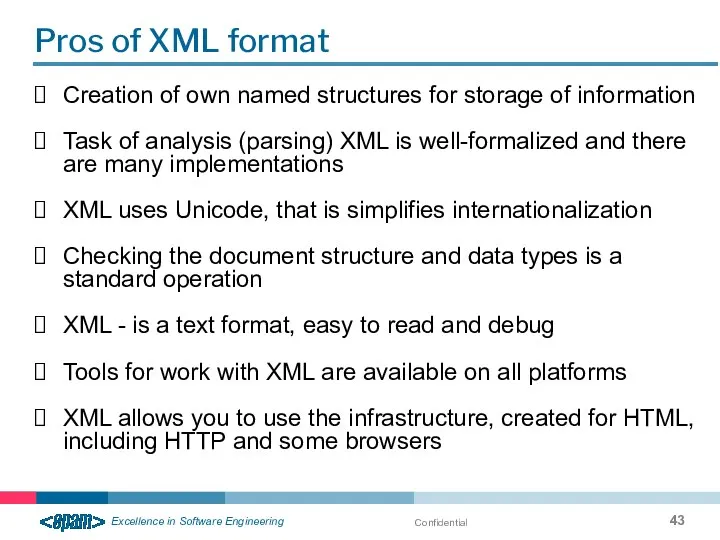
- 43. Confidential Pros of XML format Creation of own named structures for storage of information Task of
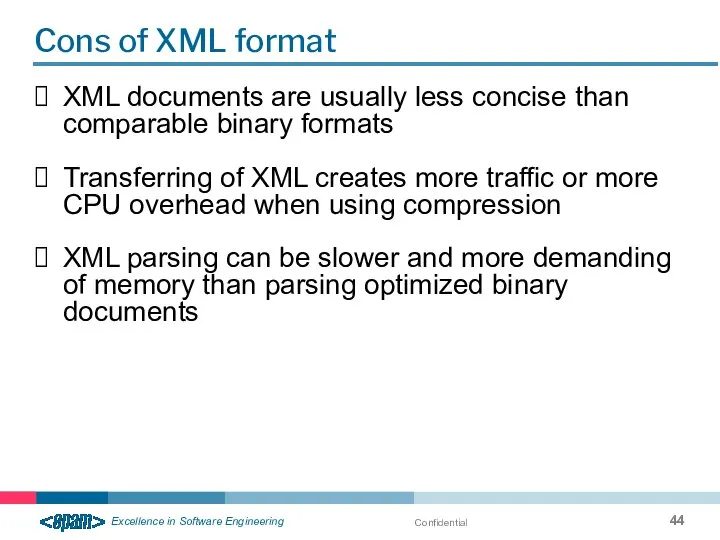
- 44. Confidential Cons of XML format XML documents are usually less concise than comparable binary formats Transferring
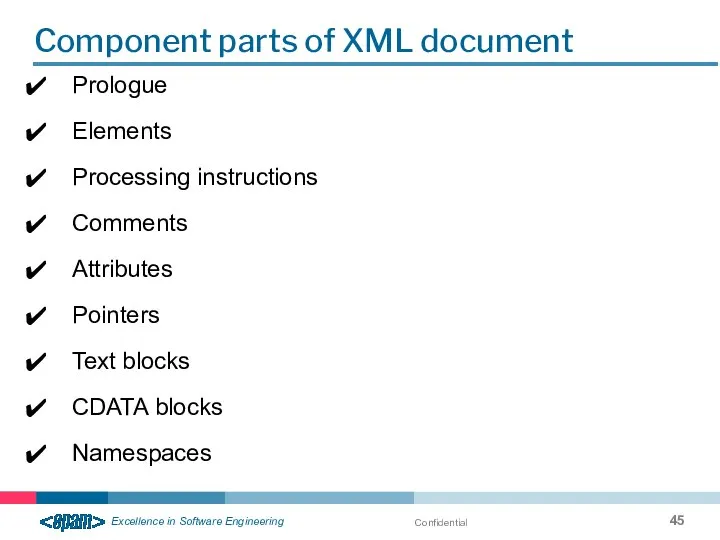
- 45. Confidential Component parts of XML document Prologue Elements Processing instructions Comments Attributes Pointers Text blocks CDATA
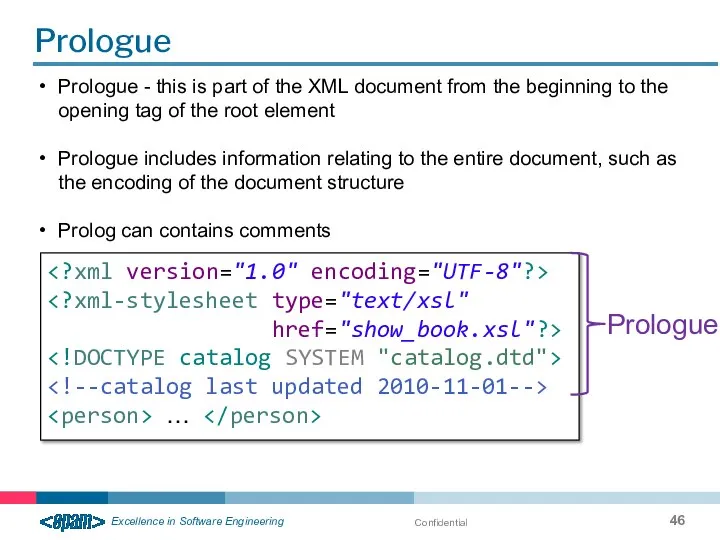
- 46. Confidential Prologue href="show_book.xsl"?> … Prologue Prologue - this is part of the XML document from the
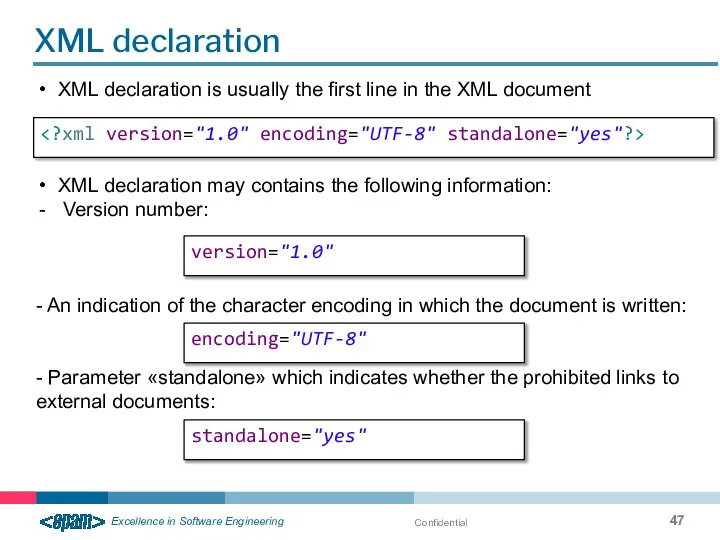
- 47. Confidential XML declaration version="1.0" encoding="UTF-8" standalone="yes" XML declaration is usually the first line in the XML
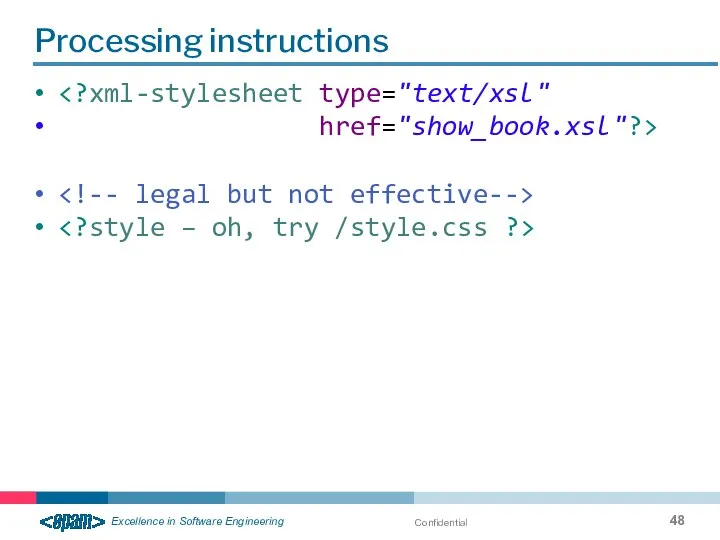
- 48. Confidential Processing instructions href="show_book.xsl"?>
