Содержание
- 2. What is Security? (cont’d.) The protection of information and its critical elements, including systems and hardware
- 3. Introduction Information security: a “well-informed sense of assurance that the information risks and controls are in
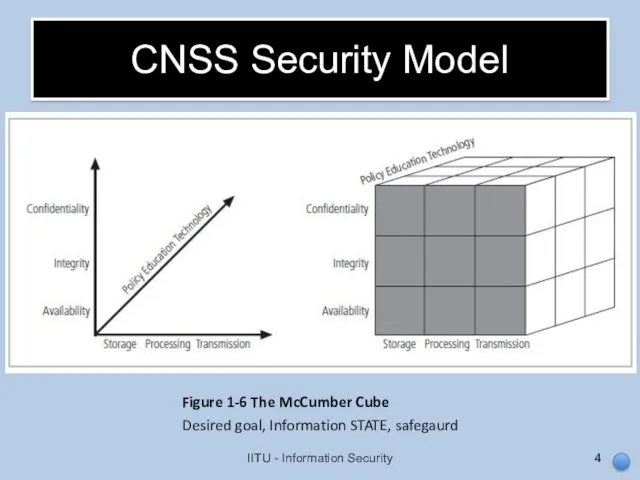
- 4. CNSS Security Model IITU - Information Security Figure 1-6 The McCumber Cube Desired goal, Information STATE,
- 5. Components of an Information System Information system (IS) is entire set of components necessary to use
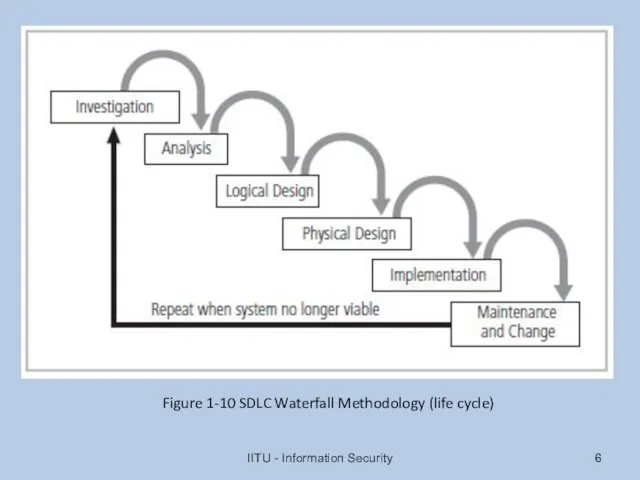
- 6. IITU - Information Security Figure 1-10 SDLC Waterfall Methodology (life cycle)
- 7. Analysis Documents from investigation phase are studied Analysis of existing security policies or programs, along with
- 8. Implementation Security solutions are acquired, tested, implemented, and tested again Personnel issues evaluated; specific training and
- 9. Summary Information security is a “well-informed sense of assurance that the information risks and controls are
- 10. EVERYTHING NEEDS A BREAK.
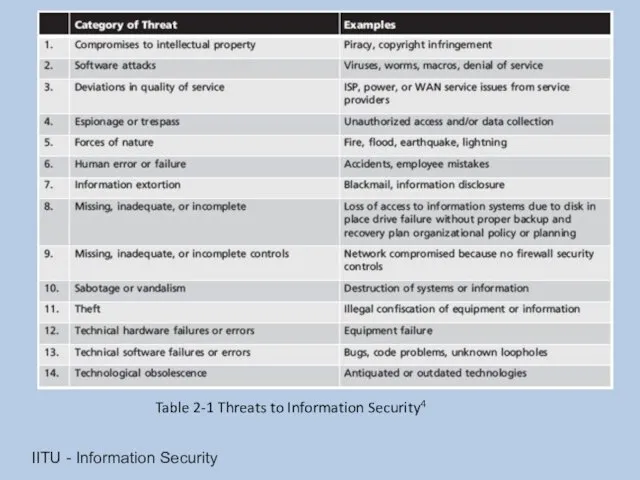
- 11. Threats Threat: an object, person, or other entity that represents a constant danger to an asset
- 12. IITU - Information Security Table 2-1 Threats to Information Security4
- 13. Deliberate Software Attacks Malicious software (malware) designed to damage, destroy, or deny service to target systems
- 14. More about previous slide Deliberate Software Attacks Deliberate software attacks occur when an individual or group
- 15. Espionage or Trespass (cont’d.) Expert hacker Develops software scripts and program exploits Usually a master of
- 16. Attacks Attacks Acts or actions that exploits vulnerability (i.e., an identified weakness) in controlled system Accomplished
- 17. Attacks (cont’d.) Types of attacks (cont’d.) Back door: gaining access to system or network using known
- 18. Attacks (cont’d.) Types of attacks (cont’d.) Denial-of-service (DoS): attacker sends large number of connection or information
- 19. Attacks (cont’d.) Types of attacks (cont’d.) Spoofing: technique used to gain unauthorized access; intruder assumes a
