Содержание
- 2. RISK ASSESSMENT IDENTIFICATION OF RISKS FOR SECURITY PURPOSE RISK = THREAT THREATS ALWAYS TAKEN INTO CONSIDERATION
- 3. RISK ASSESSMENT 2. DEFINE METHODOLOGY DEFINE THE PARAMETERS / CRITERIA SCALE THE PARAMETERS / CRITERIA SET
- 4. RISK ASSESSMENT 4. POSSIBLE METHODOLOGY FOR ISPS PARAMETERS / CRITERIA AND SCALING: PROBABILITY (P) = LIKELYHOOD
- 5. RISK ASSESSMENT 4. POSSIBLE METHODOLOGY FOR ISPS R = P x C x V TERRORISM=[REMOTE PROBABILITY
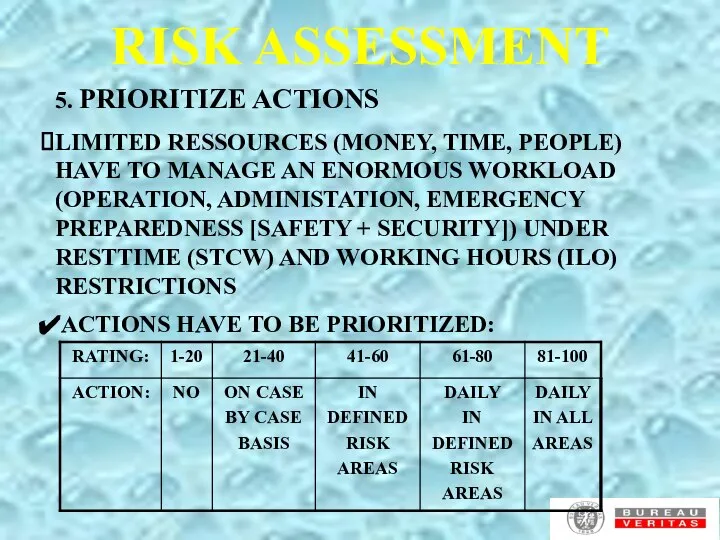
- 6. RISK ASSESSMENT 5. PRIORITIZE ACTIONS LIMITED RESSOURCES (MONEY, TIME, PEOPLE) HAVE TO MANAGE AN ENORMOUS WORKLOAD
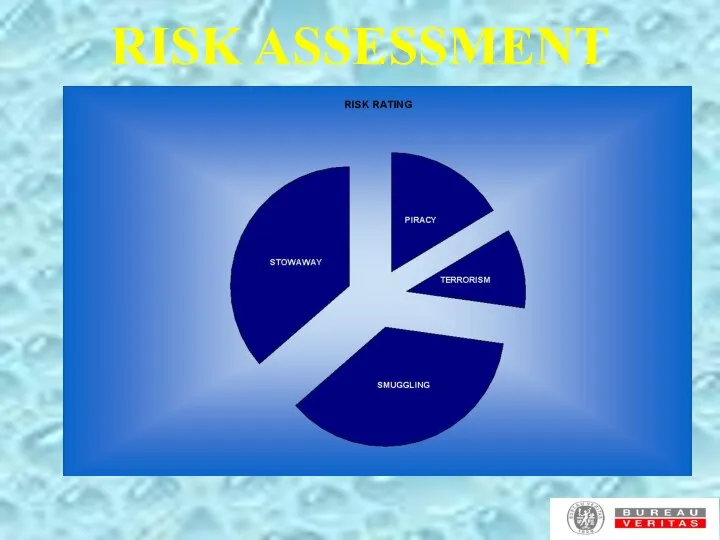
- 7. RISK ASSESSMENT
- 9. Скачать презентацию




 Аттестационная работа. Влияние паров вейпа, электронной сигареты на живые организмы
Аттестационная работа. Влияние паров вейпа, электронной сигареты на живые организмы Физическая культура и закаливание
Физическая культура и закаливание Взрыв и его поражающие факторы
Взрыв и его поражающие факторы Не вреди своему здоровью ! Вредные привычки
Не вреди своему здоровью ! Вредные привычки Наркотики и их влияние на развитие полноценной личности
Наркотики и их влияние на развитие полноценной личности Антропометрические требования в эргономике. Базы отсчета и расчет параметров рабочего места. Эргономический расчет
Антропометрические требования в эргономике. Базы отсчета и расчет параметров рабочего места. Эргономический расчет Пожарная безопасность. Конкурс
Пожарная безопасность. Конкурс Сели. Причины возникновения
Сели. Причины возникновения Здоровый образ жизни
Здоровый образ жизни Энергетические напитки
Энергетические напитки Безпека на дорозі. Правила дорожнього руху. (2 клас)
Безпека на дорозі. Правила дорожнього руху. (2 клас) Безопасность жизнедеятельности. Защита населения и территорий в чрезвычайных ситуациях
Безопасность жизнедеятельности. Защита населения и территорий в чрезвычайных ситуациях Основы здорового образа жизни
Основы здорового образа жизни Условия труда работников
Условия труда работников Занятие по внеурочной деятельности Береги зрение смолоду! 7 класс
Занятие по внеурочной деятельности Береги зрение смолоду! 7 класс Торнадо
Торнадо Вред курения
Вред курения Памятка по пожарной безопасности для РПСС
Памятка по пожарной безопасности для РПСС Тұрғын үй маңызды әлеуметтік-гигиеналық мәселе болып саналады
Тұрғын үй маңызды әлеуметтік-гигиеналық мәселе болып саналады Debating on terrorism
Debating on terrorism Участники дорожного движения
Участники дорожного движения Формирование понятия пожарная безопасность. Овладение знаниями и умениями при действиях в чрезвычайных ситуациях
Формирование понятия пожарная безопасность. Овладение знаниями и умениями при действиях в чрезвычайных ситуациях Курительные смеси
Курительные смеси Электробезопасность. Действие электрического тока на человека
Электробезопасность. Действие электрического тока на человека Гигиенические аспекты противорадиационной защиты
Гигиенические аспекты противорадиационной защиты Две классификации fake news. Можно ли распознать фейк и как это сделать
Две классификации fake news. Можно ли распознать фейк и как это сделать Общие положения ПДД 2016
Общие положения ПДД 2016 Правда про табакокурение
Правда про табакокурение