- 49. Confidential The DOCTYPE declaration declarations ]>
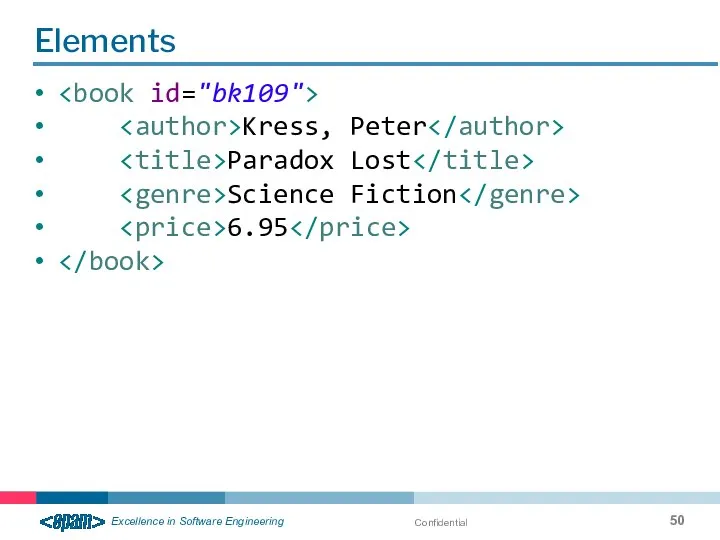
- 50. Confidential Elements Kress, Peter Paradox Lost Science Fiction 6.95
- 51. Confidential Tags att2Name="att2Value" ...> att2Name="att2Value" ... /> Tags define the boundaries of the element Opening tags
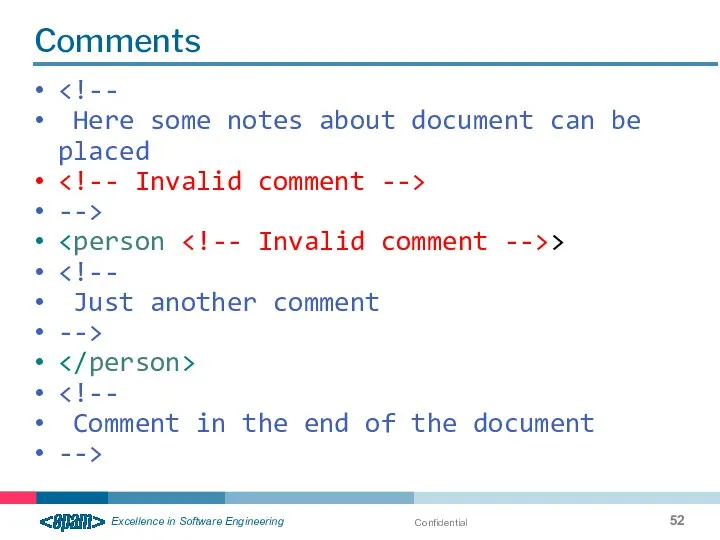
- 52. Confidential Comments Here some notes about document can be placed --> > Just another comment -->
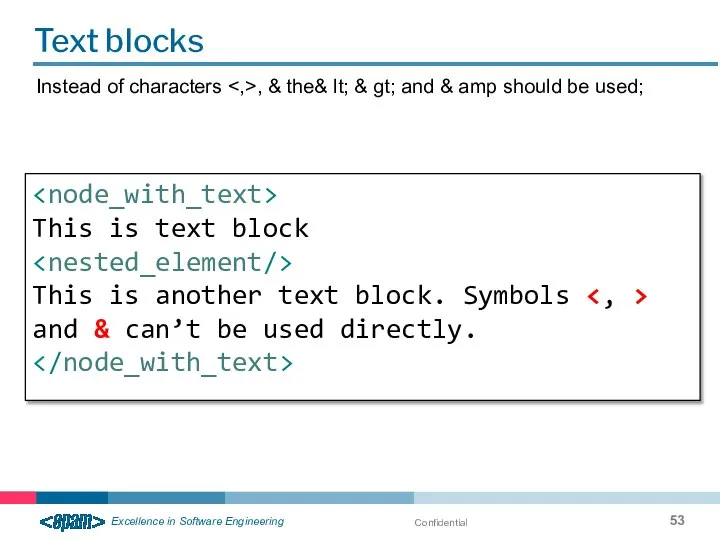
- 53. Confidential Text blocks Instead of characters , & the& lt; & gt; and & amp should
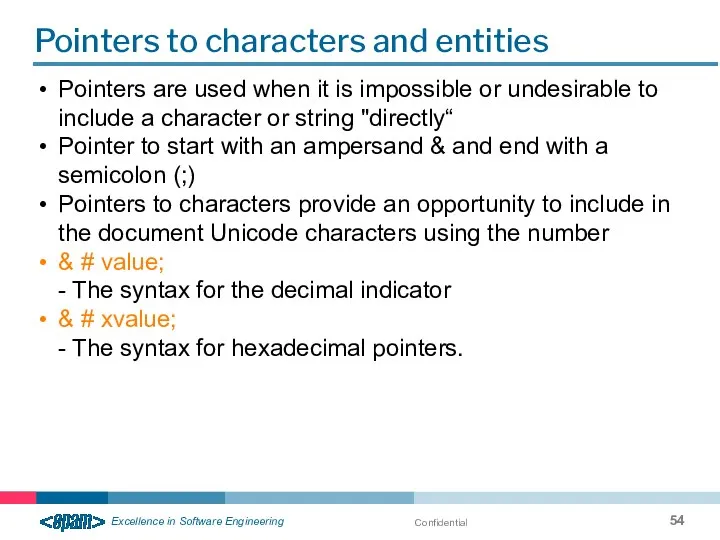
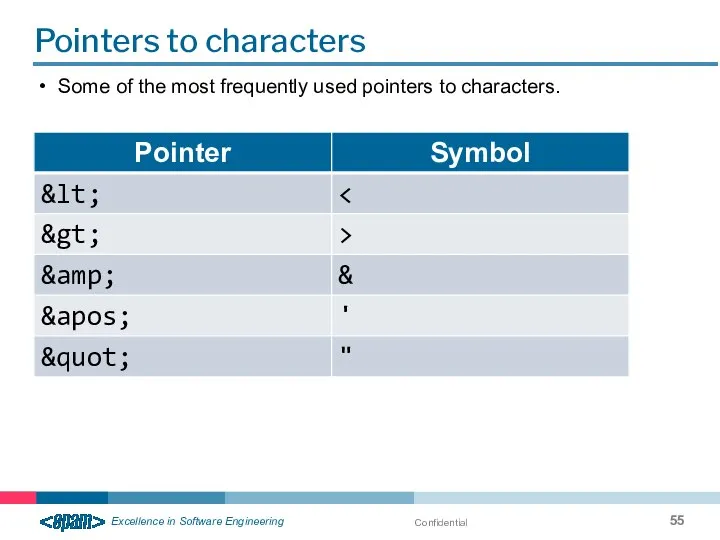
- 54. Confidential Pointers to characters and entities Pointers are used when it is impossible or undesirable to
- 55. Confidential Pointers to characters Some of the most frequently used pointers to characters.