- 20. Attacks (cont’d.) Types of attacks (cont’d.) Sniffers: program or device that monitors data traveling over network;
- 21. Attacks (cont’d.) Types of attacks (cont’d.) Social engineering: using social skills to convince people to reveal
- 22. TAKE A DEEP BREATH
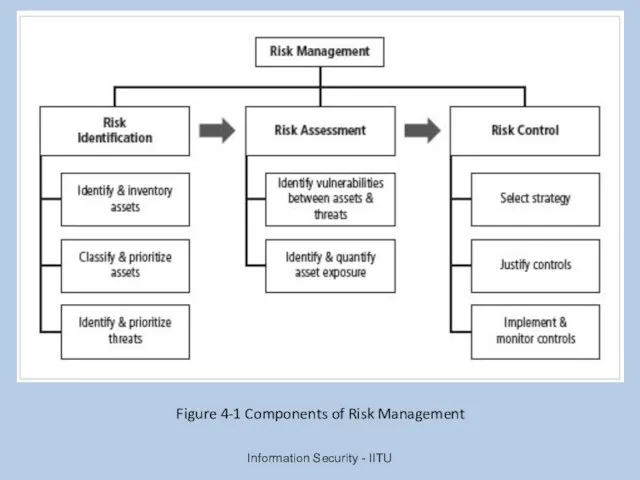
- 23. Information Security - IITU Figure 4-1 Components of Risk Management
- 24. Risk Identification Risk management involves identifying, classifying, and prioritizing an organization’s assets A threat assessment process
- 25. Risk Assessment Risk assessment evaluates the relative risk for each vulnerability Assigns a risk rating or
- 26. Information Security - IITU Table 4-10 Risk Identification and Assessment Deliverables
- 27. Access Control Access control: method by which systems determine whether and how to admit a user
- 28. Identification Identification: mechanism whereby an unverified entity that seeks access to a resource proposes a label
- 29. Authentication Authentication: the process of validating a supplicant’s purported identity Authentication factors Something a supplicant knows
- 30. Authorization Authorization: the matching of an authenticated entity to a list of information assets and corresponding
- 31. TAKE A REST
- 32. Firewalls Processing Modes Five processing modes by which firewalls can be categorized: Packet filtering Application gateways
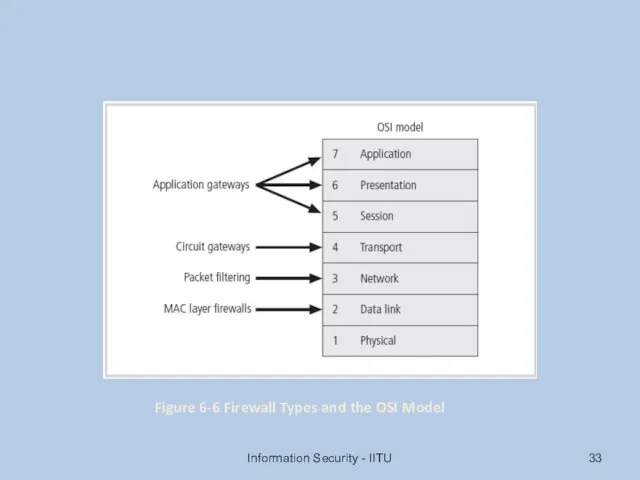
- 33. Information Security - IITU Figure 6-6 Firewall Types and the OSI Model
- 34. Firewall Architectures (cont’d.) Dual-homed host firewalls Bastion host contains two network interface cards (NICs): one connected
- 35. Firewalls Processing Modes (cont’d.) Application gateways Frequently installed on a dedicated computer; also known as a
- 36. Virtual Private Networks (VPNs) Private and secure network connection between systems; uses data communication capability of
- 37. Intrusion Detection and Prevention Systems (cont’d.) Intrusion detection: consists of procedures and systems created and operated
- 38. Honeypots, Honeynets, and Padded Cell Systems Honeypots: decoy systems designed to lure potential attackers away from
- 39. Firewall Analysis Tools Several tools automate remote discovery of firewall rules and assist the administrator in