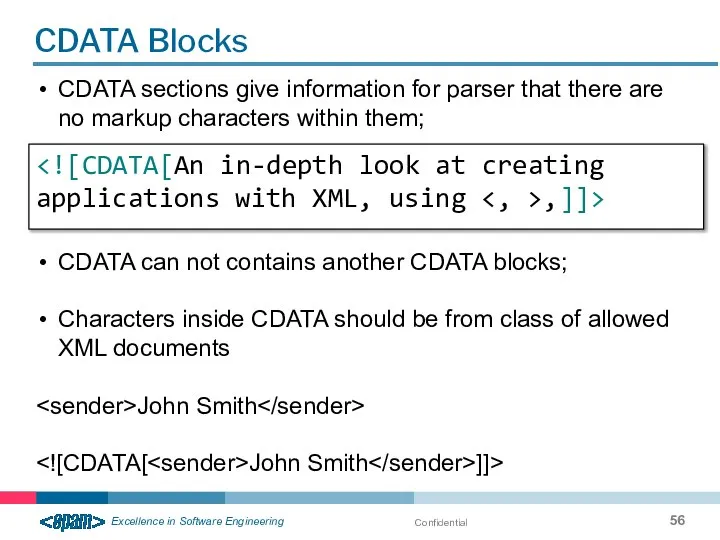
- 56. Confidential CDATA Blocks CDATA sections give information for parser that there are no markup characters within
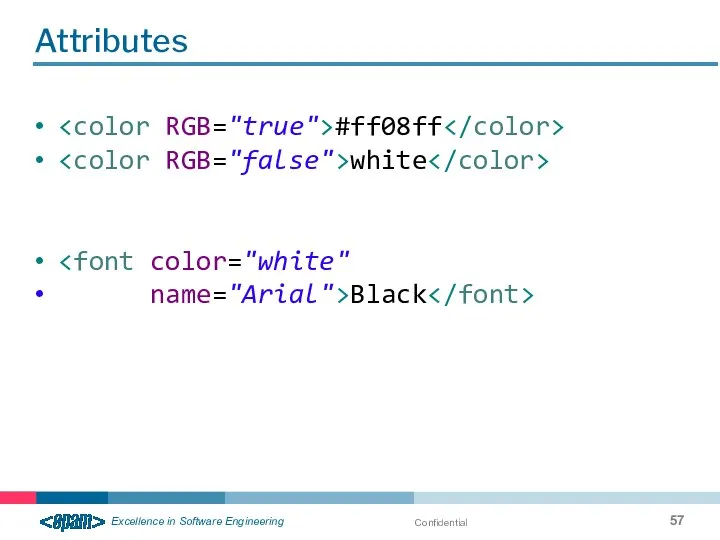
- 57. Confidential Attributes #ff08ff white name="Arial">Black
- 58. Confidential Usage of Namespaces XML namespace – is the collection of the names identifiable by reference
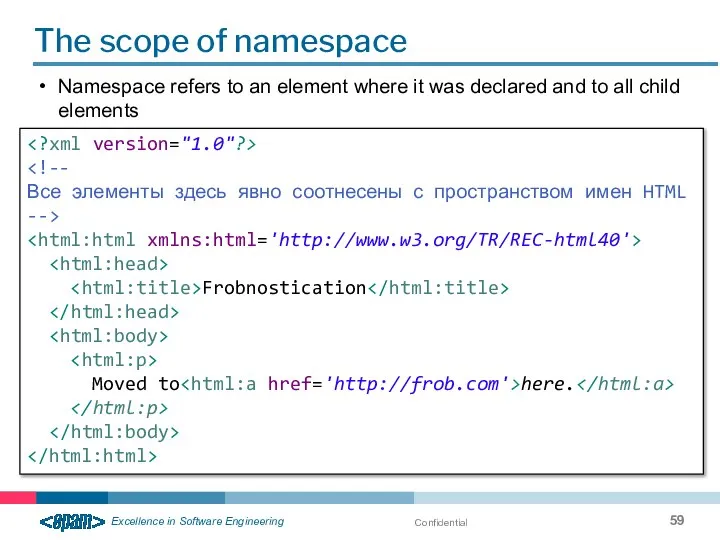
- 59. Confidential The scope of namespace Namespace refers to an element where it was declared and to
- 60. Confidential XSD
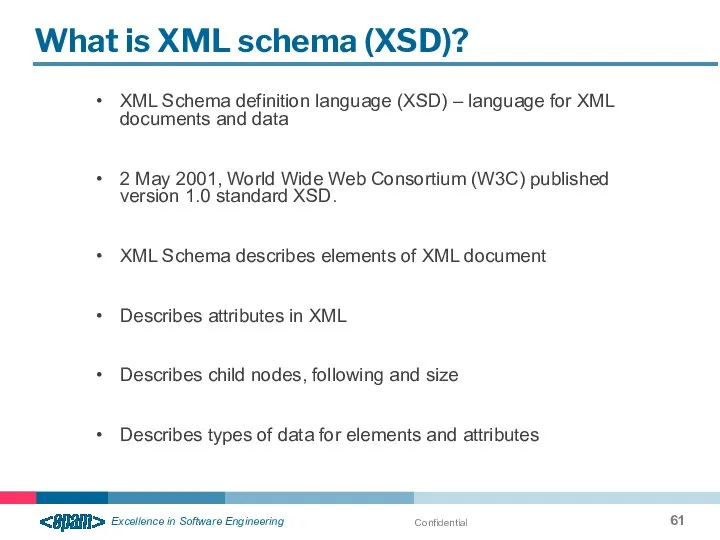
- 61. Confidential What is XML schema (XSD)? XML Schema definition language (XSD) – language for XML documents
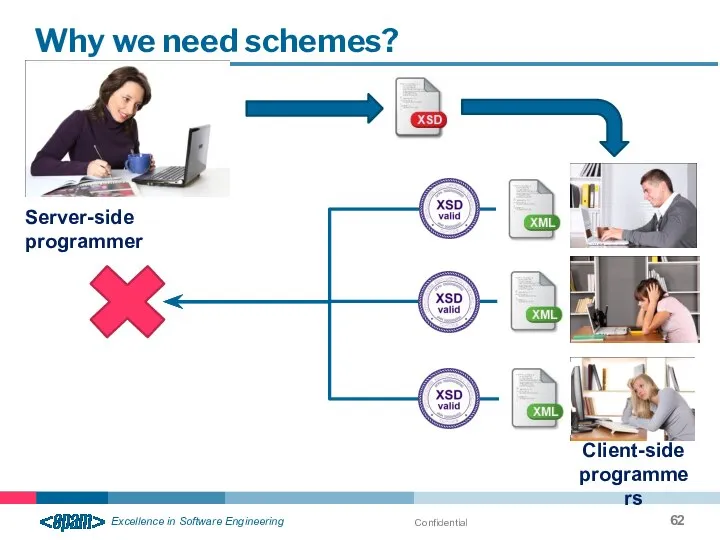
- 62. Confidential Why we need schemes? Server-side programmer Client-side programmers
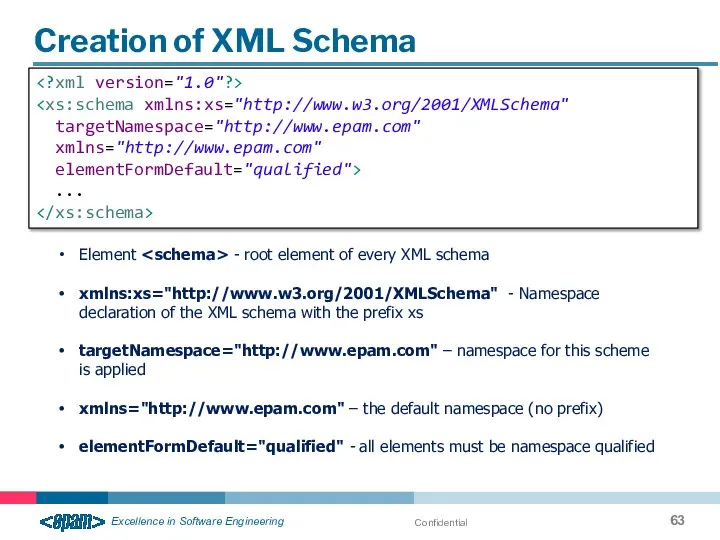