- 40. Scanning and Analysis Tools Typically used to collect information that attacker would need to launch successful
- 41. Scanning and Analysis Tools (cont’d.) Fingerprinting: systematic survey of all of target organization’s Internet addresses collected
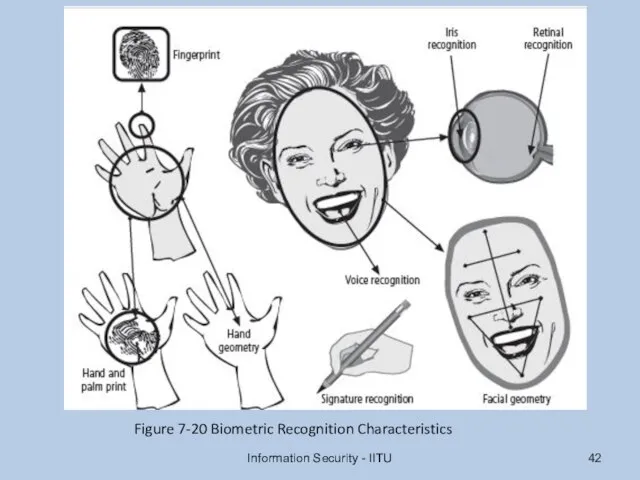
- 42. Information Security - IITU Figure 7-20 Biometric Recognition Characteristics
- 43. HAVE SOME REST
- 44. Cryptology: science of encryption; combines cryptography and cryptanalysis Cryptography: process of making and using codes to
- 45. Substitution Cipher Substitute one value for another Monoalphabetic substitution: uses only one alphabet Polyalphabetic substitution: more
- 46. Information Security - IITU Table 8-2 The Vigenère Square
- 47. Cryptographic Algorithms Often grouped into two broad categories, symmetric and asymmetric Today’s popular cryptosystems use hybrid
- 48. Symmetric Encryption (cont’d.) Data Encryption Standard (DES): one of most popular symmetric encryption cryptosystems 64-bit block
- 49. Asymmetric Encryption Also known as public-key encryption Uses two different but related keys Either key can
- 50. Asymmetric Encryption Also known as public-key encryption Uses two different but related keys Either key can
- 51. Symmetric Encryption (cont’d.) Data Encryption Standard (DES): one of most popular symmetric encryption cryptosystems 64-bit block
- 52. Symmetric Encryption Uses same “secret key” to encipher and decipher message Encryption methods can be extremely
- 53. Securing Internet Communication with S-HTTP and SSL Secure Socket Layer (SSL) protocol: uses public key encryption
- 54. Securing e-mail with S/MIME, PEM, and PGP Secure Multipurpose Internet Mail Extensions (S/MIME): builds on Multipurpose
- 55. Securing Web transactions with SET, SSL, and S-HTTP Secure Electronic Transactions (SET): developed by MasterCard and
- 56. Securing Wireless Networks with WEP and WPA Wired Equivalent Privacy (WEP): early attempt to provide security
- 57. Steganography Process of hiding information Has been in use for a long time Most popular modern
- 58. DO YOU WANT A CUP OF COFFEE?!