- 63. Confidential Creation of XML Schema targetNamespace="http://www.epam.com" xmlns="http://www.epam.com" elementFormDefault="qualified"> ... Element - root element of every XML
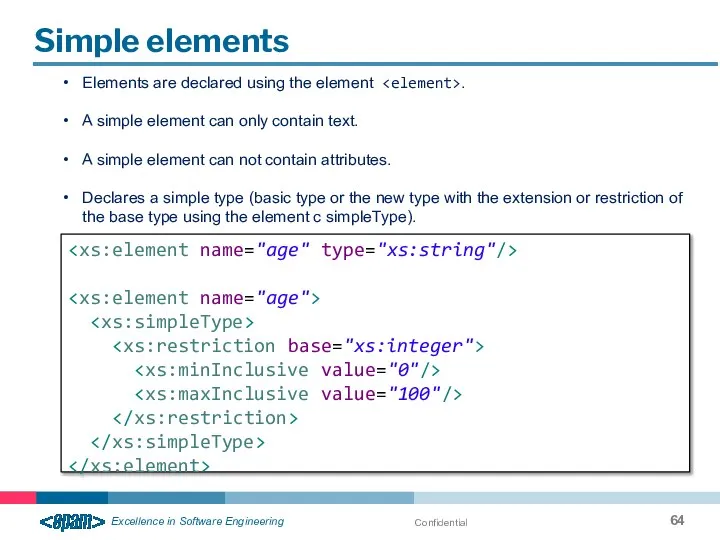
- 64. Confidential Simple elements Elements are declared using the element . A simple element can only contain
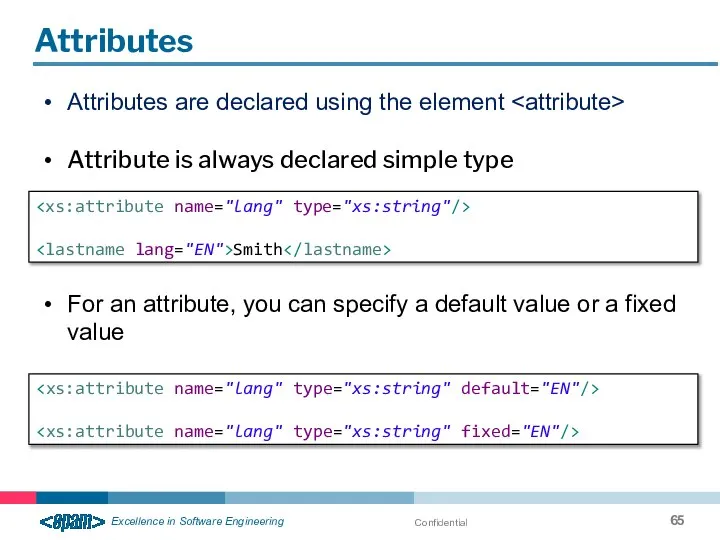
- 65. Confidential Attributes Attributes are declared using the element Attribute is always declared simple type For an
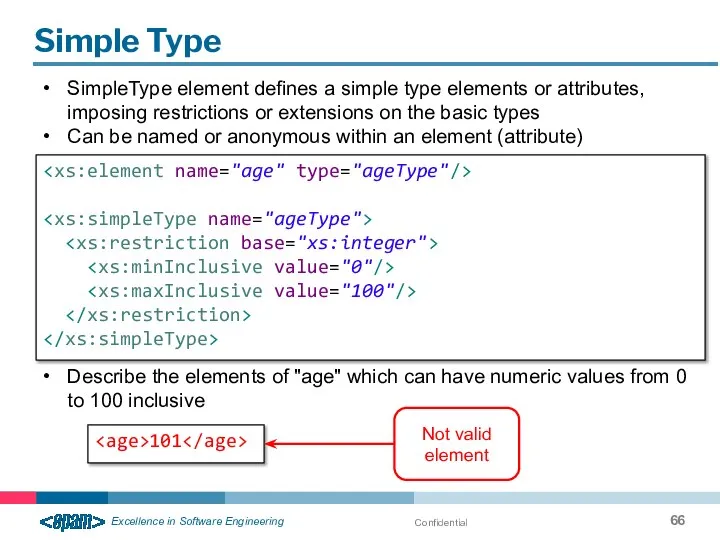
- 66. Confidential Simple Type SimpleType element defines a simple type elements or attributes, imposing restrictions or extensions
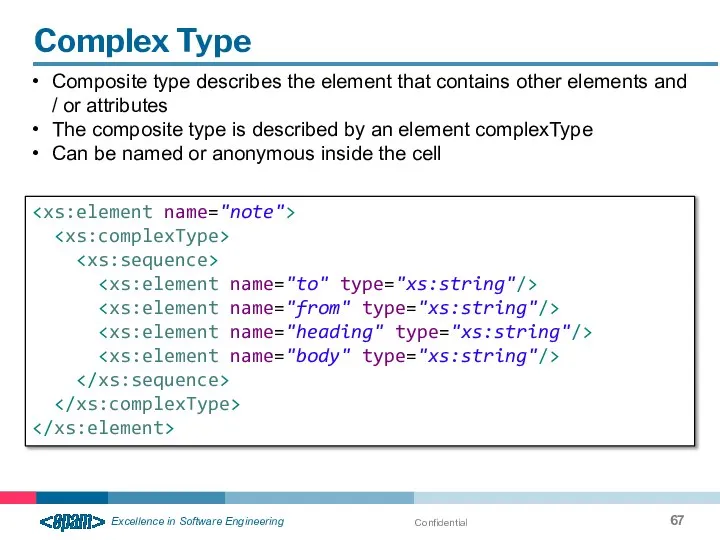
- 67. Confidential Complex Type Composite type describes the element that contains other elements and / or attributes
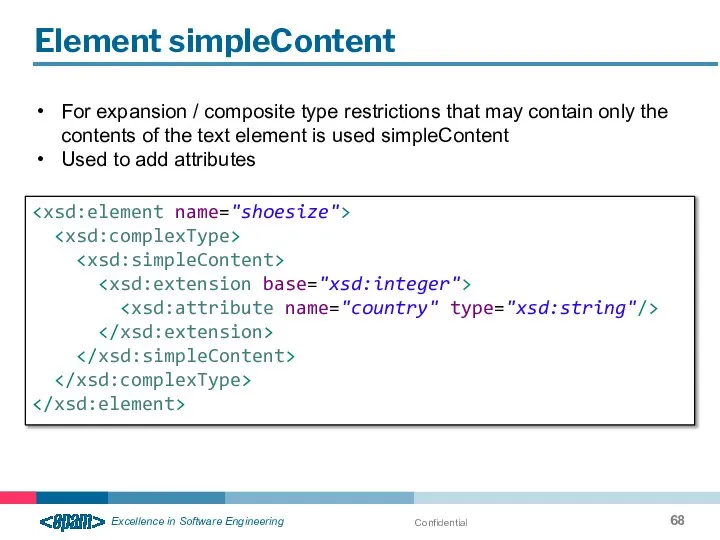