- 59. Introduction Physical security addresses design, implementation, and maintenance of countermeasures that protect physical resources of an
- 60. Uninterruptible power supply (UPS) Uninterruptible power supply (UPS) In case of power outage, UPS is backup
- 61. Heating, Ventilation, and Air Conditioning Areas within heating, ventilation, and air conditioning (HVAC) systems that can
- 62. Physical Security Controls (cont’d.) Electronic Monitoring Records events where other types of physical controls are impractical
- 63. Summary Threats to information security that are unique to physical security Key physical security considerations in
- 64. Introduction SecSDLC implementation phase is accomplished through changing configuration and operation of organization’s information systems Implementation
- 65. Developing the Project Plan Creation of project plan can be done using work breakdown structure (WBS)
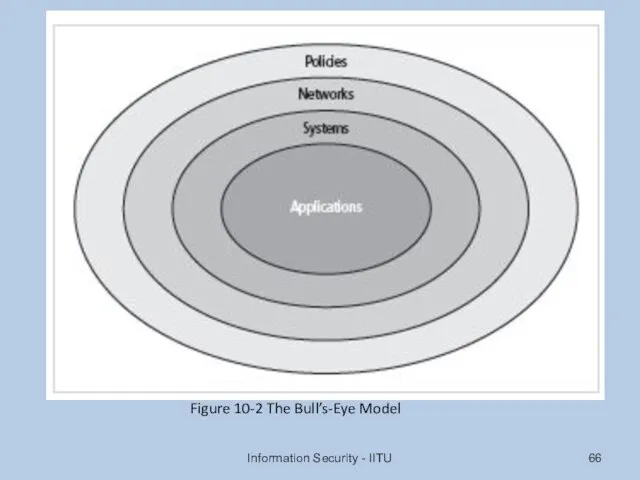
- 66. Information Security - IITU Figure 10-2 The Bull’s-Eye Model
- 67. Positioning and Staffing the Security Function The security function can be placed within: IT function Physical
- 68. Positioning and Staffing the Security Function The security function can be placed within: IT function Physical
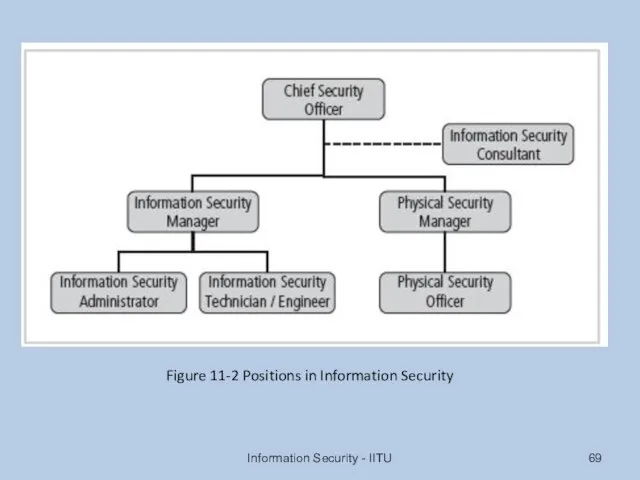
- 69. Information Security - IITU Figure 11-2 Positions in Information Security
- 70. Staffing the Information Security Function (cont’d.) Chief Information Security Officer (CISO or CSO) Top information security
- 71. Staffing the Information Security Function (cont’d.) Security manager Accountable for day-to-day operation of information security program
- 72. Staffing the Information Security Function (cont’d.) Security technician Technically qualified individuals tasked to configure security hardware
- 73. IT MIGHT BE A BAD DAY, NOT A BAD LIFE
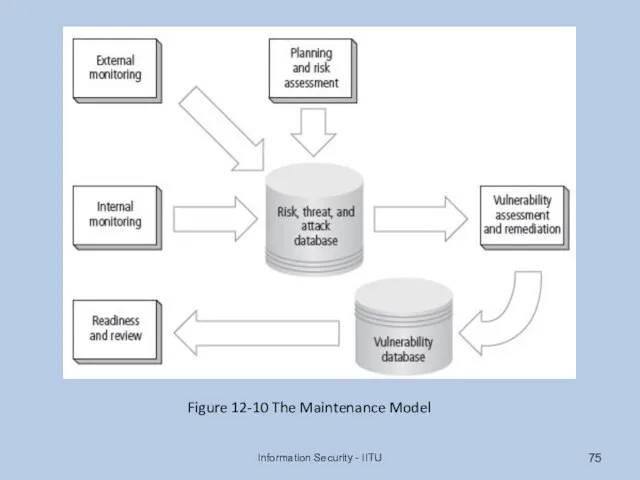
- 74. The Security Maintenance Model Designed to focus organizational effort on maintaining systems Recommended maintenance model based
- 75. Information Security - IITU Figure 12-10 The Maintenance Model
- 76. Monitoring the External Environment Objective to provide early awareness of new threats, threat agents, vulnerabilities, and
- 77. Monitoring the Internal Environment Maintain informed awareness of state of organization’s networks, systems, and security defenses
- 78. Planning and Risk Assessment Primary objective is to keep lookout over entire information security program Accomplished
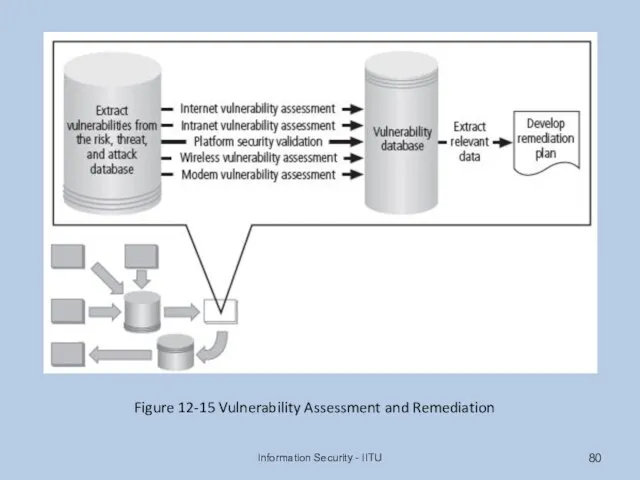
- 79. Vulnerability Assessment and Remediation Primary goal: identification of specific, documented vulnerabilities and their timely remediation Accomplished
- 80. Information Security - IITU Figure 12-15 Vulnerability Assessment and Remediation
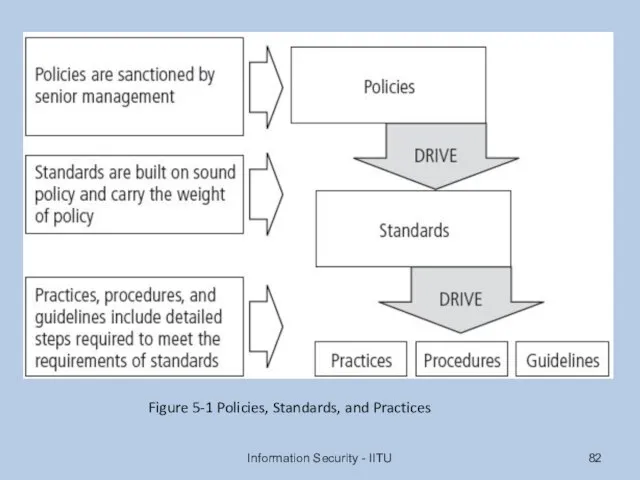
- 81. Definitions Policy: course of action used by organization to convey instructions from management to those who
- 82. Information Security - IITU Figure 5-1 Policies, Standards, and Practices
- 83. The ISO 27000 Series One of the most widely referenced and often discussed security models Framework
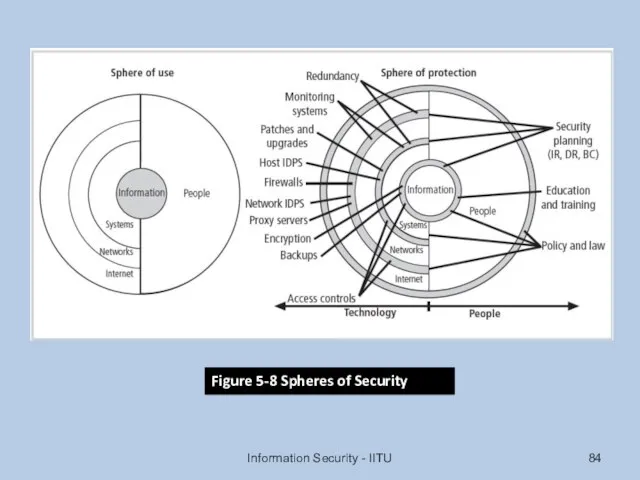
- 84. Information Security - IITU Figure 5-8 Spheres of Security