- 68. Confidential Element simpleContent For expansion / composite type restrictions that may contain only the contents of
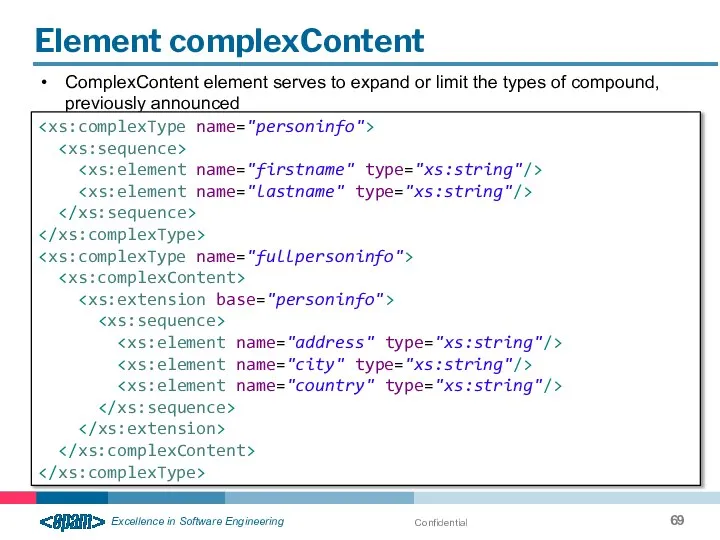
- 69. Confidential Element complexContent ComplexContent element serves to expand or limit the types of compound, previously announced
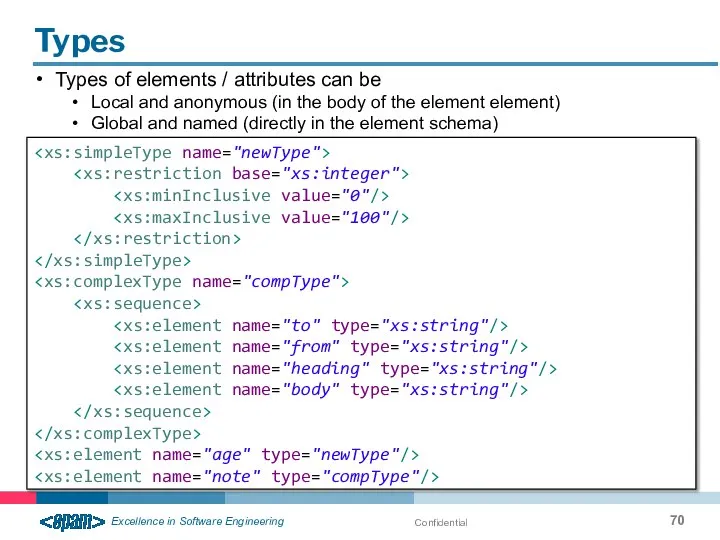
- 70. Confidential Types Types of elements / attributes can be Local and anonymous (in the body of
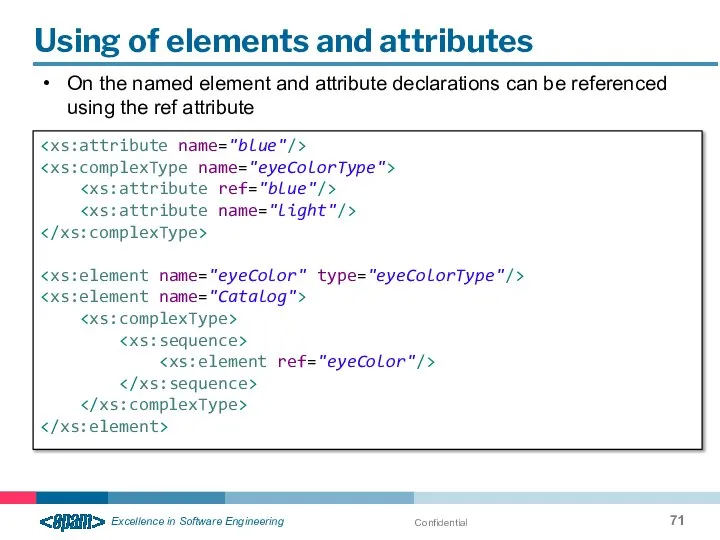
- 71. Confidential Using of elements and attributes On the named element and attribute declarations can be referenced
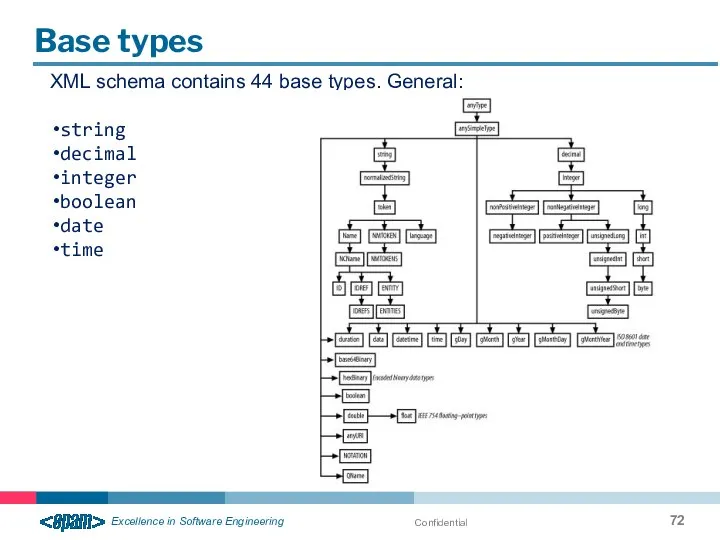
- 72. Confidential Base types XML schema contains 44 base types. General: string decimal integer boolean date time
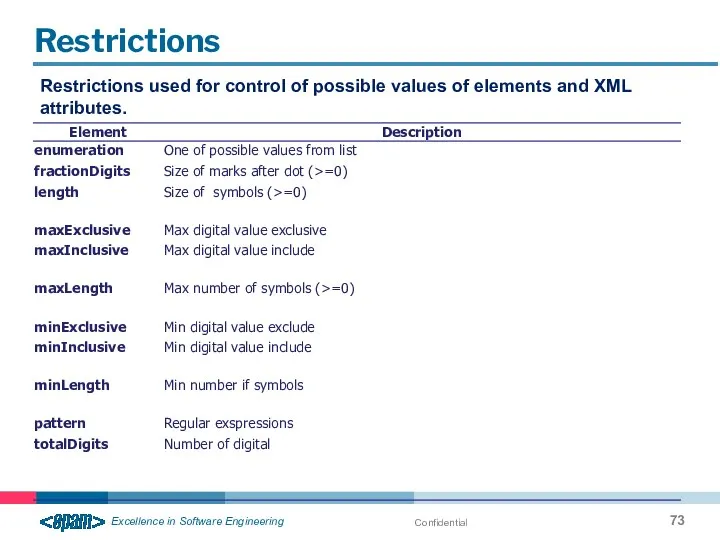
- 73. Confidential Restrictions Restrictions used for control of possible values of elements and XML attributes.