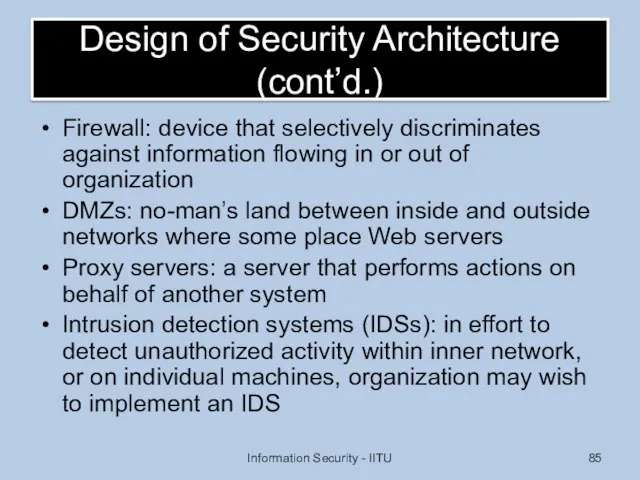
- 85. Design of Security Architecture (cont’d.) Firewall: device that selectively discriminates against information flowing in or out
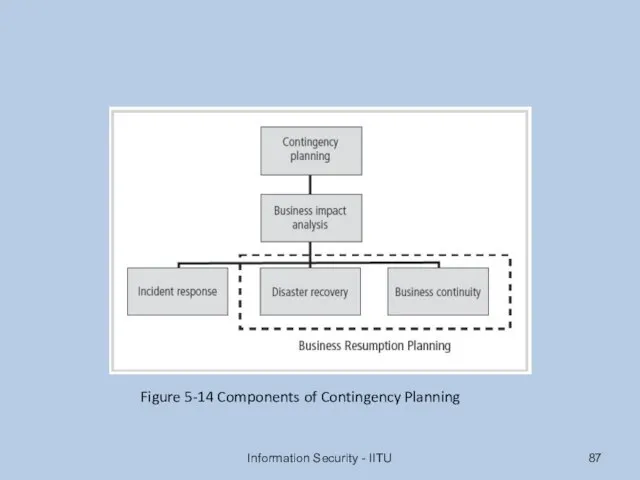
- 86. Continuity Strategies Incident response plans (IRPs); disaster recovery plans (DRPs); business continuity plans (BCPs) Primary functions
- 87. Information Security - IITU Figure 5-14 Components of Contingency Planning
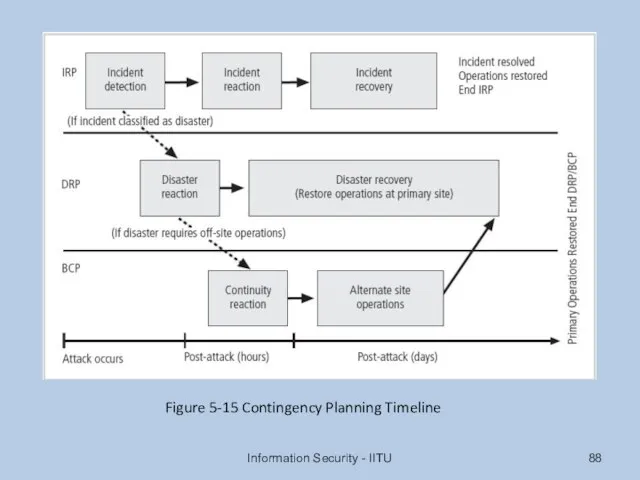
- 88. Information Security - IITU Figure 5-15 Contingency Planning Timeline
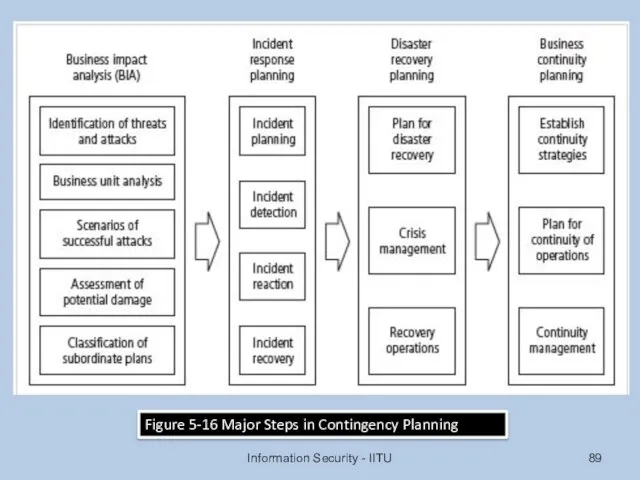
- 89. Information Security - IITU Figure 5-16 Major Steps in Contingency Planning
- 91. Скачать презентацию






























































 Контекстная реклама
Контекстная реклама Основы программирования на языке Python
Основы программирования на языке Python Инструкция по созданию презентаций
Инструкция по созданию презентаций Программное обеспечение ПК
Программное обеспечение ПК Bash programming. CSCI 330 the unix system
Bash programming. CSCI 330 the unix system Измерение информации. Объёмный подход
Измерение информации. Объёмный подход Требования к программному обеспечению
Требования к программному обеспечению Безопасный интернет
Безопасный интернет Практикум по теме персональный компьютер
Практикум по теме персональный компьютер Текстовые редакторы
Текстовые редакторы New words 2017
New words 2017 Информационная безопасность Урок медиабезопасности подготовила Лифанова Н.В., классный руководитель 10 класса МОУ Космынинска