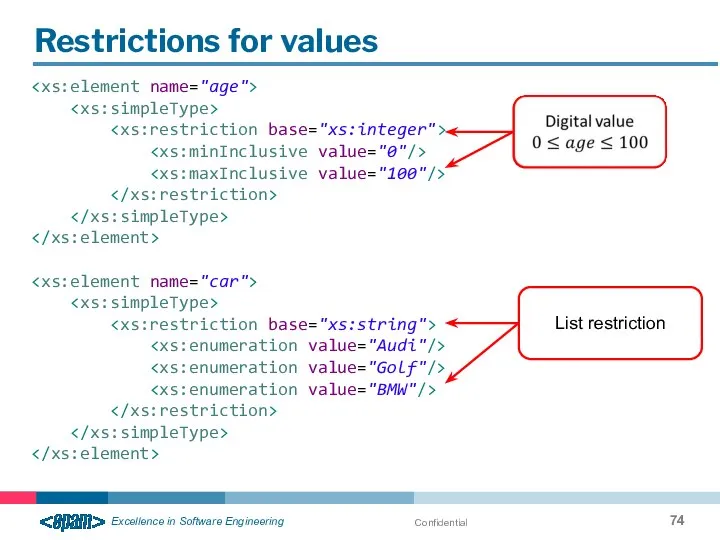
- 74. Confidential Restrictions for values List restriction
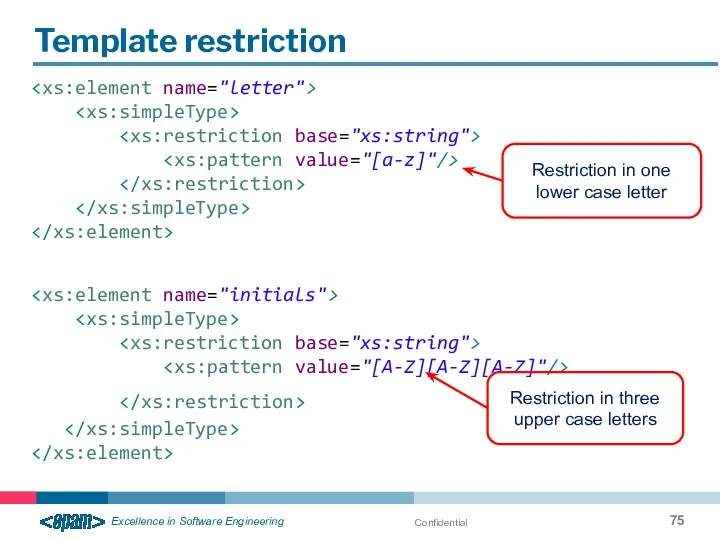
- 75. Confidential Template restriction Restriction in one lower case letter Restriction in three upper case letters
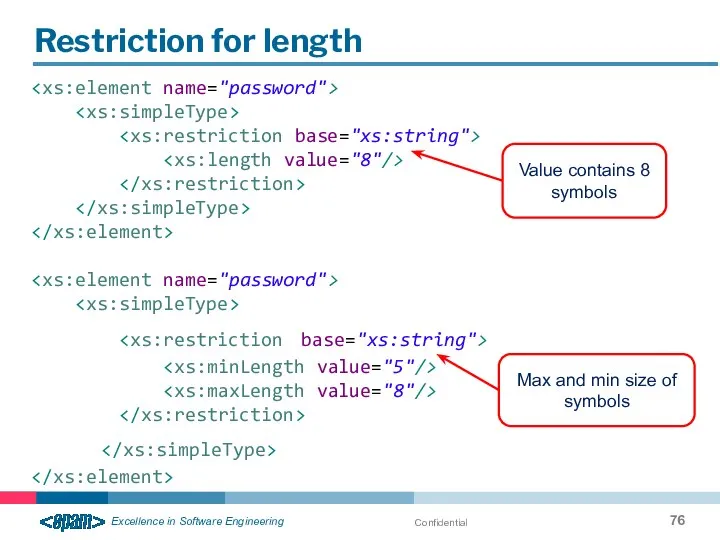
- 76. Confidential Restriction for length Value contains 8 symbols Max and min size of symbols
- 77. Confidential White spaces restriction Restriction whiteSpace can have 3 values: preserve – leave all white spaces
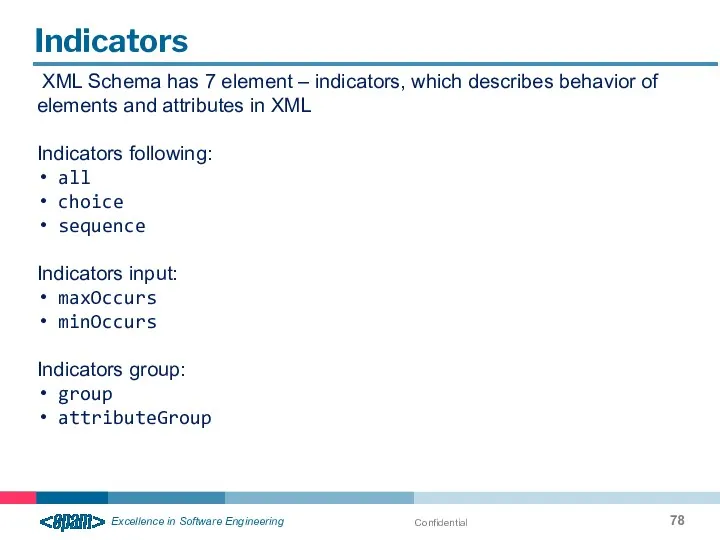
- 78. Confidential Indicators XML Schema has 7 element – indicators, which describes behavior of elements and attributes
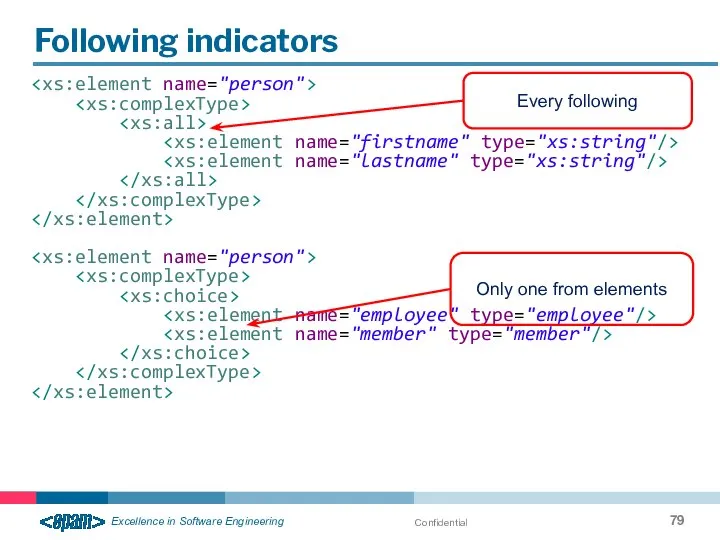
- 79. Confidential Following indicators Every following Only one from elements
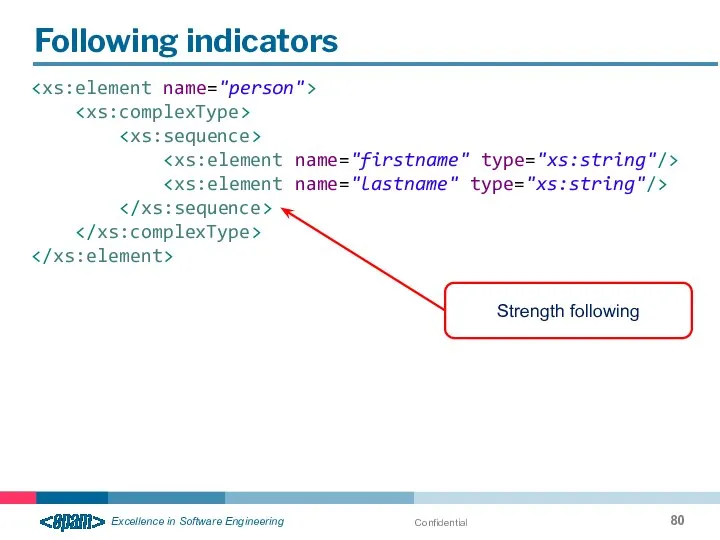
- 80. Confidential Following indicators Strength following
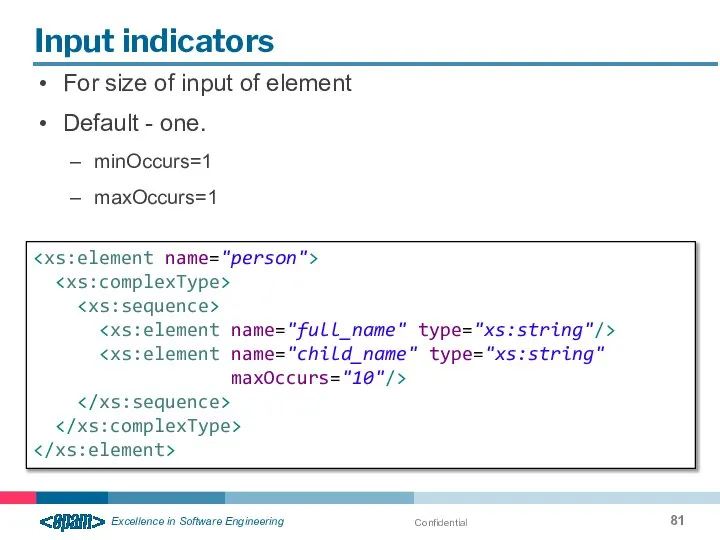
- 81. Confidential Input indicators For size of input of element Default - one. minOccurs=1 maxOccurs=1 maxOccurs="10"/>
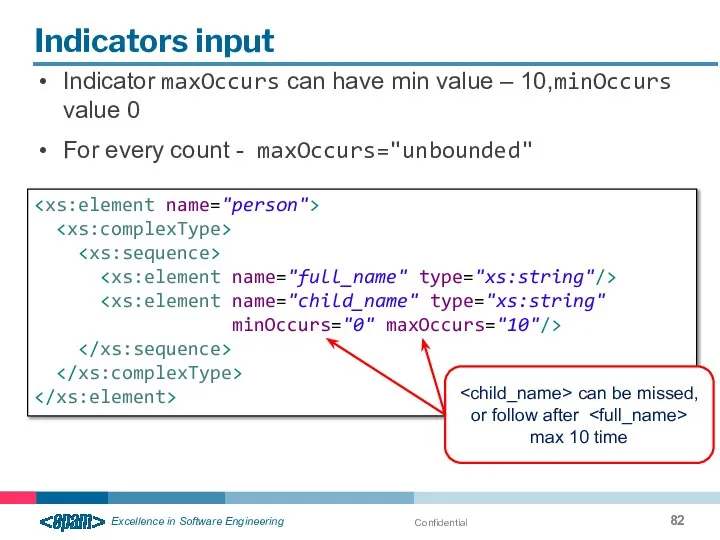
- 82. Confidential Indicators input Indicator maxOccurs can have min value – 10,minOccurs value 0 For every count
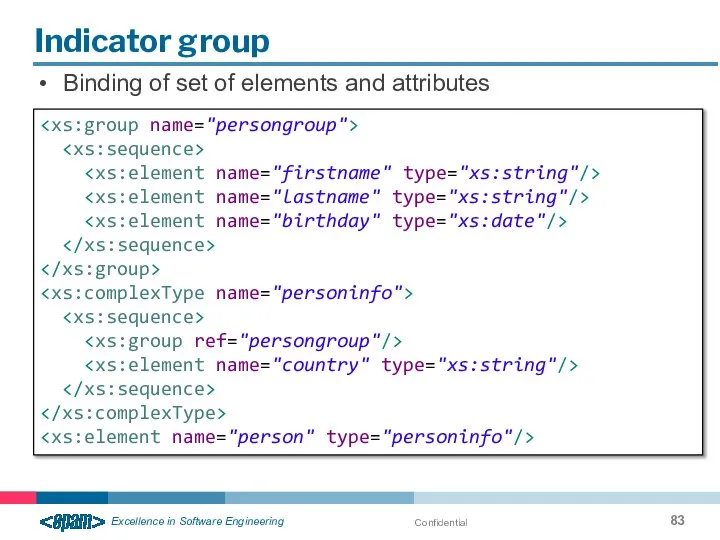
- 83. Confidential Indicator group Binding of set of elements and attributes
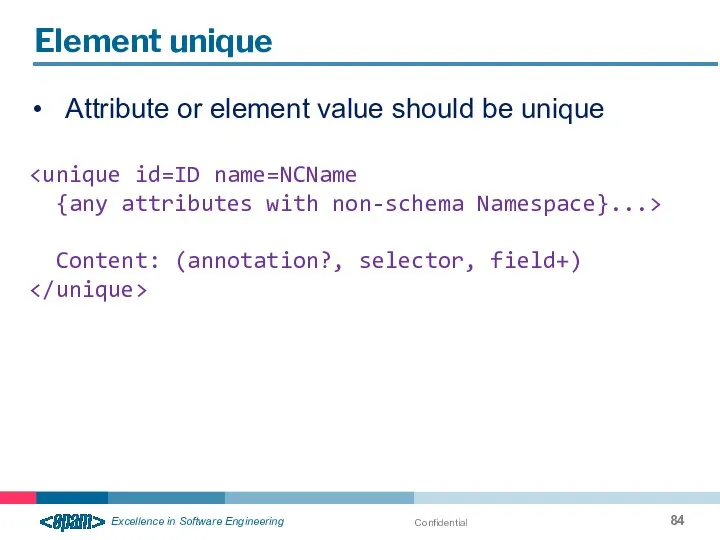
- 84. Confidential Element unique Attribute or element value should be unique {any attributes with non-schema Namespace}...> Content:
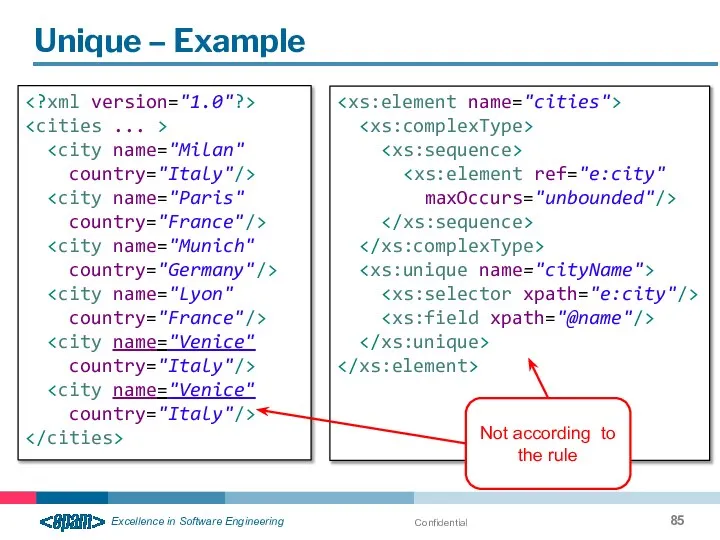
- 85. Confidential Unique – Example country="Italy"/> country="France"/> country="Germany"/> country="France"/> country="Italy"/> country="Italy"/> maxOccurs="unbounded"/> Not according to the rule
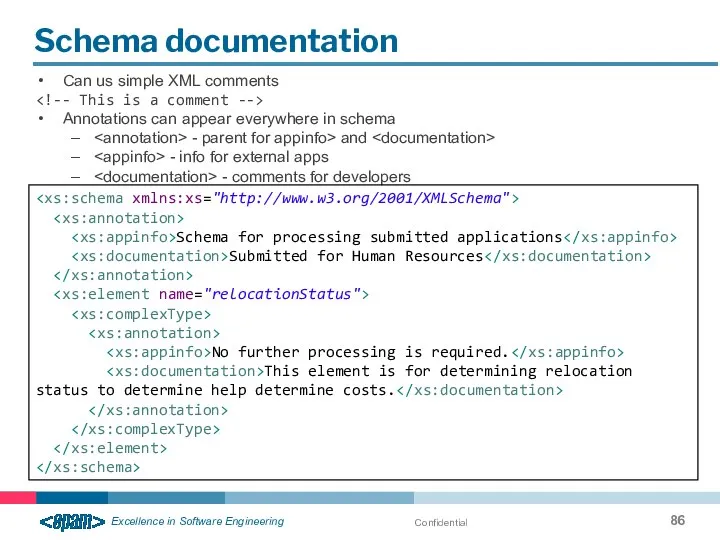
- 86. Confidential Schema documentation Can us simple XML comments Annotations can appear everywhere in schema - parent
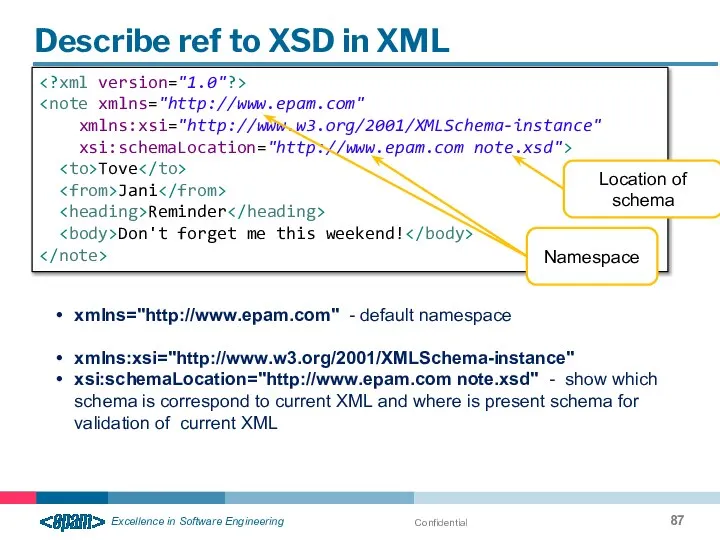
- 87. Confidential Describe ref to XSD in XML xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.epam.com note.xsd"> Tove Jani Reminder Don't forget me
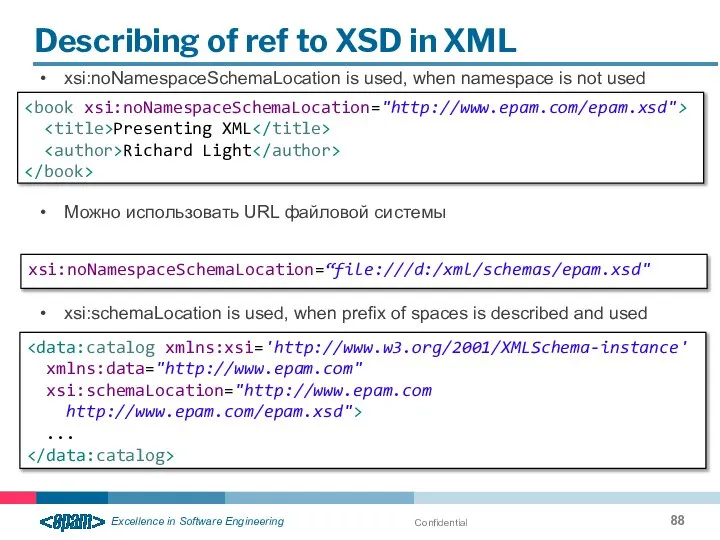
- 88. Confidential Describing of ref to XSD in XML xsi:noNamespaceSchemaLocation is used, when namespace is not used
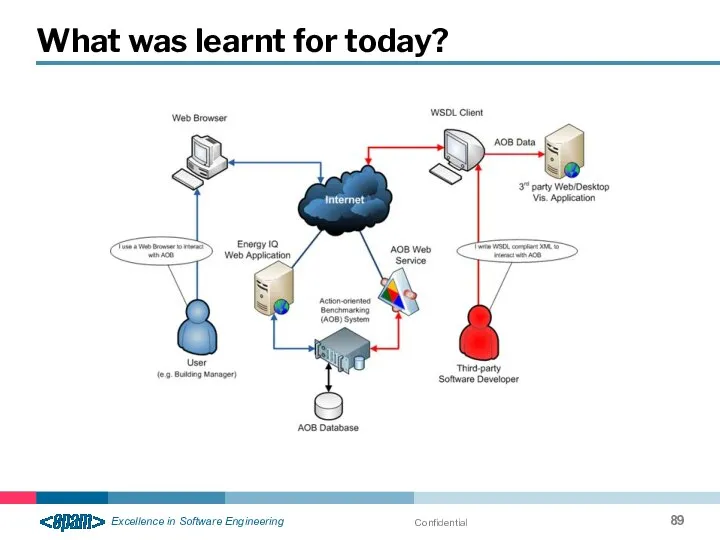
- 89. Confidential What was learnt for today?
- 90. Confidential What was learnt for today? Web application / Web site / Web Server Web service
- 92. Скачать презентацию







![Confidential The DOCTYPE declaration declarations ]>](/_ipx/f_webp&q_80&fit_contain&s_1440x1080/imagesDir/jpg/1374972/slide-48.jpg)



 Проектирование коллекций
Проектирование коллекций Древняя Индия
Древняя Индия История и версии ОС MicroSoft
История и версии ОС MicroSoft Предприятие АО "РКЦ "Прогресс"
Предприятие АО "РКЦ "Прогресс" Василий Андреев (создатель и руководитель первого в России оркестра народных инструментов)
Василий Андреев (создатель и руководитель первого в России оркестра народных инструментов) Свойства для размещения и размера элементов
Свойства для размещения и размера элементов Үзе укый белмәсә дә, Гомер буе язын
Үзе укый белмәсә дә, Гомер буе язын Решение квадратных уравнений Выполнили учителя Мкоу гимназии вятские поляны: Гатауллина гульфия анасовна и малькова надежда вас
Решение квадратных уравнений Выполнили учителя Мкоу гимназии вятские поляны: Гатауллина гульфия анасовна и малькова надежда вас БЕЗОПАСНОСТЬ В БЫТОВОЙ СРЕДЕ
БЕЗОПАСНОСТЬ В БЫТОВОЙ СРЕДЕ Архитектурно-дизайнерское материаловедение