Информационная безопасность Урок медиабезопасности подготовила Лифанова Н.В., классный руководитель 10 класса МОУ Космынинска Ашық тәрбие сағаты
Ашық тәрбие сағаты Презентация "История развития криптографии" - скачать презентации по Информатике
Презентация "История развития криптографии" - скачать презентации по Информатике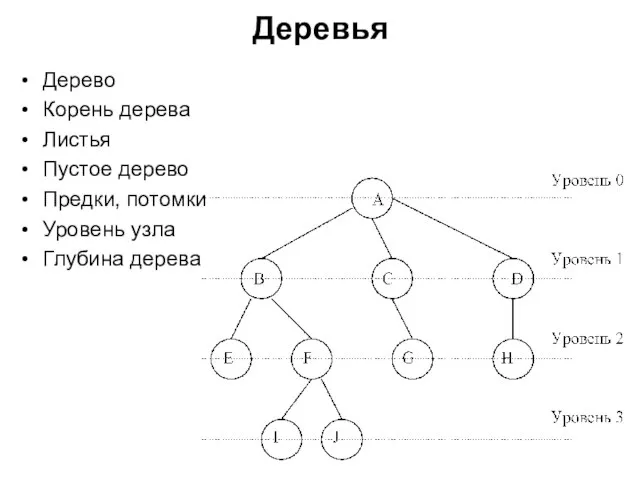 Деревья. Двоичные (бинарные) деревья
Деревья. Двоичные (бинарные) деревья EasyEdu - наш новый органайзер
EasyEdu - наш новый органайзер 4SA313 - Bezpečnost informačních systémů
4SA313 - Bezpečnost informačních systémů ППС-2017, Лекция №2(3)
ППС-2017, Лекция №2(3) Процессоры Типы процессоров и их характеристики
Процессоры Типы процессоров и их характеристики  Виды ссылок в Excel
Виды ссылок в Excel Microsoft Office бағдарламасында құжат құру
Microsoft Office бағдарламасында құжат құру Поисковые системы интернета Выполнила: Корпачева Лена 11б класс
Поисковые системы интернета Выполнила: Корпачева Лена 11б класс  Компьютерный сервис. Комплексные пакеты настроек смартфонов и планшетов
Компьютерный сервис. Комплексные пакеты настроек смартфонов и планшетов Общая характеристика социальных сервисов Web
Общая характеристика социальных сервисов Web Презентация "Моделирование и формализация 9 класс" - скачать презентации по Информатике
Презентация "Моделирование и формализация 9 класс" - скачать презентации по Информатике Основная идея
Основная идея Уязвимости информации и информационных систем. ОИТ. Лекция 4
Уязвимости информации и информационных систем. ОИТ. Лекция 4 Состав и действия объекта (3 класс)
Состав и действия объекта (3 класс)