Архитектурно-дизайнерское материаловедение Организация проектной и исследовательской деятельности в школе.
Организация проектной и исследовательской деятельности в школе. Праздник алфавита Выполнила: Шарло Виктория Александровна, учитель иностранного языка
Праздник алфавита Выполнила: Шарло Виктория Александровна, учитель иностранного языка Атеросклероз коронарной артерии (атероматозная бляшка
Атеросклероз коронарной артерии (атероматозная бляшка Кушать подано! Введение
Кушать подано! Введение Статистика тема 6 абсолютные и относ
Статистика тема 6 абсолютные и относ ГОРНЫЕ ПОРОДЫ
ГОРНЫЕ ПОРОДЫ  Износ каменных конструкций
Износ каменных конструкций Урок в 7 классе по теме: «Умножение и деление степеней» Учитель: Носова Татьяна Николаевна г.Николаевск-на-Амуре, Хабаровского к
Урок в 7 классе по теме: «Умножение и деление степеней» Учитель: Носова Татьяна Николаевна г.Николаевск-на-Амуре, Хабаровского к Зв′язне мовлення. Поняття культури мовлення і спілкування
Зв′язне мовлення. Поняття культури мовлення і спілкування Механічні характеристики асинхронного двигуна
Механічні характеристики асинхронного двигуна Проектирование системы водоснабжения
Проектирование системы водоснабжения ВКР: Модернизация системы регулирования температуры нефтепродуктов подогревателя автоматизированного ПБА – 2 ЗАО
ВКР: Модернизация системы регулирования температуры нефтепродуктов подогревателя автоматизированного ПБА – 2 ЗАО Эвольвенттік іліністі құру
Эвольвенттік іліністі құру Норма права
Норма права Тепловое излучение
Тепловое излучение ПРОСТОЙ КАТЕГОРИЧЕСКИЙ СИЛЛОГИЗМ
ПРОСТОЙ КАТЕГОРИЧЕСКИЙ СИЛЛОГИЗМ Сравнение системы закупок СССР и РФ
Сравнение системы закупок СССР и РФ Алгоритмы и исполнители
Алгоритмы и исполнители